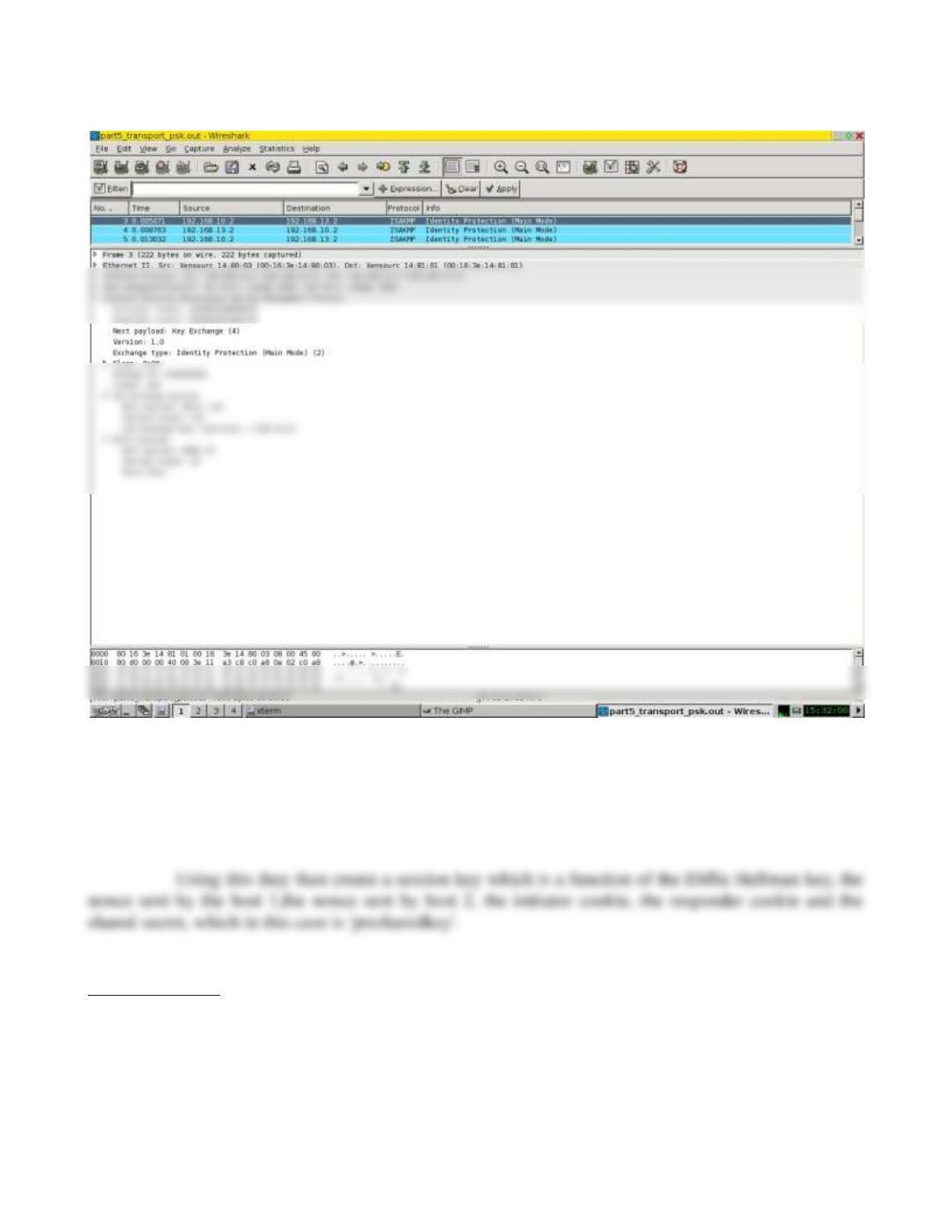
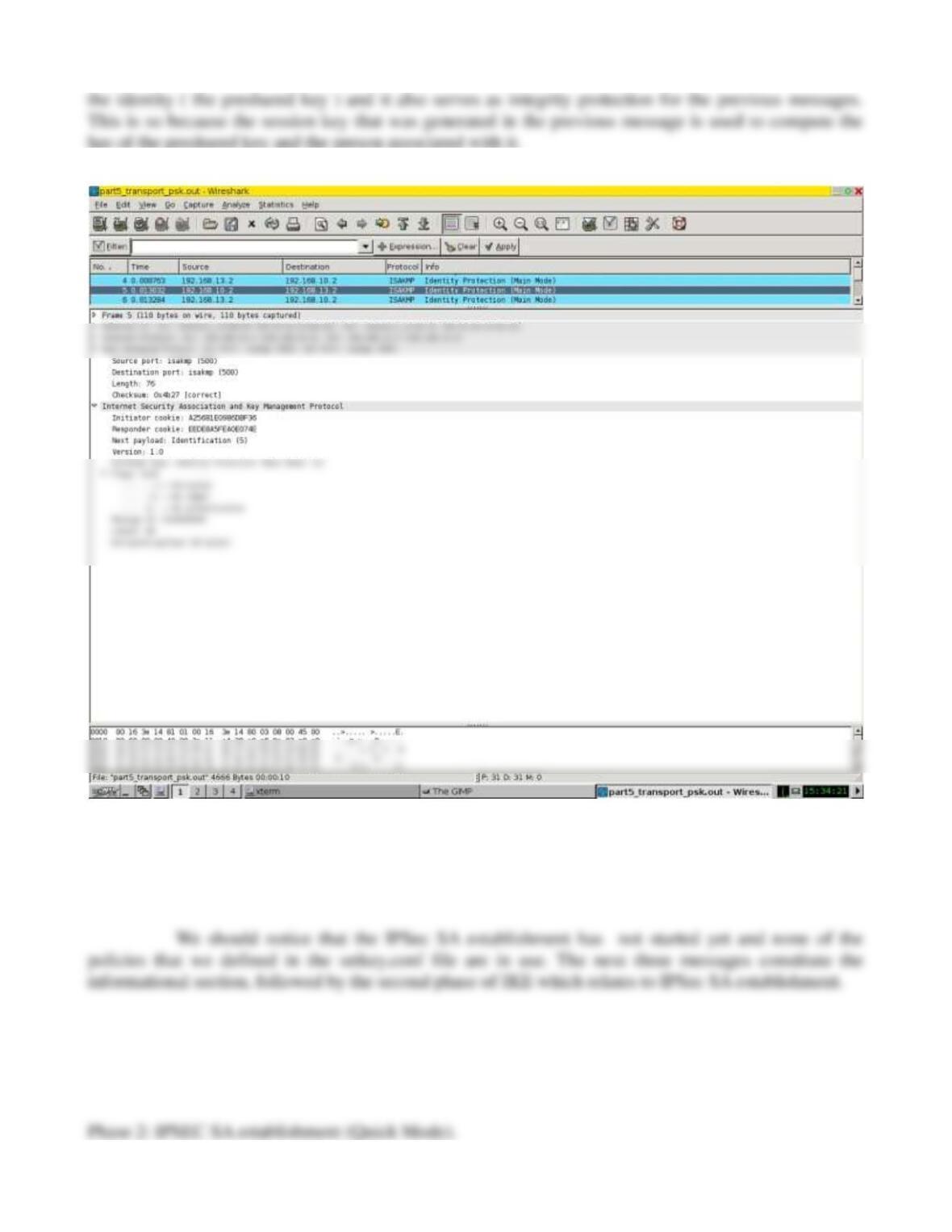
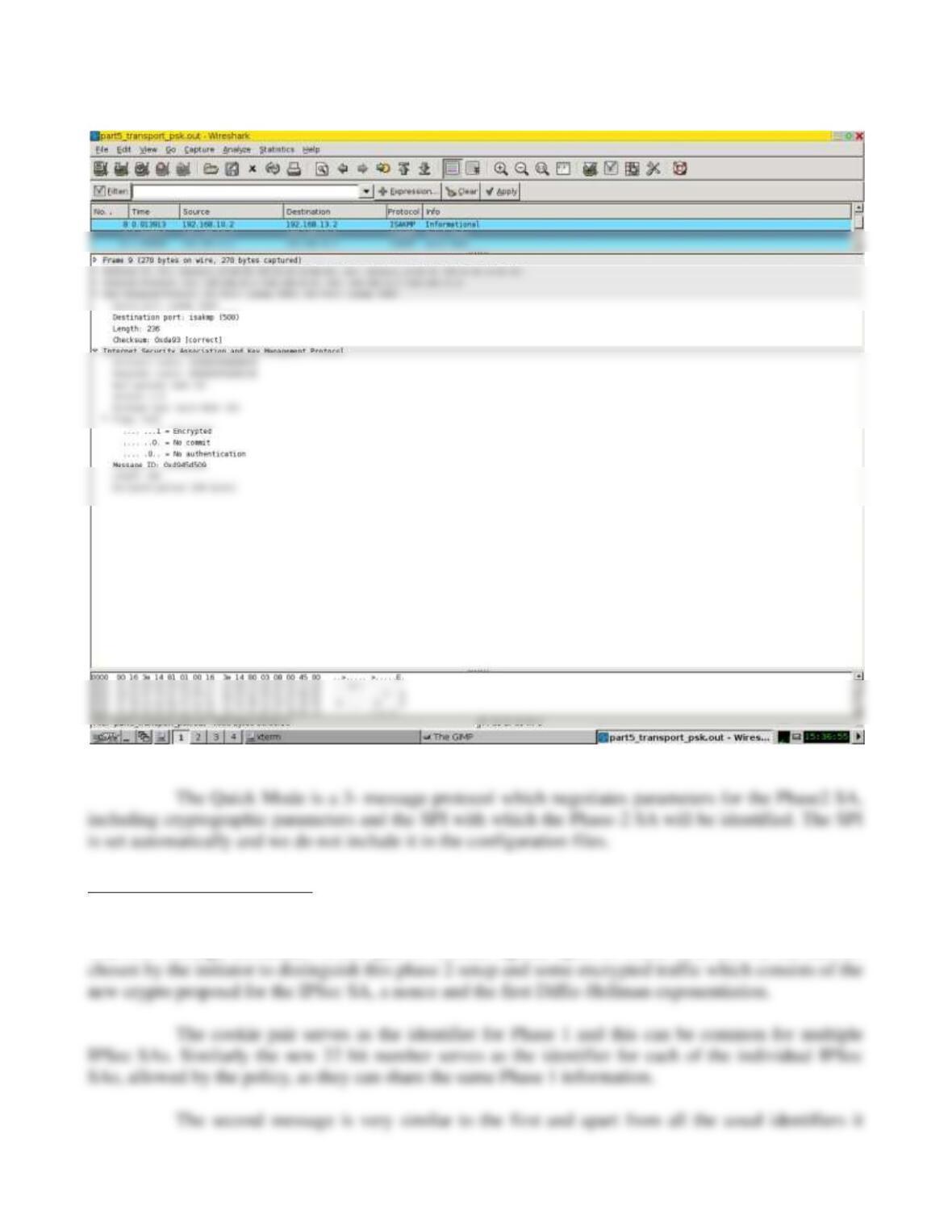
4. In preshared keys method, the keys is a function of the preshared key, sender and responder
cookies, the diffie hellman key, and the nonces while it is a function of the nonces and the diffie
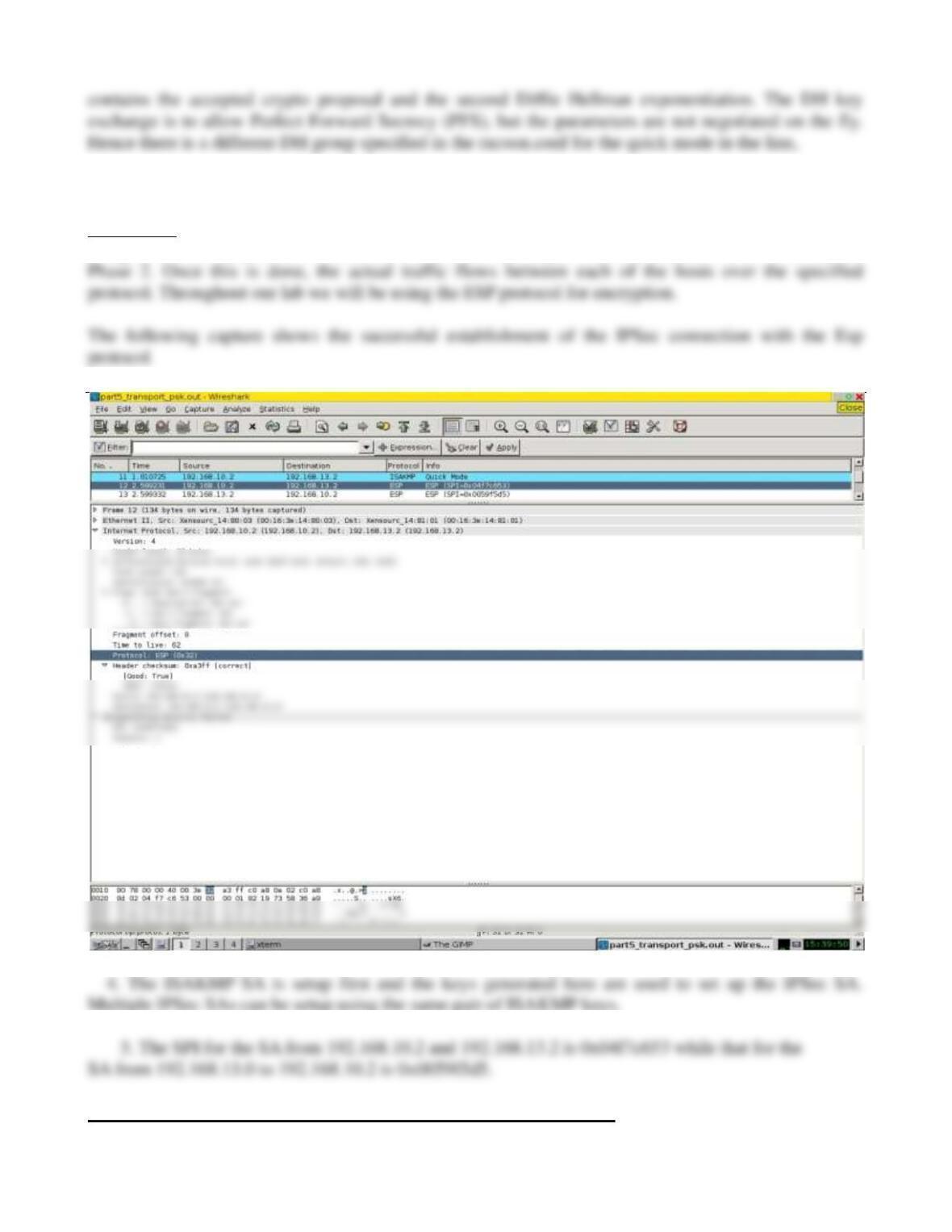
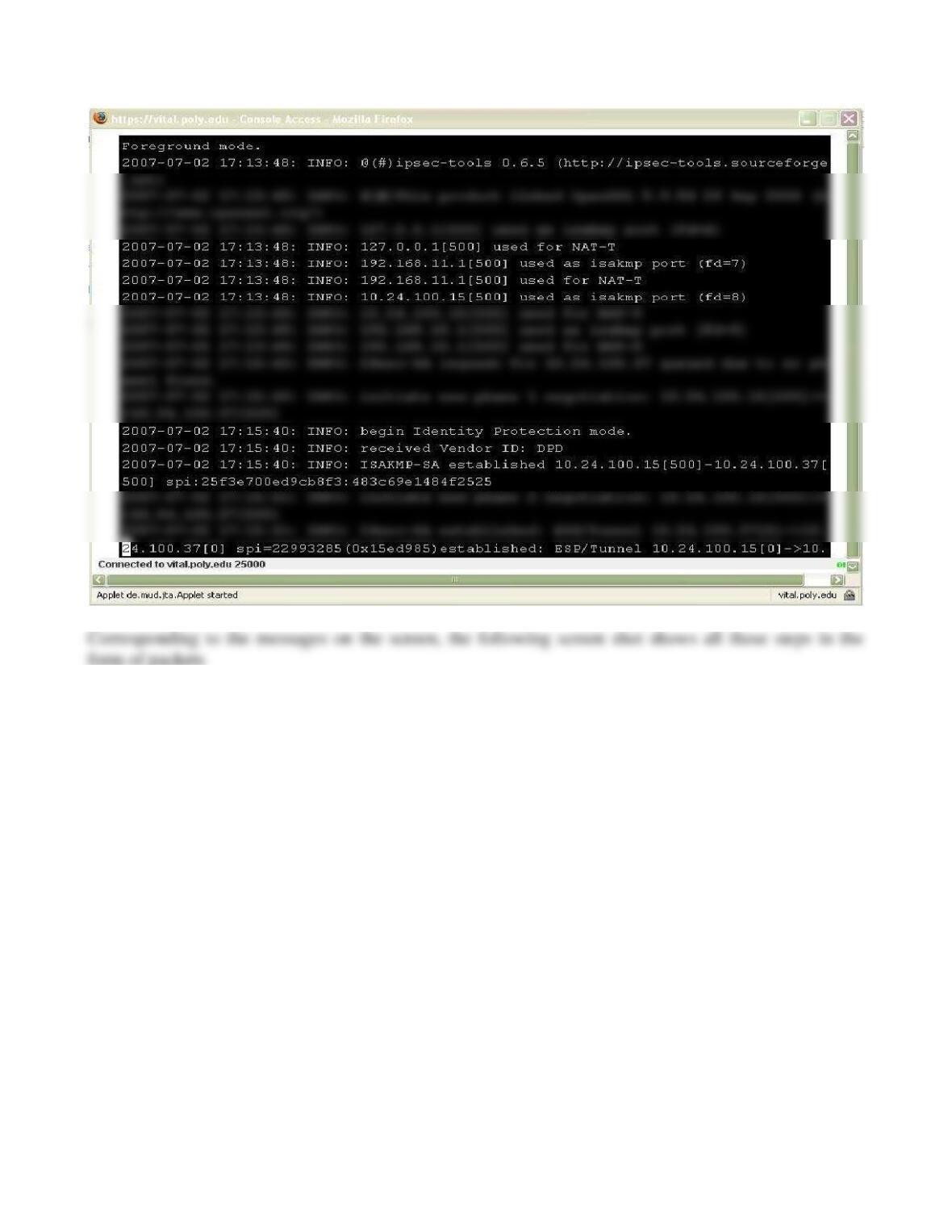
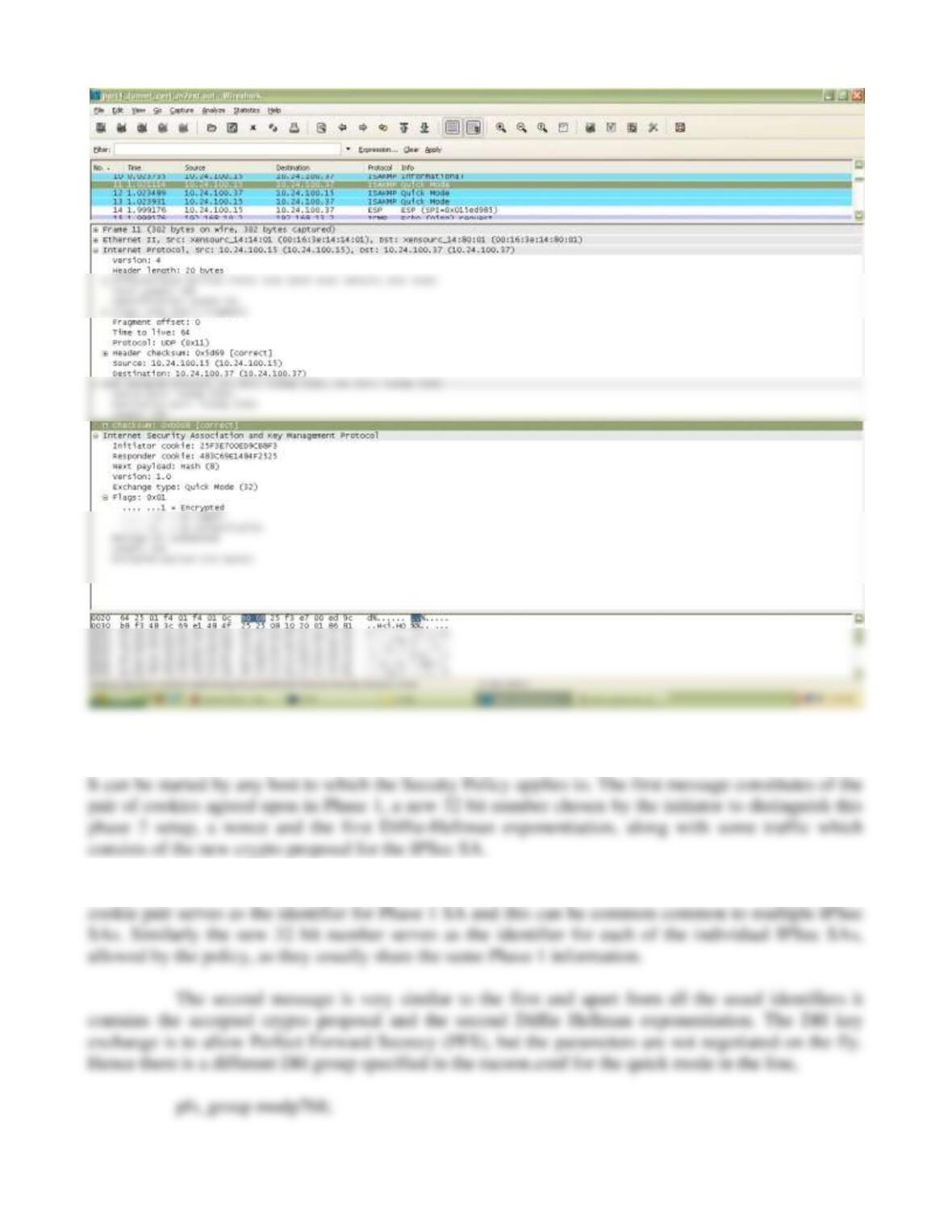
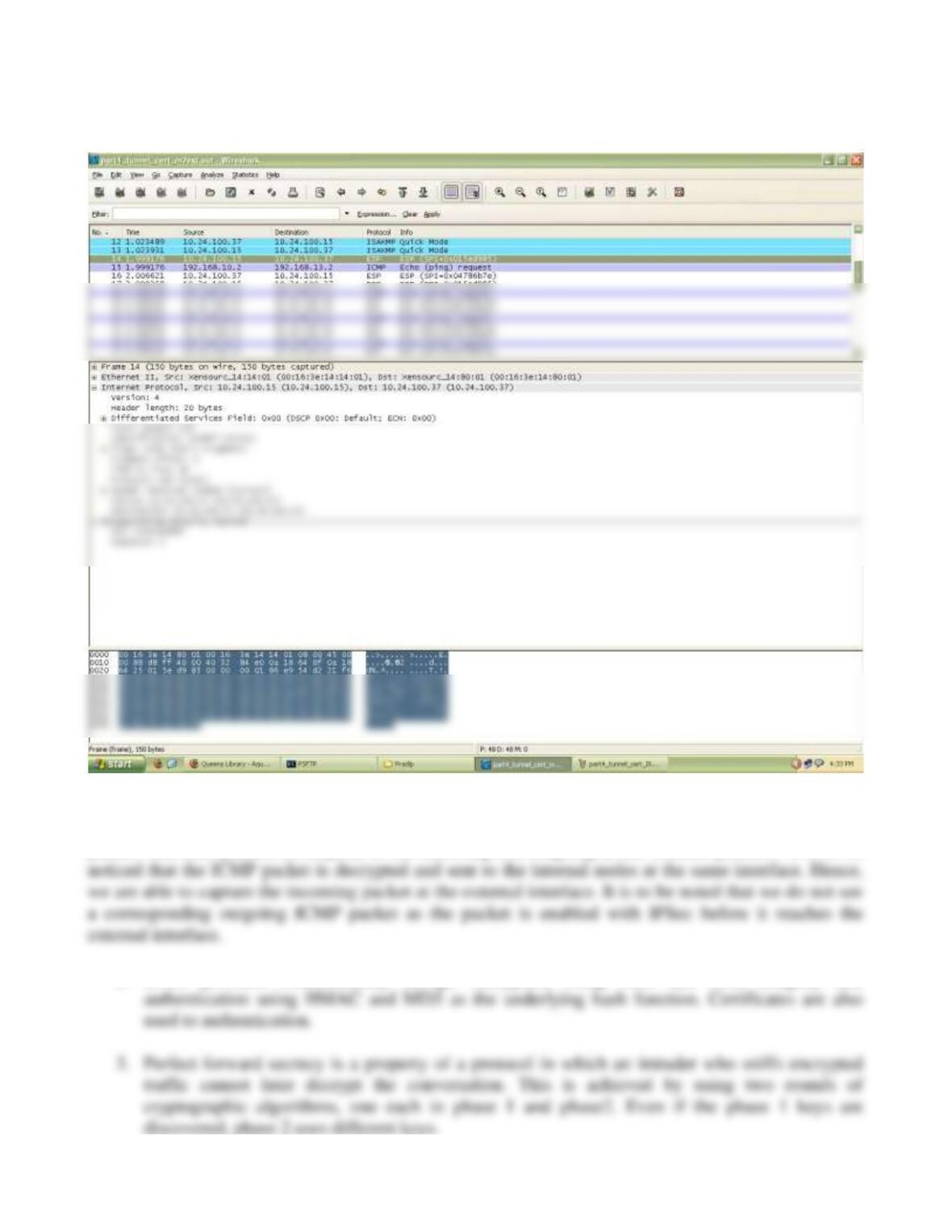
5. SPI for the SA between 10.24.100.15 to 10.24.100.37 is 0x015ed985 while that for the
SA between 10.24.100.24 is 0x04786b7e.
6. No the same configuration will not protect traffic flowing between the other two internal hosts.
This is because, although, the other two hosts have the same respective gateways, they lie in
Note:
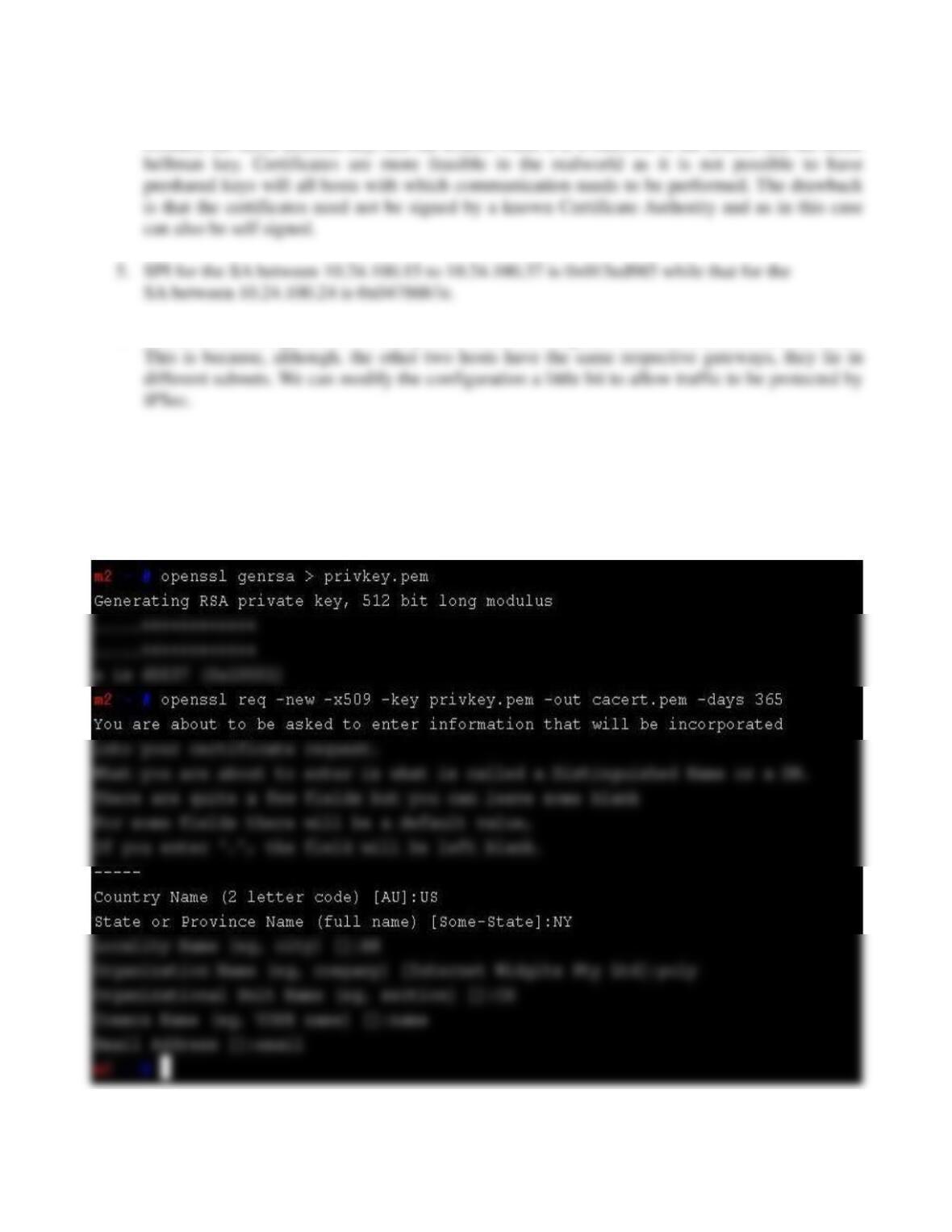
The private keys were created using Openssl's genrsa command. Similarly the certificates were also
created using other OpenSSL commands. The following screenshot shows this.