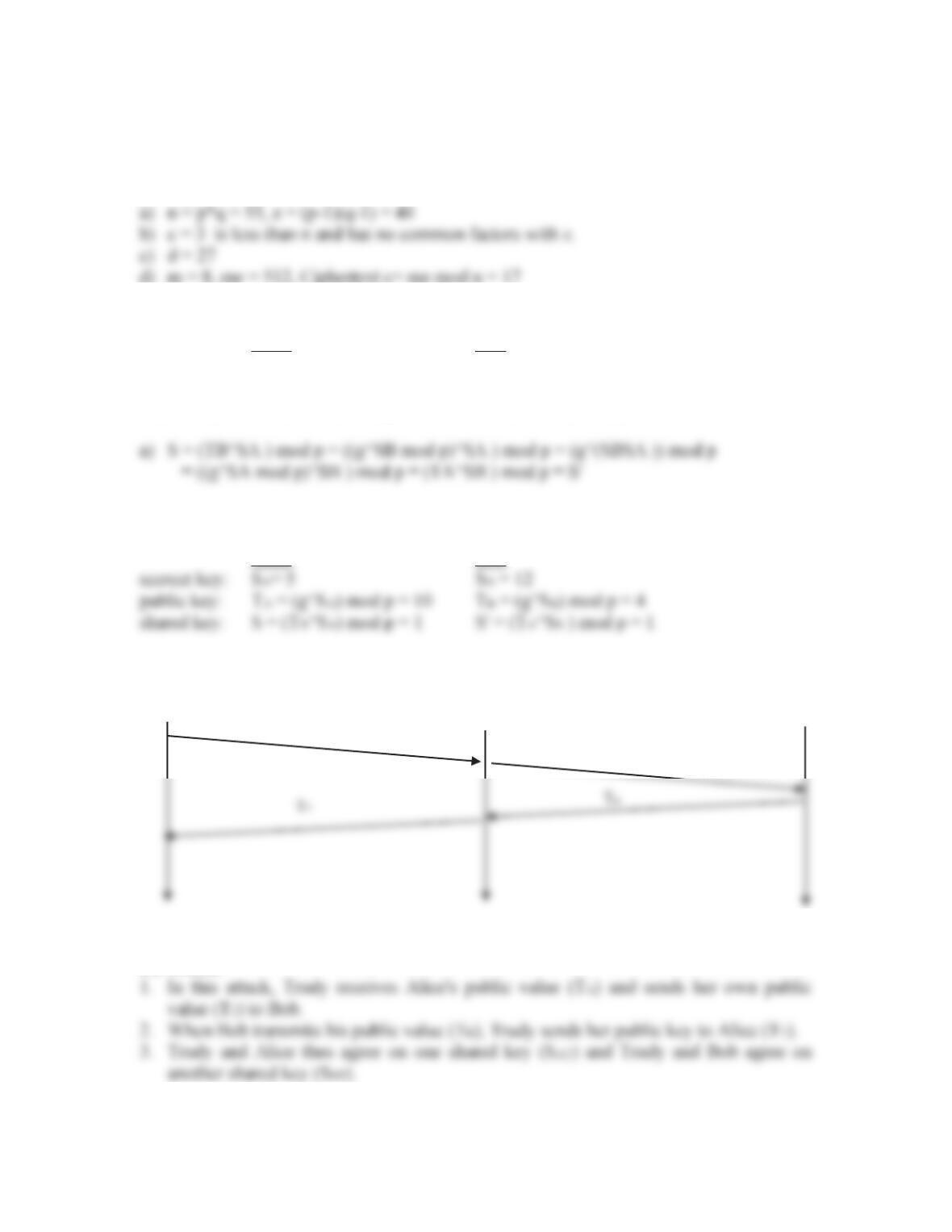
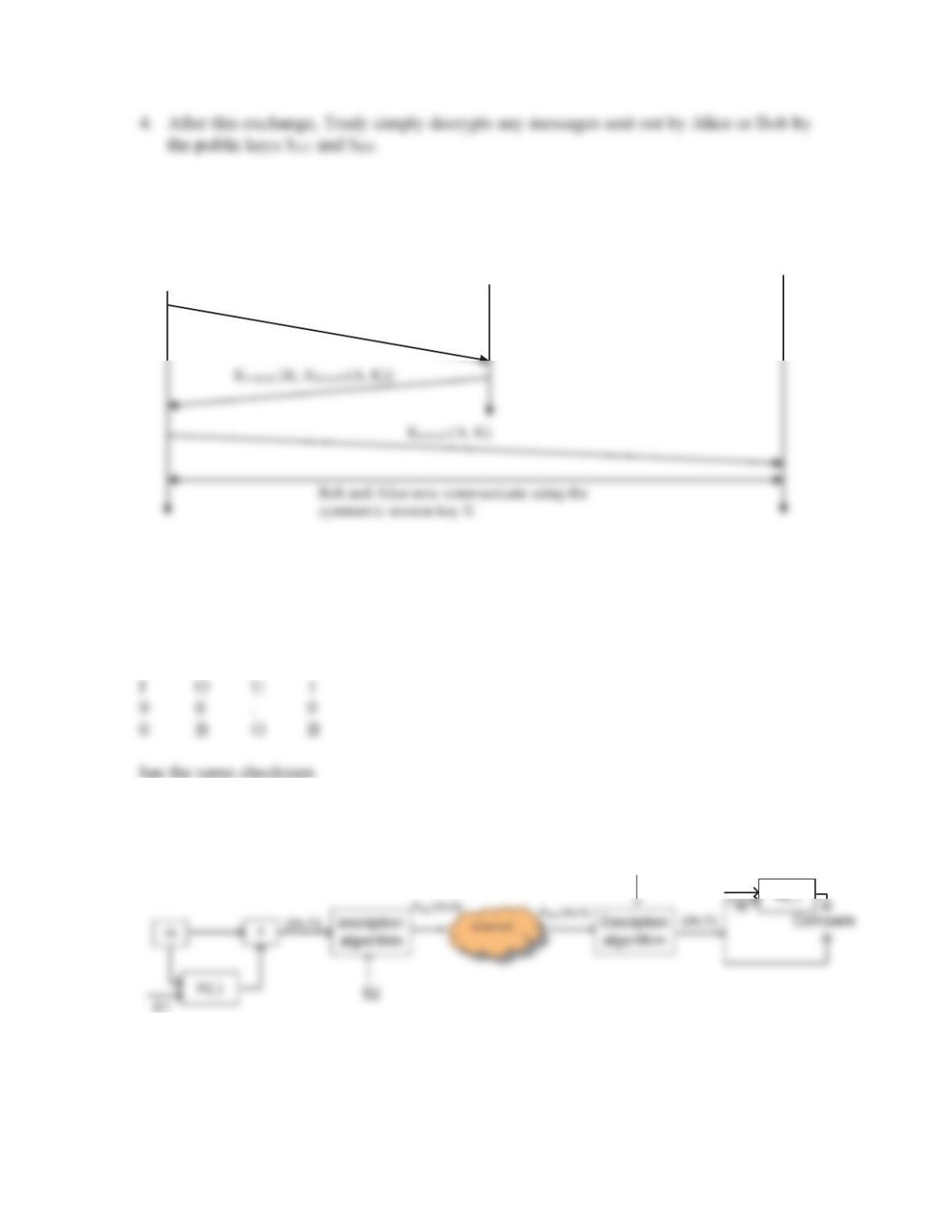
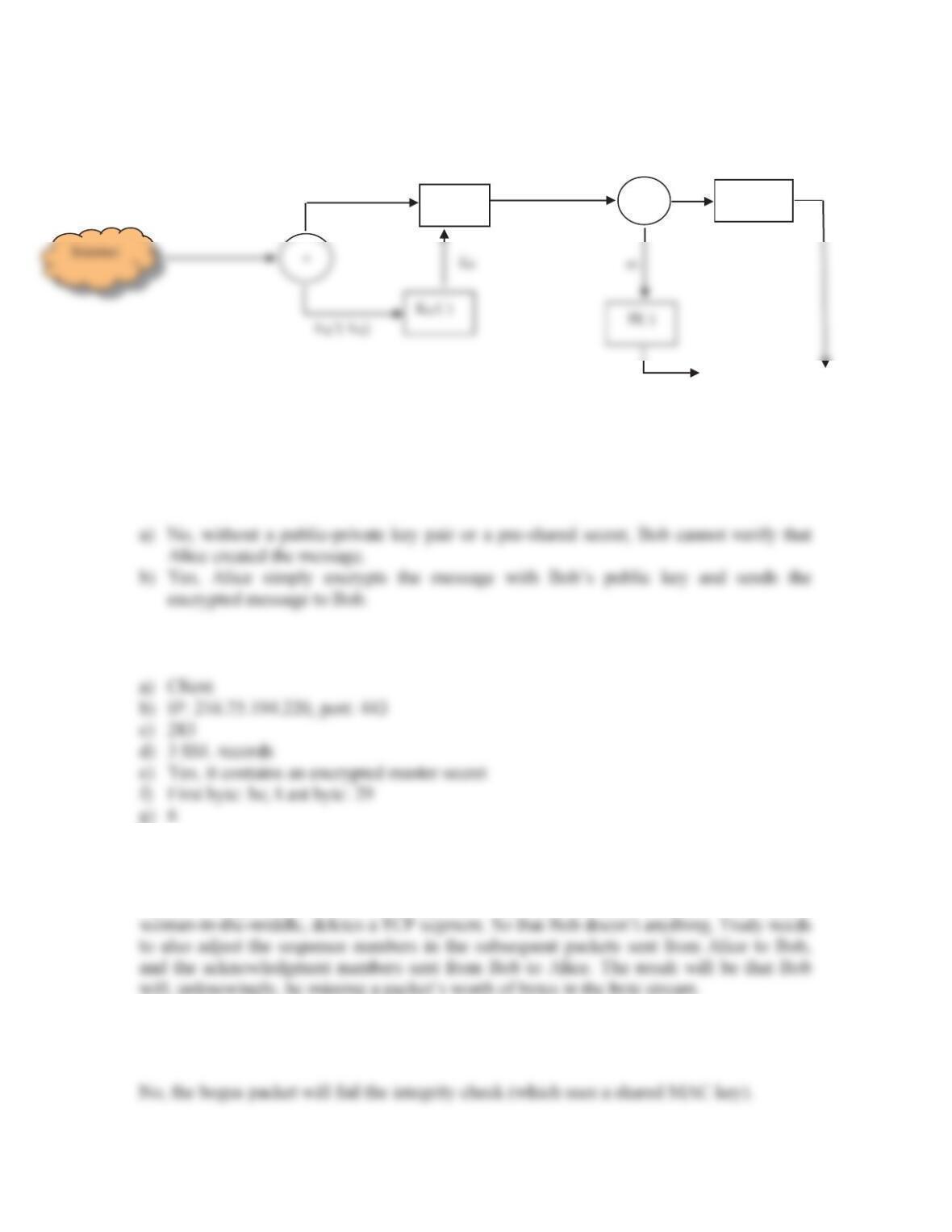
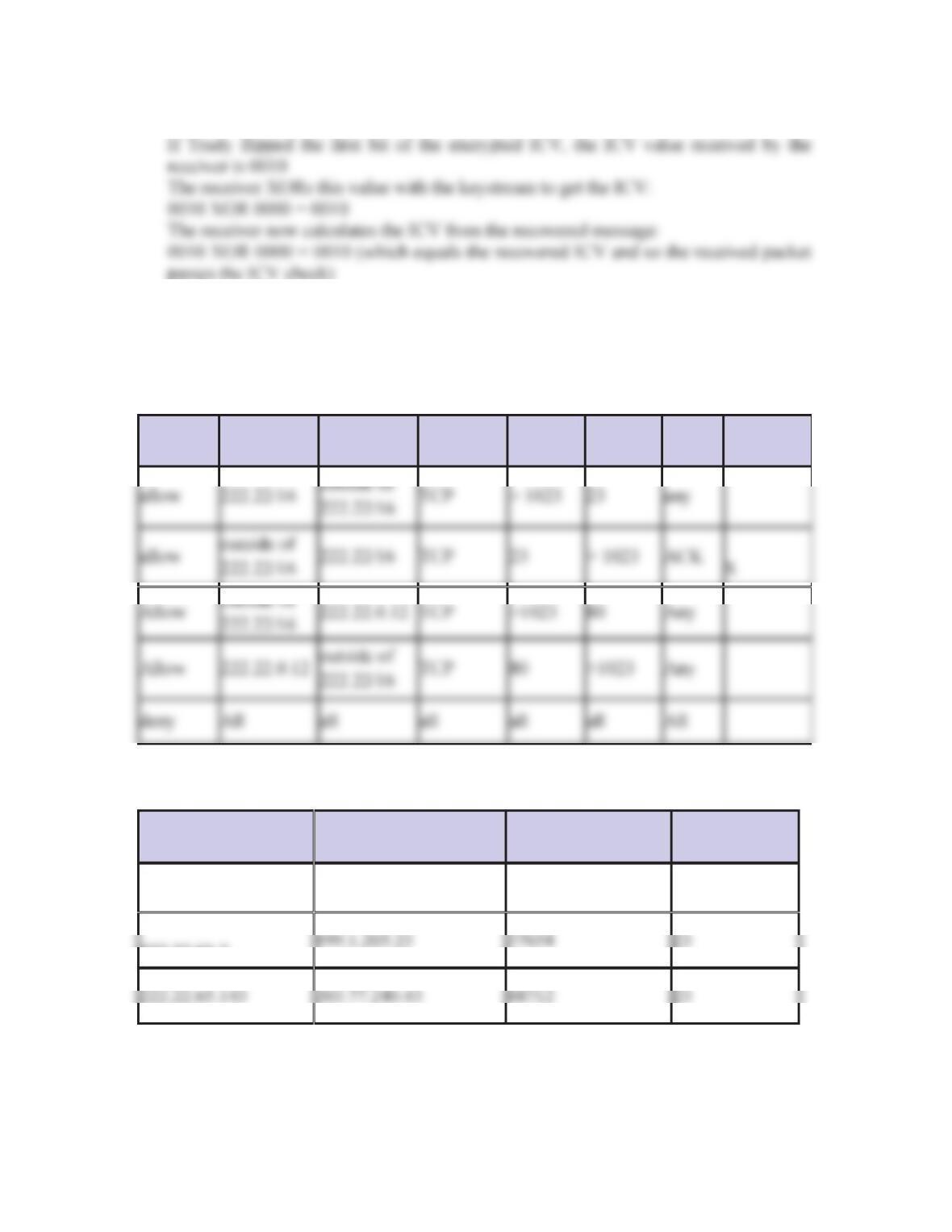
Chapter 8 Review Questions
1. Confidentiality is the property that the original plaintext message can not be
determined by an attacker who intercepts the ciphertext-encryption of the original
plaintext message. Message integrity is the property that the receiver can detect
2. User’s laptop and a web server; (ii) two routers; (iii) two DNS name servers.
3. One important difference between symmetric and public key systems is that in
symmetric key systems both the sender and receiver must know the same (secret) key.
4. In this case, a known plaintext attack is performed. If, somehow, the message
6. If each user wants to communicate with N other users, then each pair of users must
have a shared symmetric key. There are N*(N-1)/2 such pairs and thus there are
7. a mod n = 23 , b mod n = 4. So (a*b) mod n = 23*4=92
9. One requirement of a message digest is that given a message M, it is very difficult to
find another message M’ that has the same message digest and, as a corollary, that