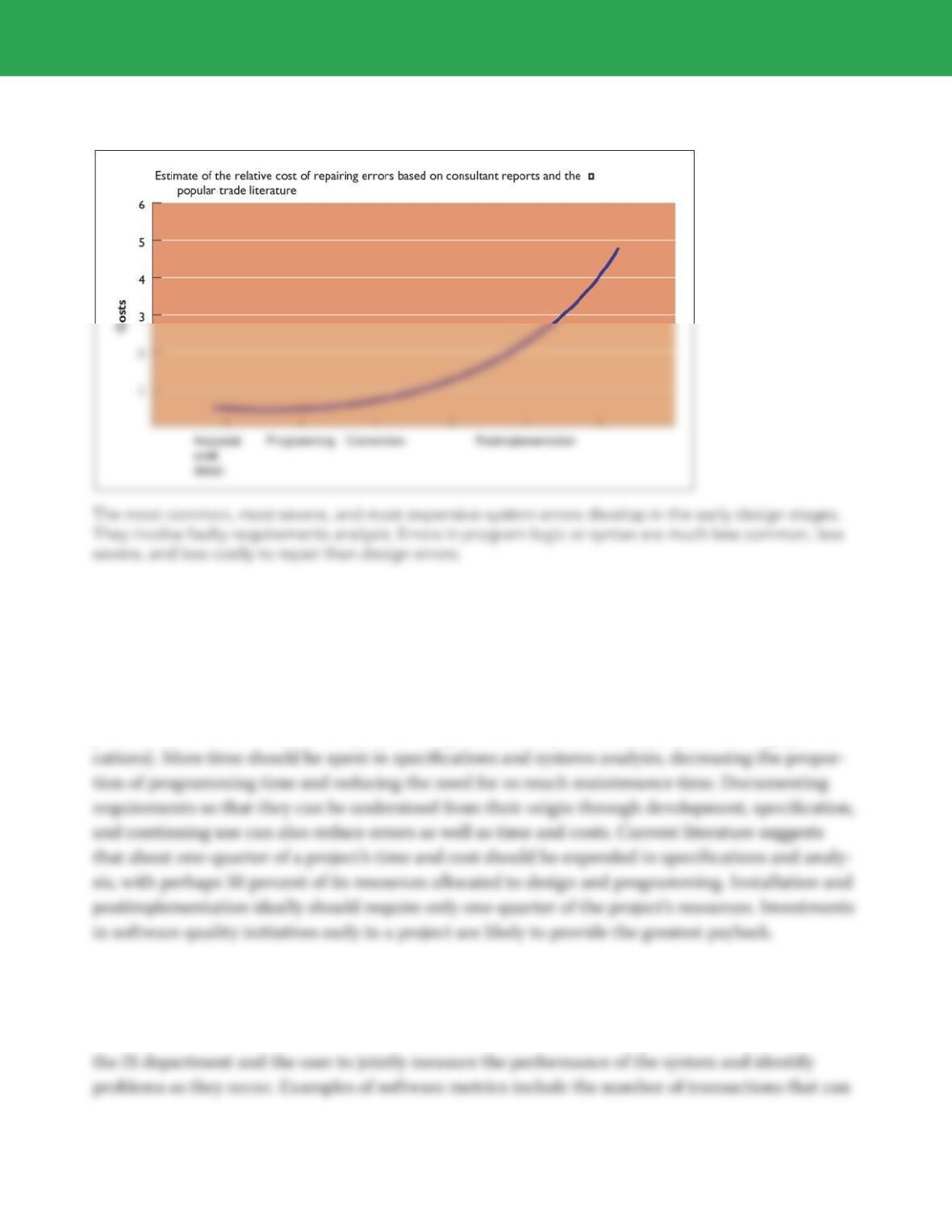
Chapter 8 Learning Track 6 4
be processed in a specified unit of time, online response time, the number of payroll checks printed
per hour, and the number of known bugs per hundred lines of code.
TESTING
e stages of testing required to put an information system into operation are program testing,
system testing, and acceptance testing. Early, regular, and thorough testing will contribute signifi-
cantly to system quality. In general, software testing is often misunderstood. Many view testing as
a way to prove the correctness of work they have done. In fact, we know that all sizable software is
riddled with errors, and we must test to uncover these errors.
Testing begins at the design phase. Because no coding exists yet, the test normally used is a walk-
through—a review of a specification or design document by a small group of people carefully
Electronic commerce and electronic business applications introduce new levels of complexity for
testing to ensure high-quality performance and functionality. Behind each large Web site, such as
Amazon.com, eBay, or E*TRADE, are hundreds of servers, thousands of miles of network cable,
and hundreds of software programs, creating numerous points of vulnerability. ese Web sites
must be built and tested to make sure that they can withstand expected—and unexpected—spikes