Algorithms: Sequential, Parallel and Distributed 1-2
Overview
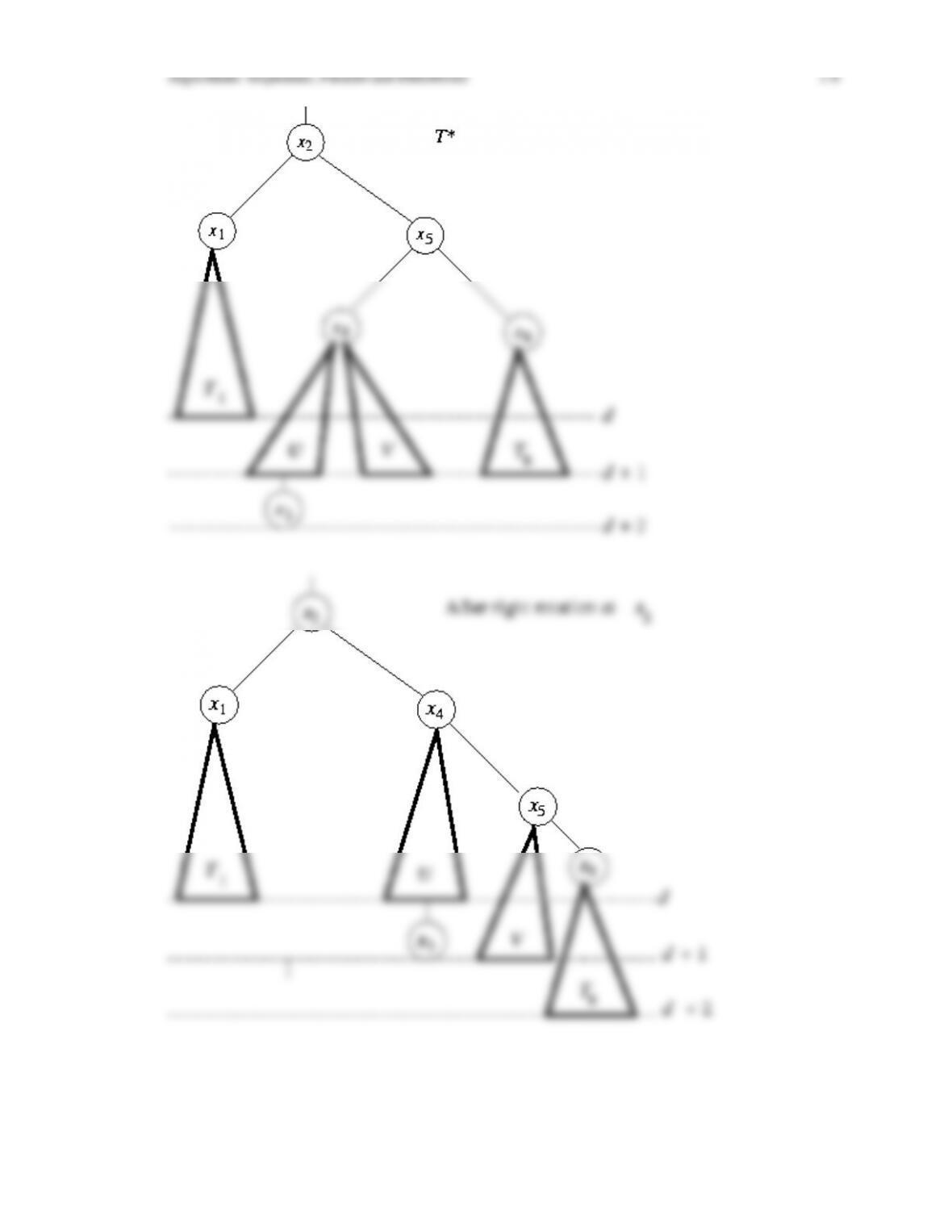
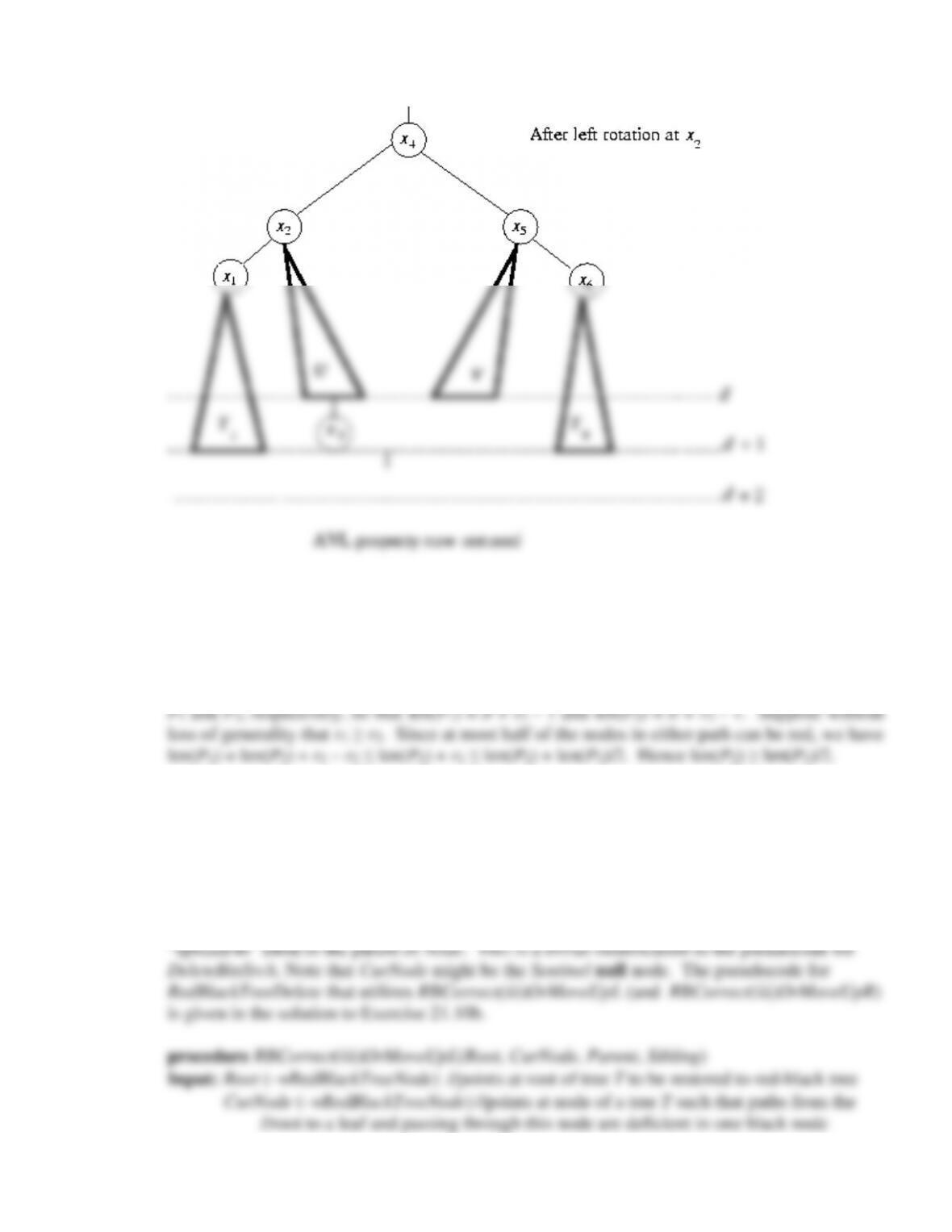
In Chapter 21 we introduce the notion of a balanced binary search tree, and show how rotations
in such trees can be used to help restore balance after nodes have been inserted or deleted. We
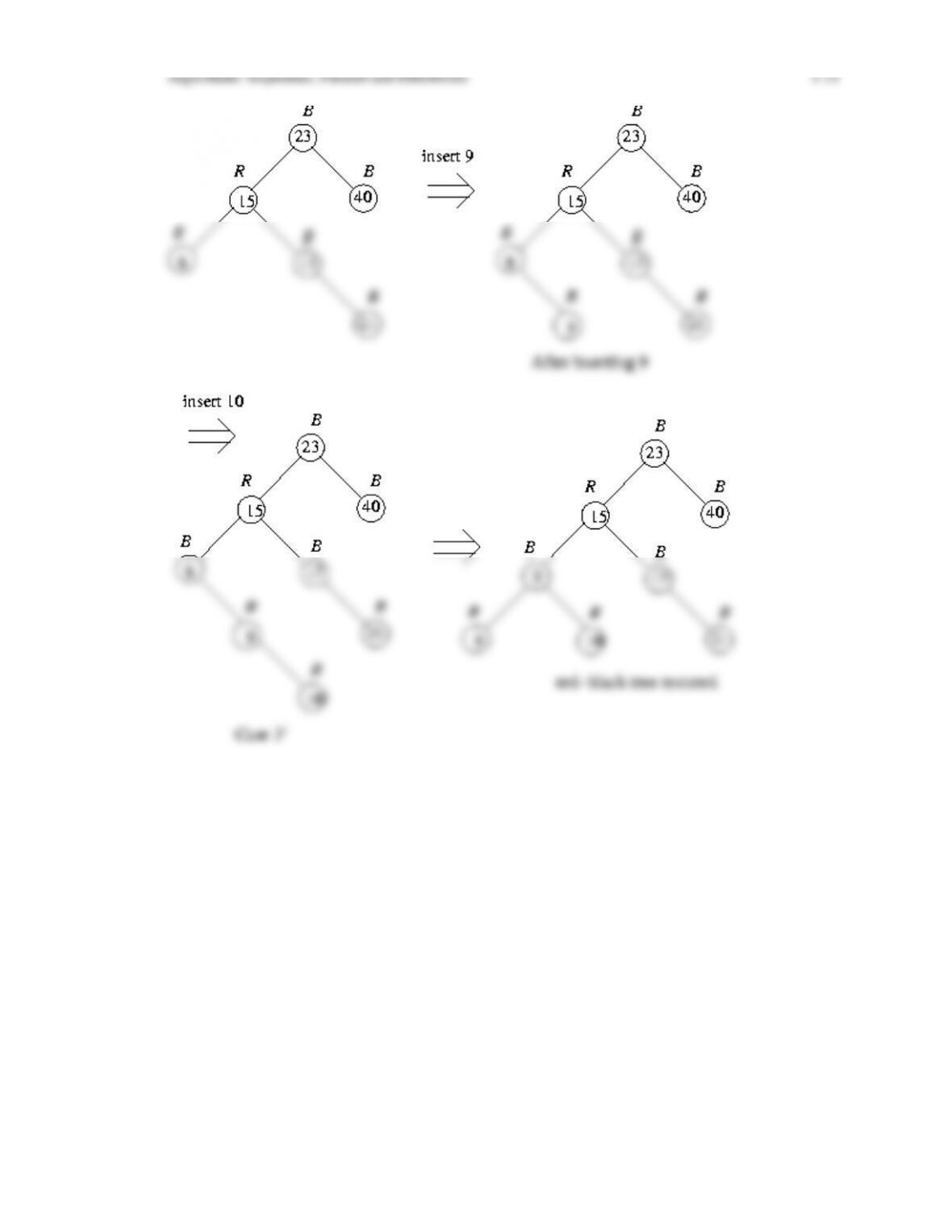
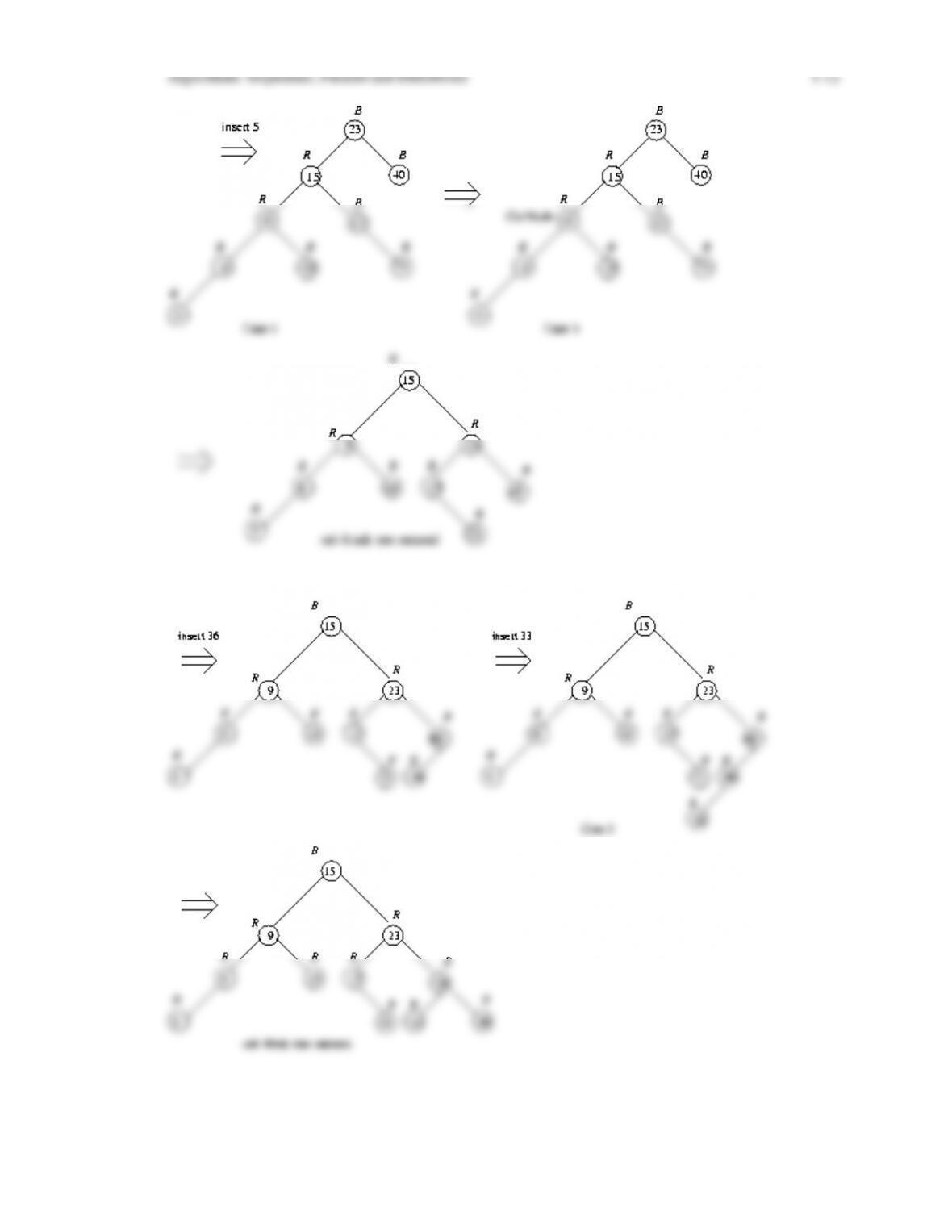
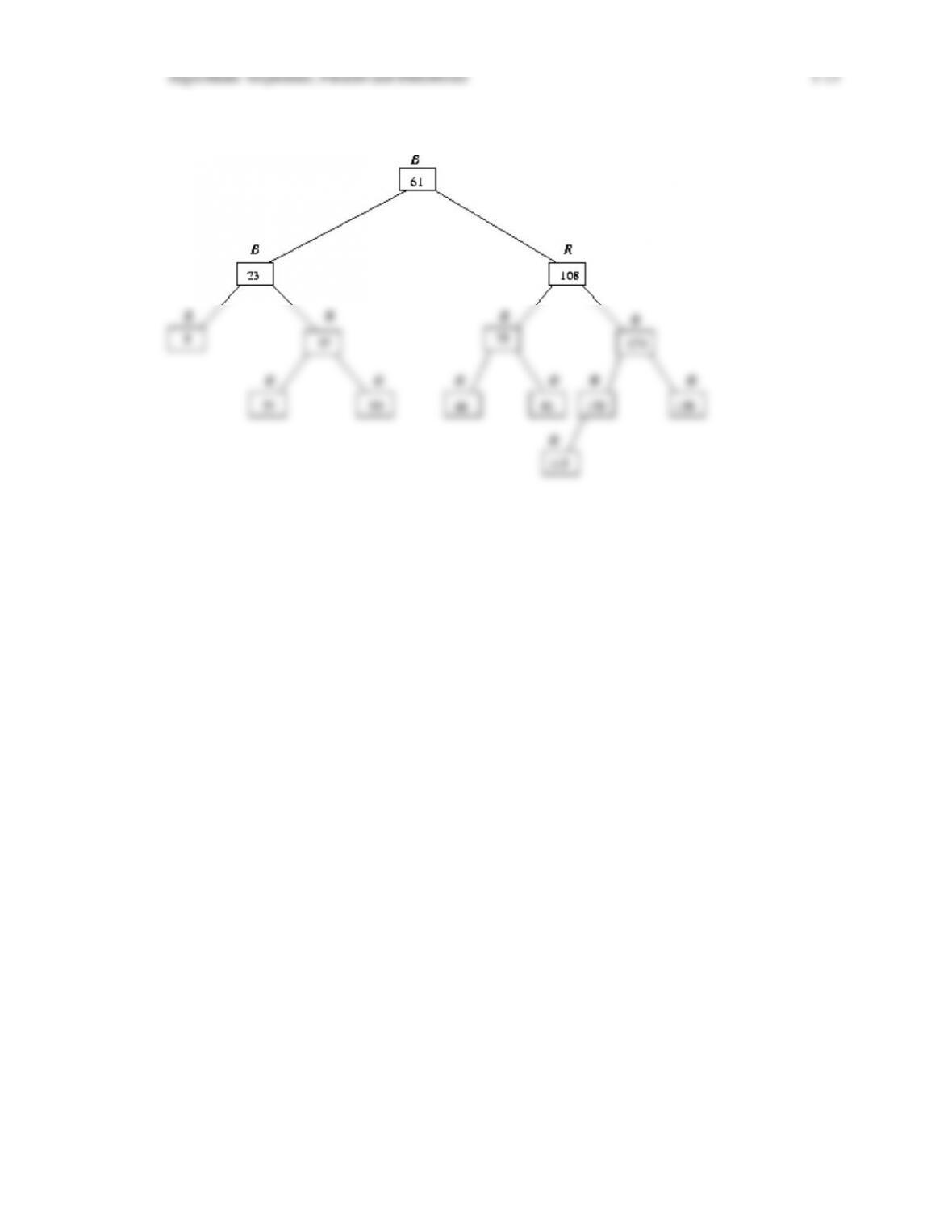
define the notion of an AVL tree and a red-black tree, and prove that the depth of a red-black
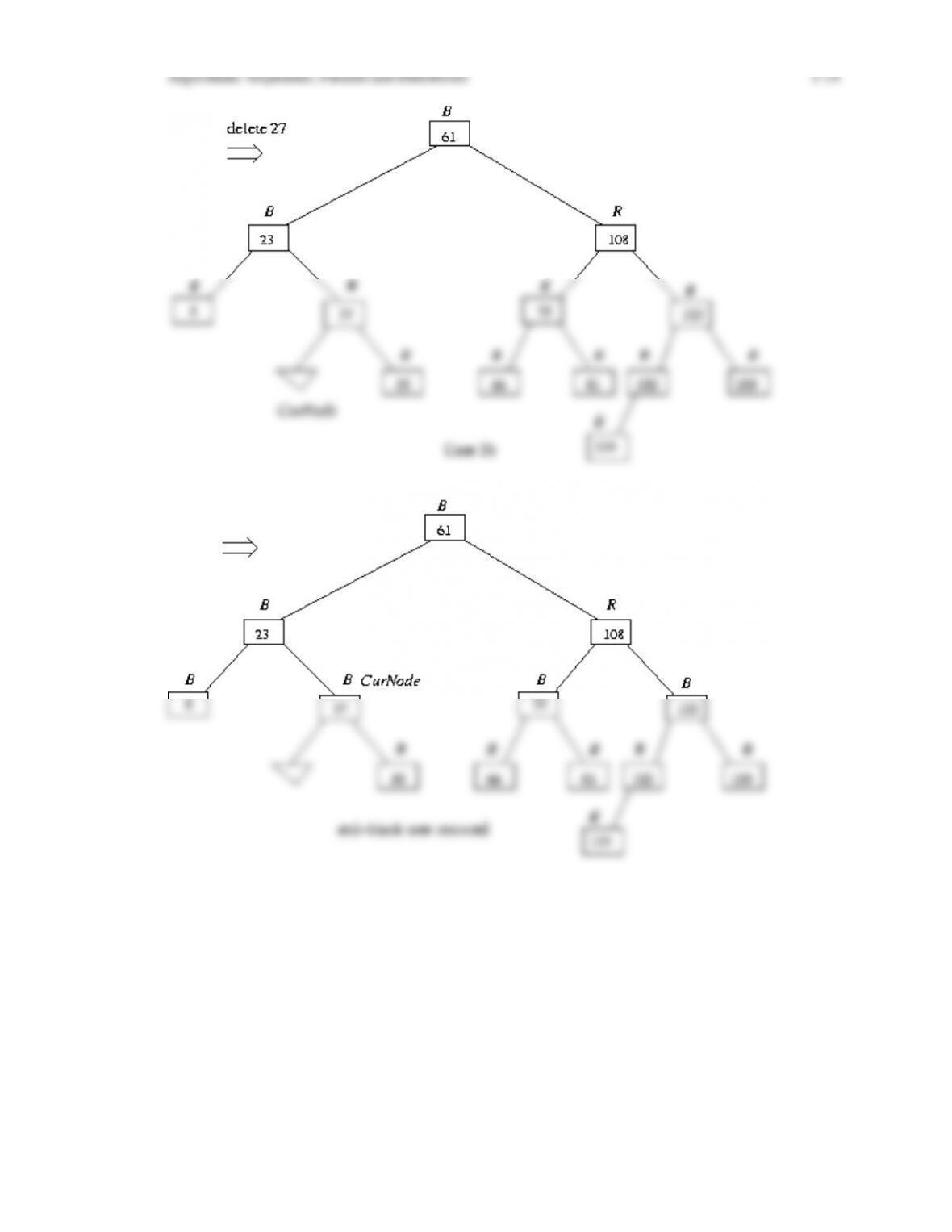
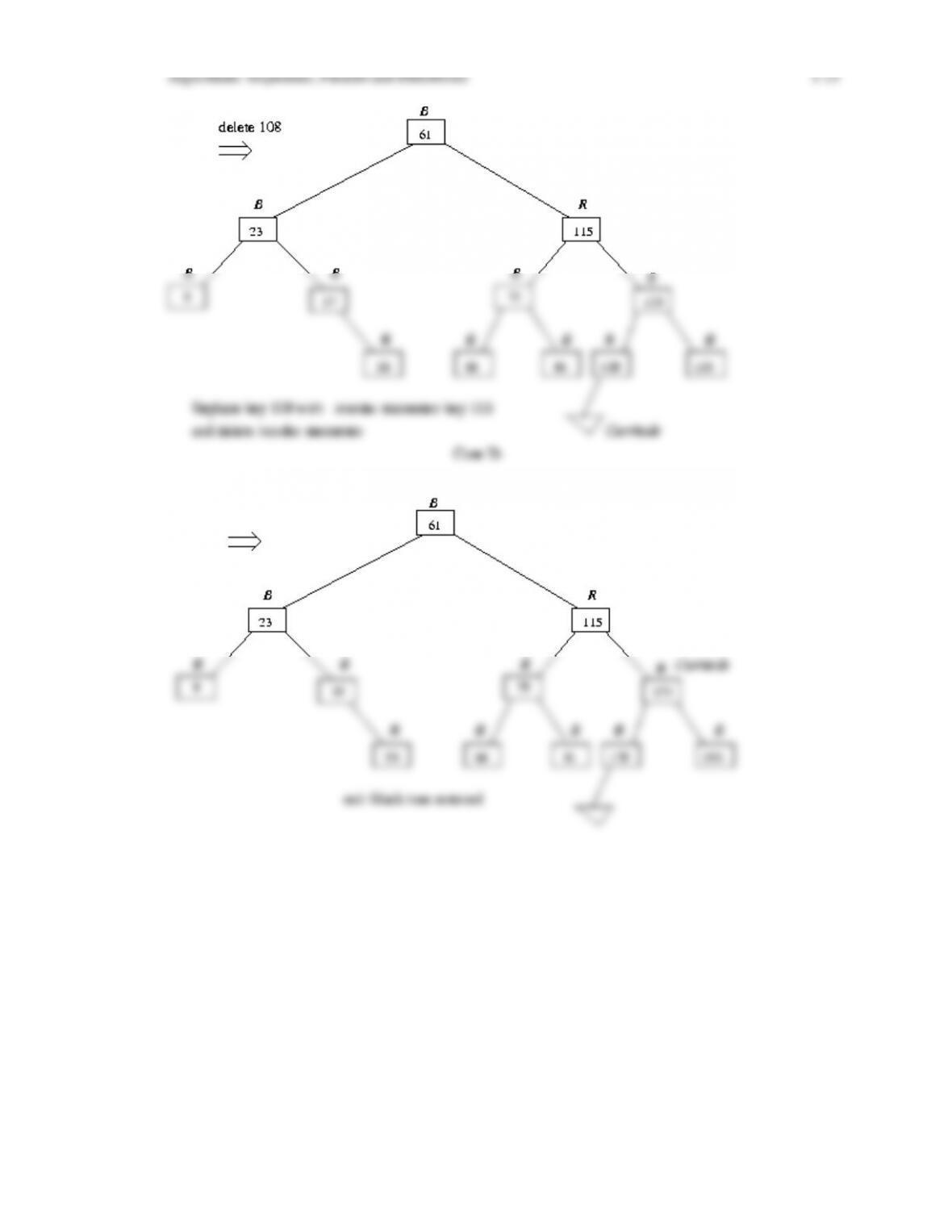
tree is logarithmic in the number of nodes in the tree. We then discuss algorithms for inserting
and deleting nodes in a red-black tree, including giving transition diagrams that show how
these algorithms proceed through the various cases until balance is restored. We finish the
chapter with a discussion of the B-tree multiway search tree, which is a useful ADT for
maintaining externally stored databases.
Chapter Objectives
After completing the chapter the student will know:
• The definitions of AVL and red-black trees
• The notion of a rotation in a binary search tree, and its role in restoring balance in AVL and
red-black trees
Instructor Notes
The algorithms for inserting and deleting elements in a red-black tree are straightforward, but
cumbersome in detail. Certainly one would not expect the student (or the instructor!) to
memorize the various cases and what procedures are followed depending on these cases.