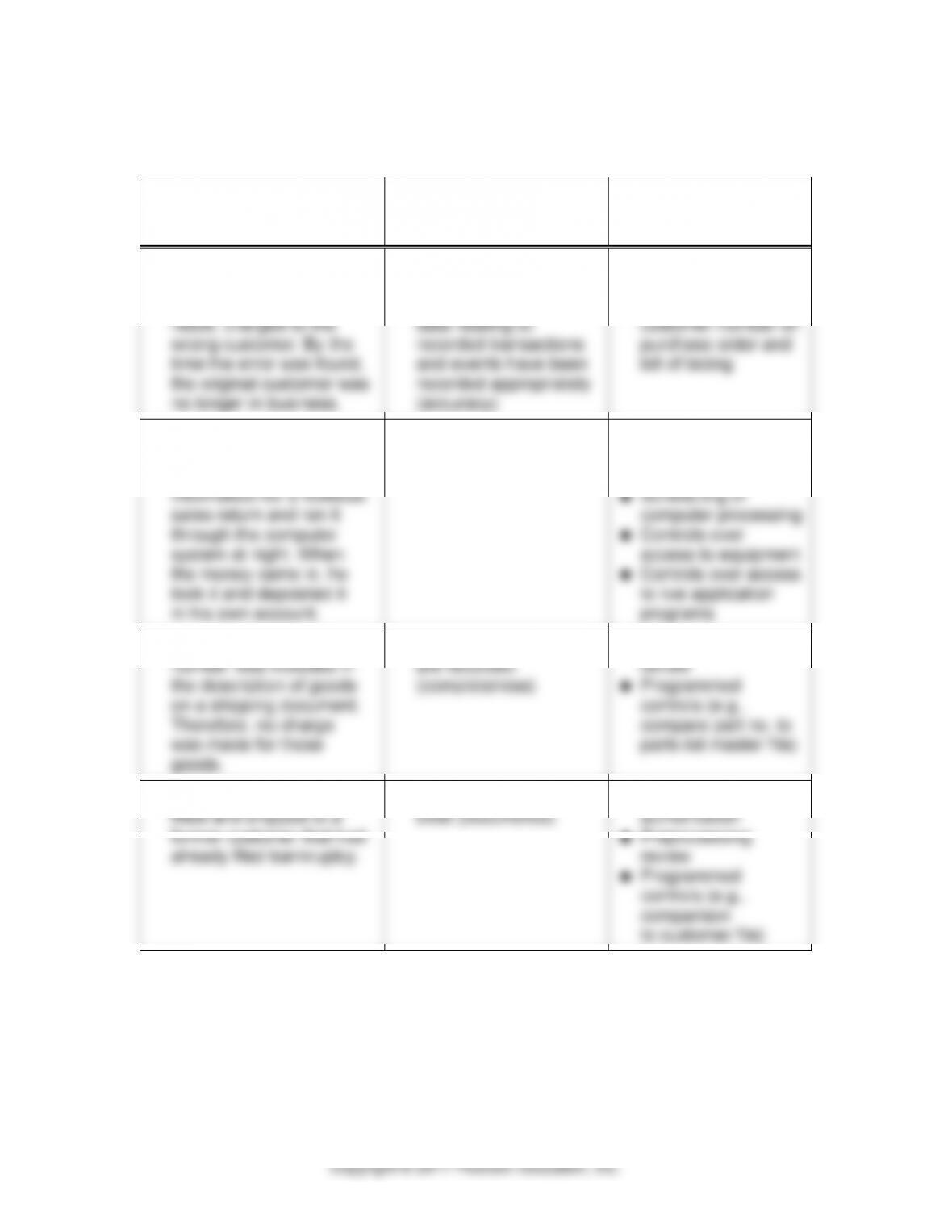
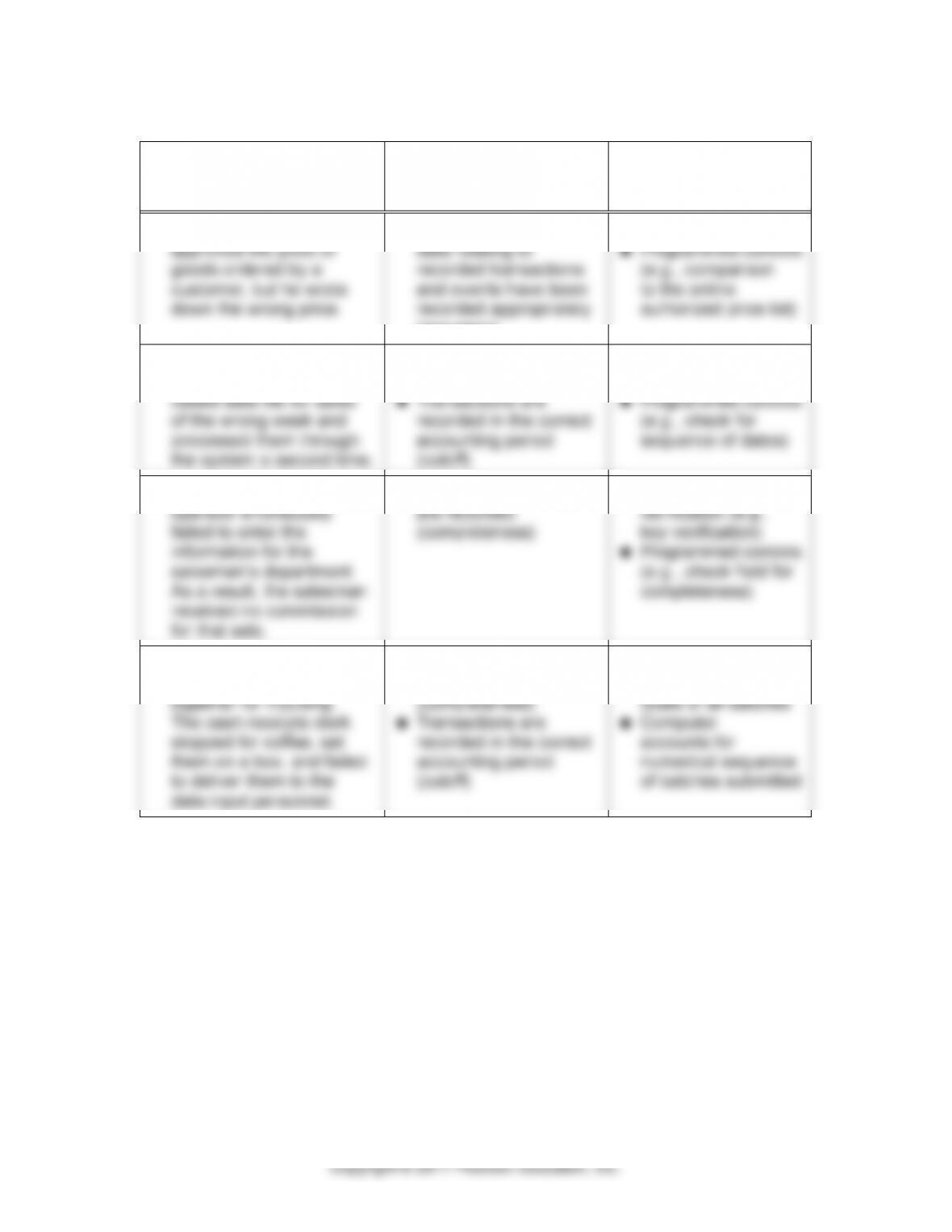
11-16
11-29 (continued)
the sales function.
For larger IT functions, programmers are split into subgroups
with some programmers only authorized to address programming
2. Strengthening IT general controls over program changes, restricting
access to live software versions, and enhancing segregation of
duties will significantly reduce the programmer’s ability to make
unauthorized changes to software as was done at Wilcoxon Sports.
change in software without someone’s knowledge. If the
librarian only accepts revised programs for properly authorized
If programmer functions are separated among programmers
sales application and the operating system software.
11-30
a. The strengths of Hardwood Lumber Company’s computerized accounting
system include the following:
Separate departments for systems programming, applications
programming, operations, and data control.
CHANGE or RUN capabilities.
The computer room is locked and requires a key-card for access
program files.
application software program files.
Data control clerks have no access to software program files.