Chapter Six – Database Administration
TEACHING SUGGESTIONS
• This chapter introduces the topic of database administration by describing the
fundamental concepts, technology, and terminology used for multi-user database
management.
• This text distinguishes between database administration and data administration.
The latter is an organizational activity that typically sits high in the enterprise
organization chart and may be concerned with much larger issues than the
maintenance of a particular database. This chapter is concerned with database
administration, a more pedestrian function that occurs at a much lower level in the
organization. Every multi-user database needs a database administrator. The
administrator may only have a few tasks to perform and may work on them only a
few hours a week, but someone needs to be given the responsibility for ensuring that
the database administration tasks are accomplished on a timely basis. This is
especially true for Internet technology databases where the users may be far away
or even anonymous, and where the consequences of failures and mistakes will be
difficult to correct.
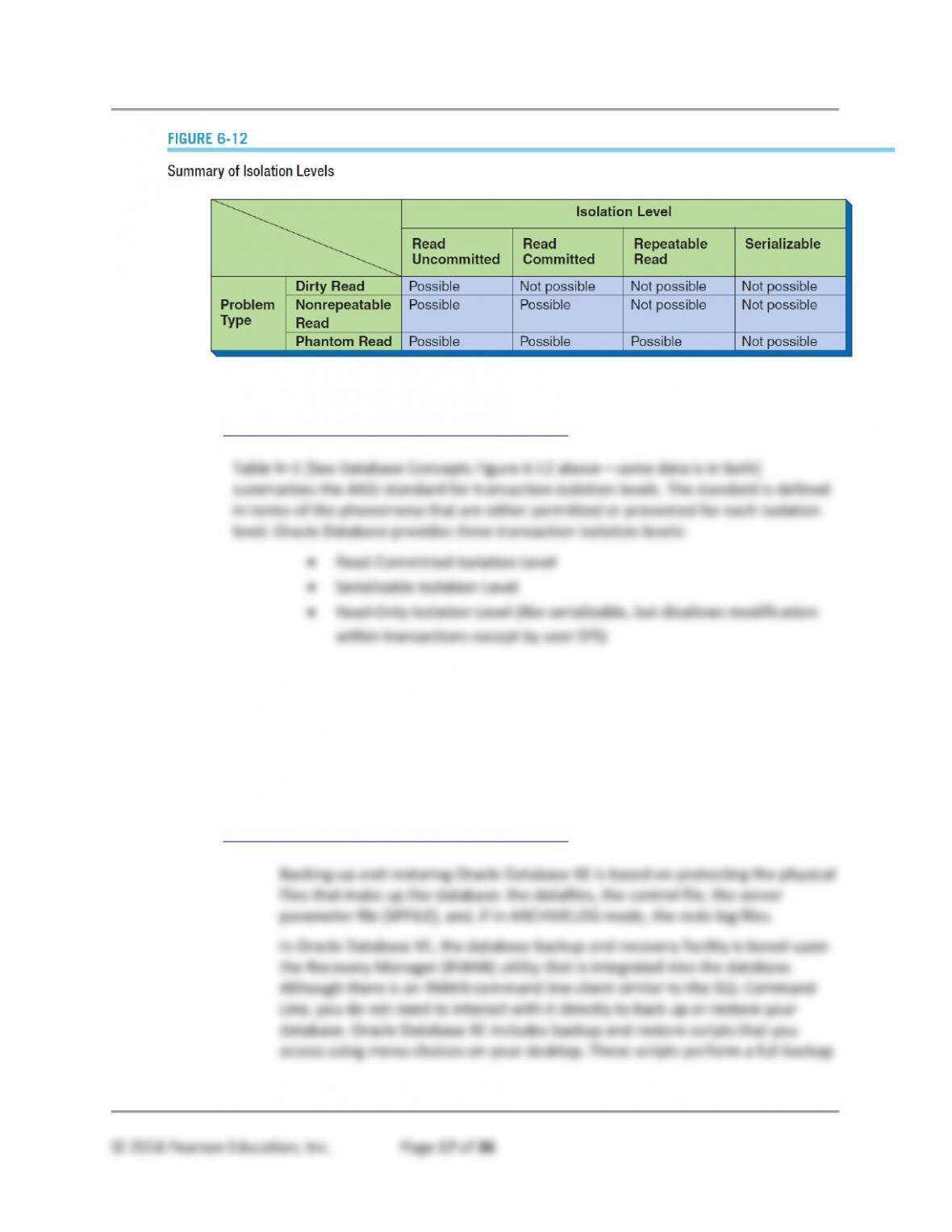
• Concurrency control is important and sometimes seems obscure. If users do not
learn the concepts and techniques, however, the DBMS will use default settings.
These defaults may be perfect, but they also may be terrible. Thus, even though
these issues can be ignored, their ramifications cannot be avoided.
• Security is becoming more and more important. As implied in the text, for Internet
applications, security tasks are accomplished by both the Web server and the
DBMS. Students should look into these issues when they have had both Web server
and database classes.
• If you are working with SQL Server 2016, be sure to create the server login and
database user accounts as shown in the chapter. The Web site material in Chapter
7 will not work without them!
• The goal of this chapter with regard to backup and recovery is to raise the students’
consciousness to these issues. They should get a general idea of the importance of
backup and recovery and the general nature of backup and recovery tools and
techniques.