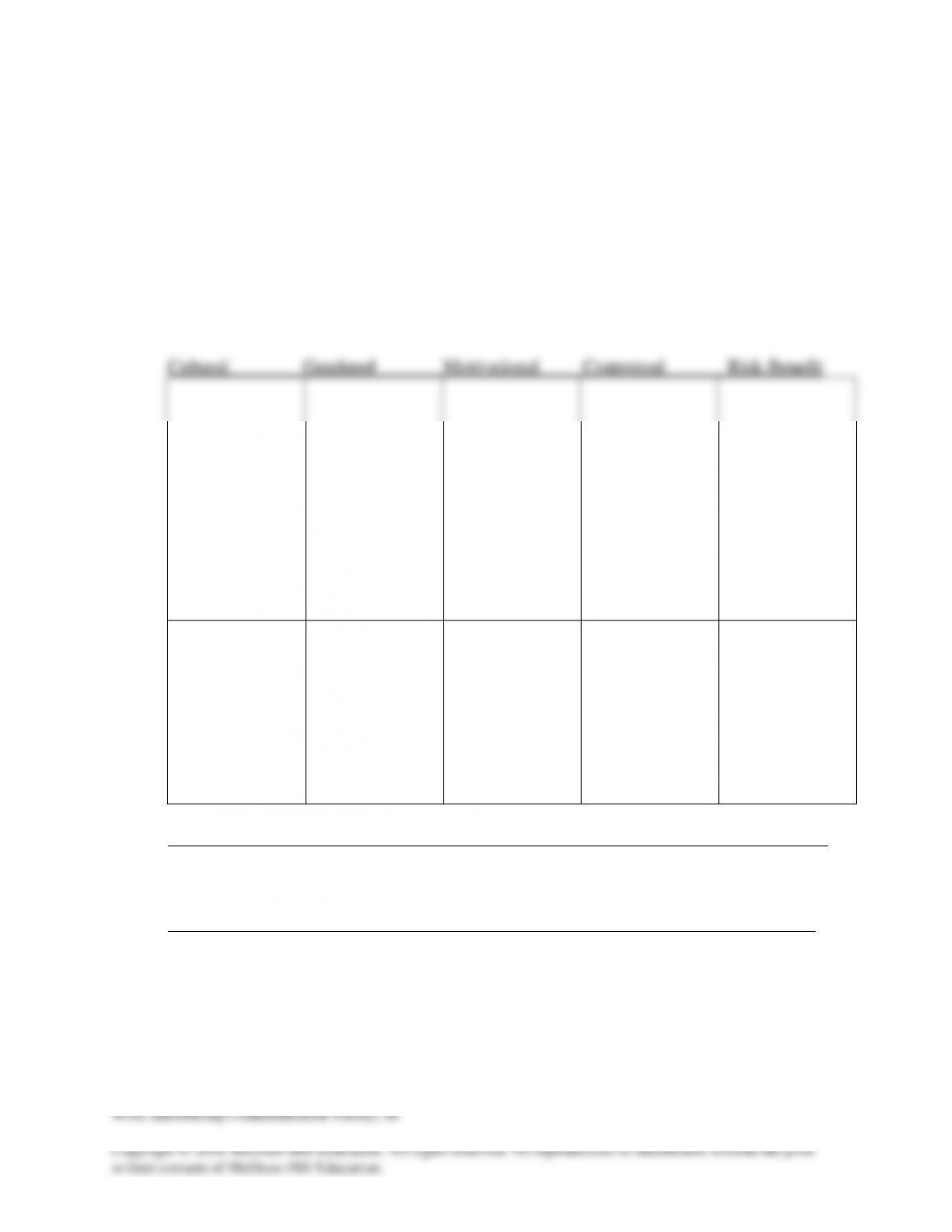
5
Chapter 12: Communication Privacy Management Theory
West, Introducing Communication Theory, 6e
o In any event, turbulence will ensue when “expectations for privacy management
are unfulfilled” (Petronio, 2010, p. 182).
V. Integration, Critique, and Closing
• Communication Privacy Management Theory has enjoyed significant attention from
scholars in communication as well as from those in other disciplines.
• The theory appears to resonate because its boundaries and boundary rules guide all sorts of
behaviors in all types of relationships.
A. Logical Consistency
• Some critics have observed that CPM uses the term dialectic inaccurately, claiming to
be dialectic in nature when it’s really based on dualistic thinking.
• Petronio (2002) responds to this criticism by noting that perhaps the accusation of
dualistic thinking comes from the use of the terms balance and equilibrium in the early
original]). Thus, Petronio argues that it is legitimate to call CPM Theory dialectical in
nature.
B. Utility
• Communication Privacy Management Theory has much promise of utility.
• It offers an explanation for the delicate process of coordination disclosing and
concealing that people perform continually in their relationships with others.
C. Heurism
• Communication Privacy Management Theory demonstrates heurism because it has been
utilized as a framework in a variety of situations, including romantic relationships (e.g.,
Nichols, 2012), military families (Owlett, Richards, Wilson, DeFreese, and Roberts,
2015), academic advising (e.g., Thompson, Petronio, and Braithwaite, 2012), and health
care (e.g., Romo, 2012; Petronio and Sargent, 2011).
• One promising and exciting area where CPM has been investigated is with blogging and
Facebook. Jeff Child (e.g., Child and Petronio, 2011; Child and Starcher, 2016; Child
and Westerman, 2013; Child, Petronio, Agyeman-Budu, and Westerman, 2011) has