add 192.168.10.2 192.168.13.2 esp 0x301 -E 3des-cbc ------>8
0xf6ddb555acfd9d77b03ea3843f26532558fe8eb5573965df; ------>9
#Security Policies ------>10
spdadd 192.168.10.2 192.168.13.2 any -P in ipsec ------>11
esp/transport//require; ------>12
Setkey.conf file on 192.168.13.2
The setkey file has two blocks in it and the first part deals with configuring the IPSec
security associations while the second part is used for configuring the Security Policies. We first
flushed the previous configuration settings( if any) and configured the Security Association Database
parameters as follows.
Lines 8 and 9 contain the required configuration settings for the SA in the other direction.
The encryption key for this SA is different from the one used for the previous SA.
We configured the Security Policies in the following way
Using the keyword spdadd we specified the two end hosts which would be taking part in
the IPSec connection and gave the SA a direction (IN since the configuration file is on M3). Also we
specified that the SA should be set up using the transport mode and the ESP protocol. This is shown in
Lines 11 and 12. Lines 13 and 14 specify the other direction (OUT).
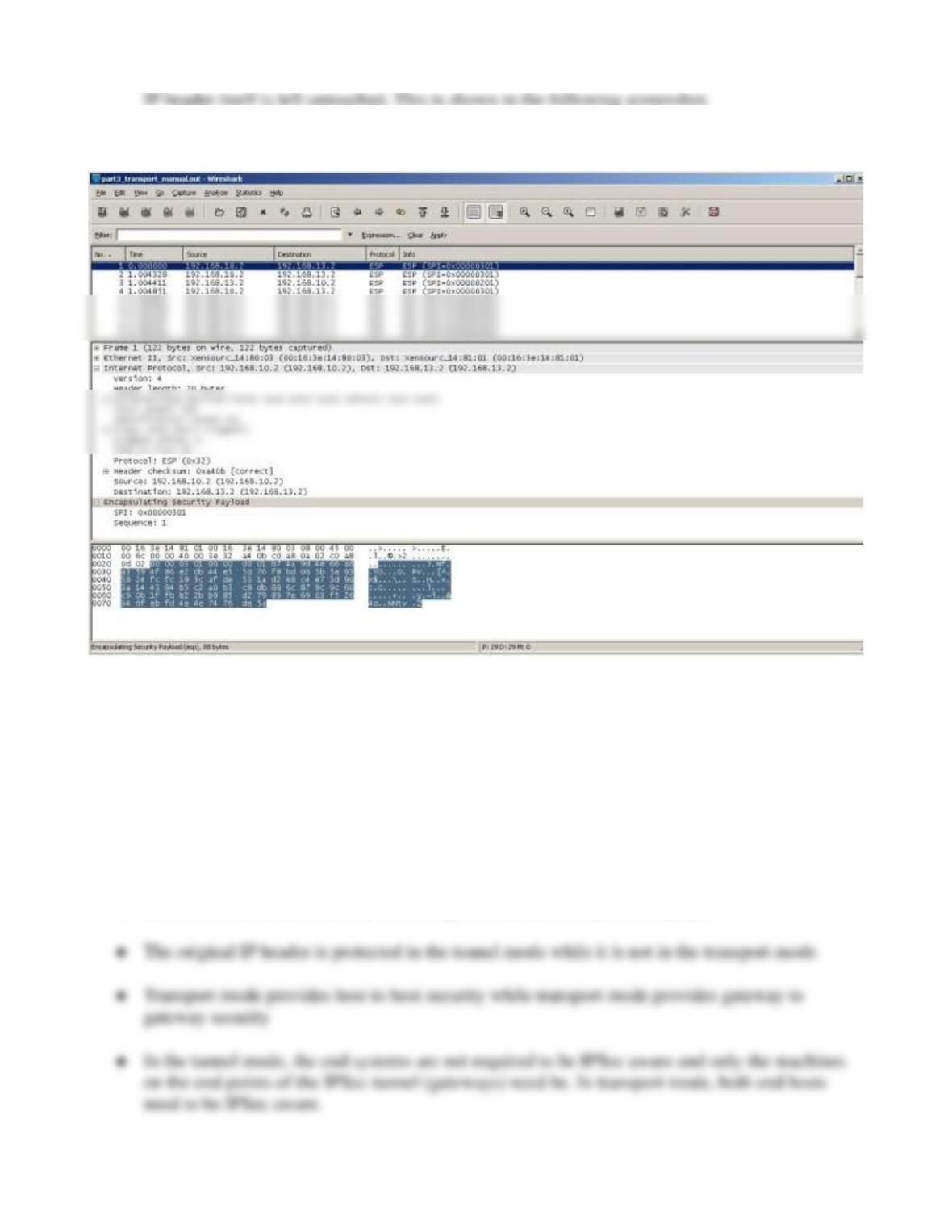
2. IPSec provides only confidentiality in this case. We are neither using AH nor using
3. No,the IP header is not encrypted. This is because we are using the Transport mode which runs