Focus Questions
x What are the characteristics of Ethernet networks, in terms of media access, collisions
domains, broadcast domains, and distance/speed limitations of various Ethernet standards?
x What functions are performed by Ethernet switch features, such as VLANs, trunks, Spanning
Tree Protocol, link aggregation, Power over Ethernet, port monitoring, user authentication,
and first-hop redundancy?
Icebreaker Discussion
Choose one or both of the following:
1. Why is it necessary to have a common language for communication across devices?
This speaks to the need for Ethernet and why it became so popular; without it you would
have to define the communication structure between any two devices that connect.
2. What are the characteristics of a network cable designated as 100BASET?
It is important for students to identify the characteristics of the Ethernet standard
designations. They will need to understand, recognize, and memorize these for the exam.
Icebreaker Activity
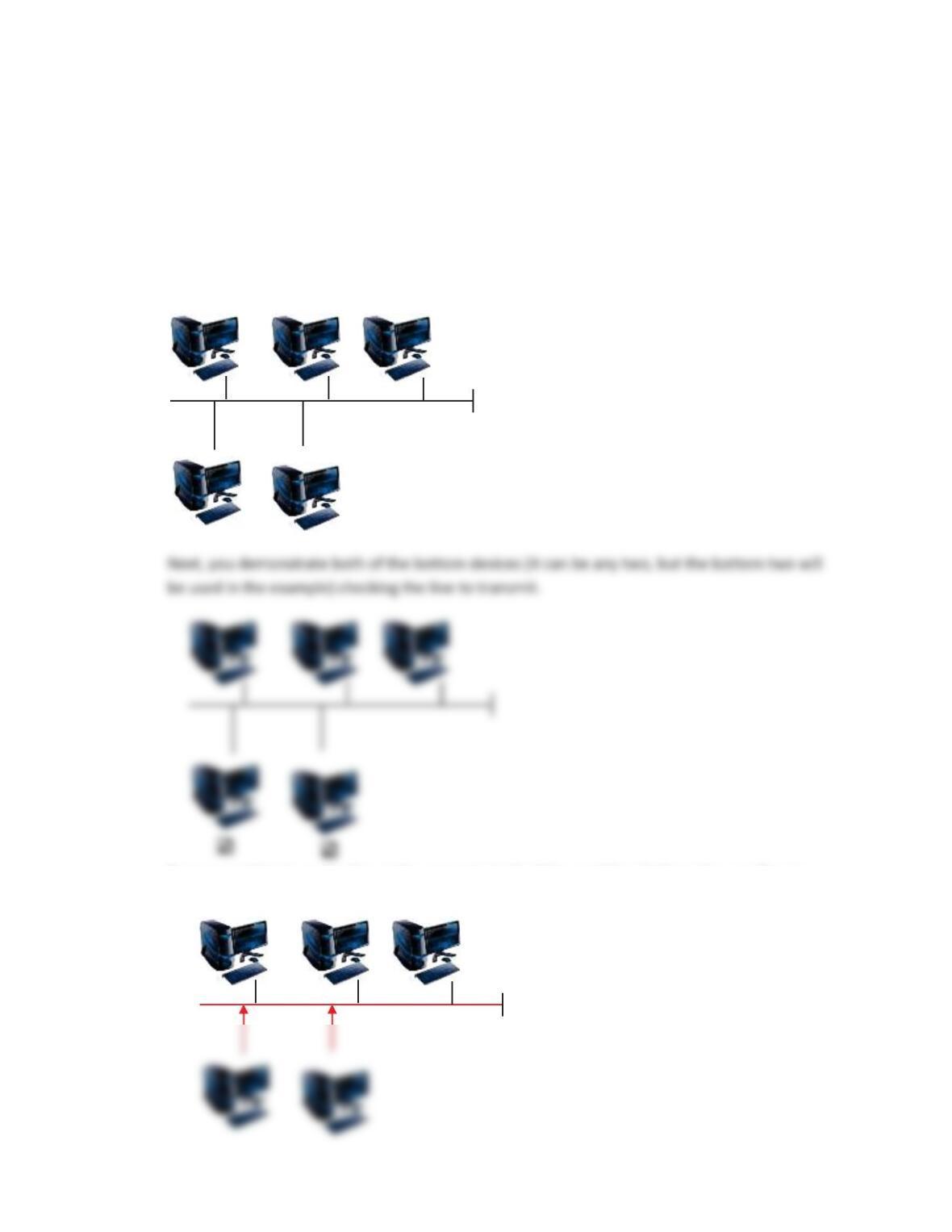
1. On a bus topology, explain the possibility of collisions in transmission. Diagram the topology
to aid in the explanation.
For this activity, you will build the need for collision detection and recovery. This also