Chapter 8 Learning Track 4 10
4. Maintenance. Data on computer files must continue to remain correct
and current.
TABLE 3 Important Edit Techniques
Edit Technique Description Example
Reasonableness checks To be accepted, the data must
fall within certain limits set in
advance, or they will be
rejected.
If an order transaction is for 20,000
units and the largest order on record
was 50 units, the transaction will be
rejected.
Format checks Characteristics of the contents
A nine-position Social Security
Existence checks The computer compares input
reference data to tables or
master files to make sure that
valid codes are being used.
An employee can have a Fair Labor
Standards Act code of only 1, 2, 3,
4, or 5. All other values for this field
will be rejected.
Dependency checks The computer checks whether a
logical relationship is main-
tained between the data for the
same transaction. When it is
not, the transaction is rejected.
A car loan initiation transaction
should show a logical relationship
between the size of the loan, the
number of loan repayments, and the
size of each installment.
Check digit An extra reference number
called a check digit follows an
A product code with the last posi-
tion as a check digit, as developed
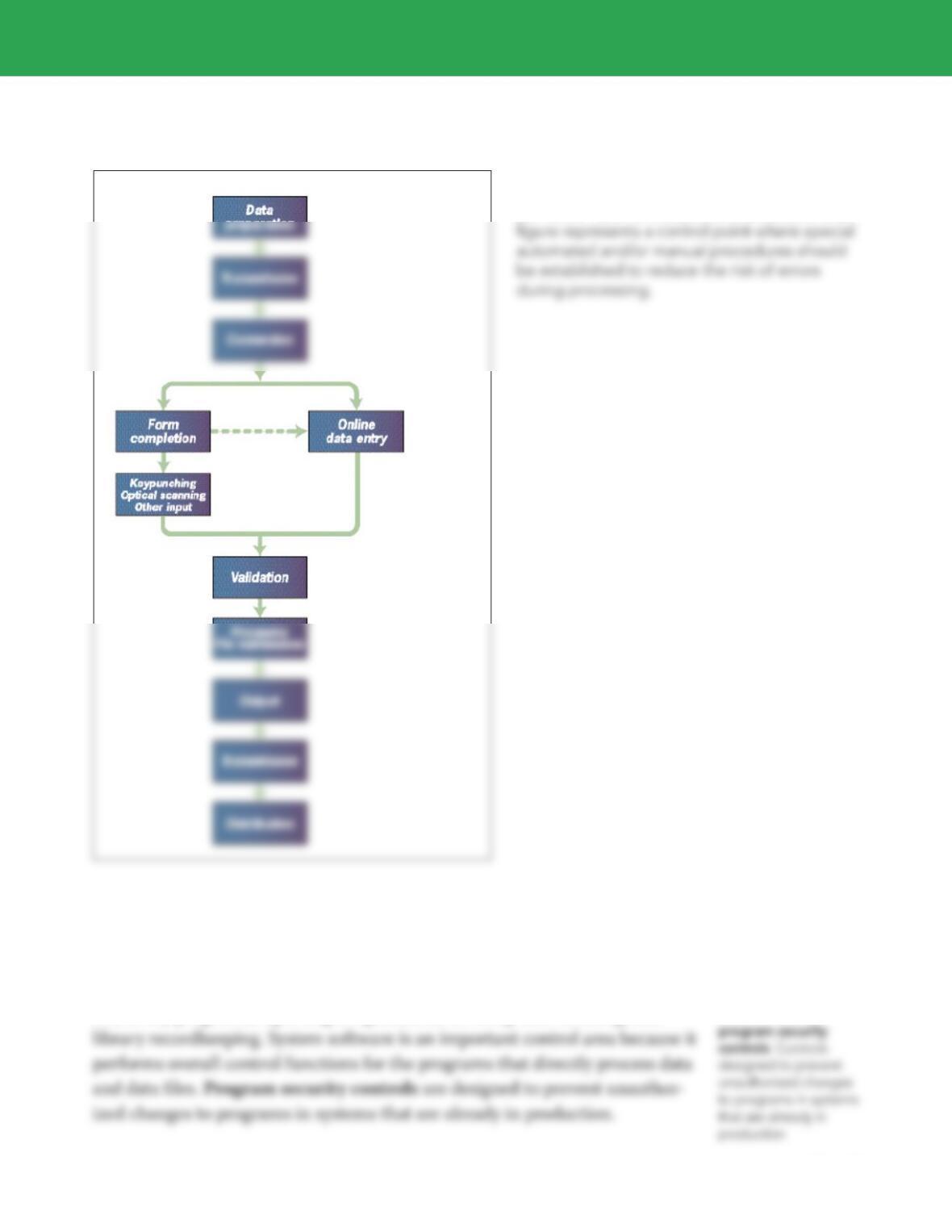
Application controls can be classified as (1) input controls, (2) processing
controls, and (3) output controls.
INPUT CONTROLS
input
controls Procedures to
check data for accuracy