Ch. 9: Information Systems Controls for System Reliability – Part 2: Confidentiality and Privacy
Which of the following actions can you perform?
1. Open the file
2. Copy the file to a USB drive.
3. Move the file to a USB drive.
4. Rename the file.
5. Delete the file
ADDITIONAL NOTE TO INSTRUCTORS: Tell students to save the encrypted file in a
shared directory that is accessible to all users who log onto that system. That way, even a
standard user will be able to see the files.
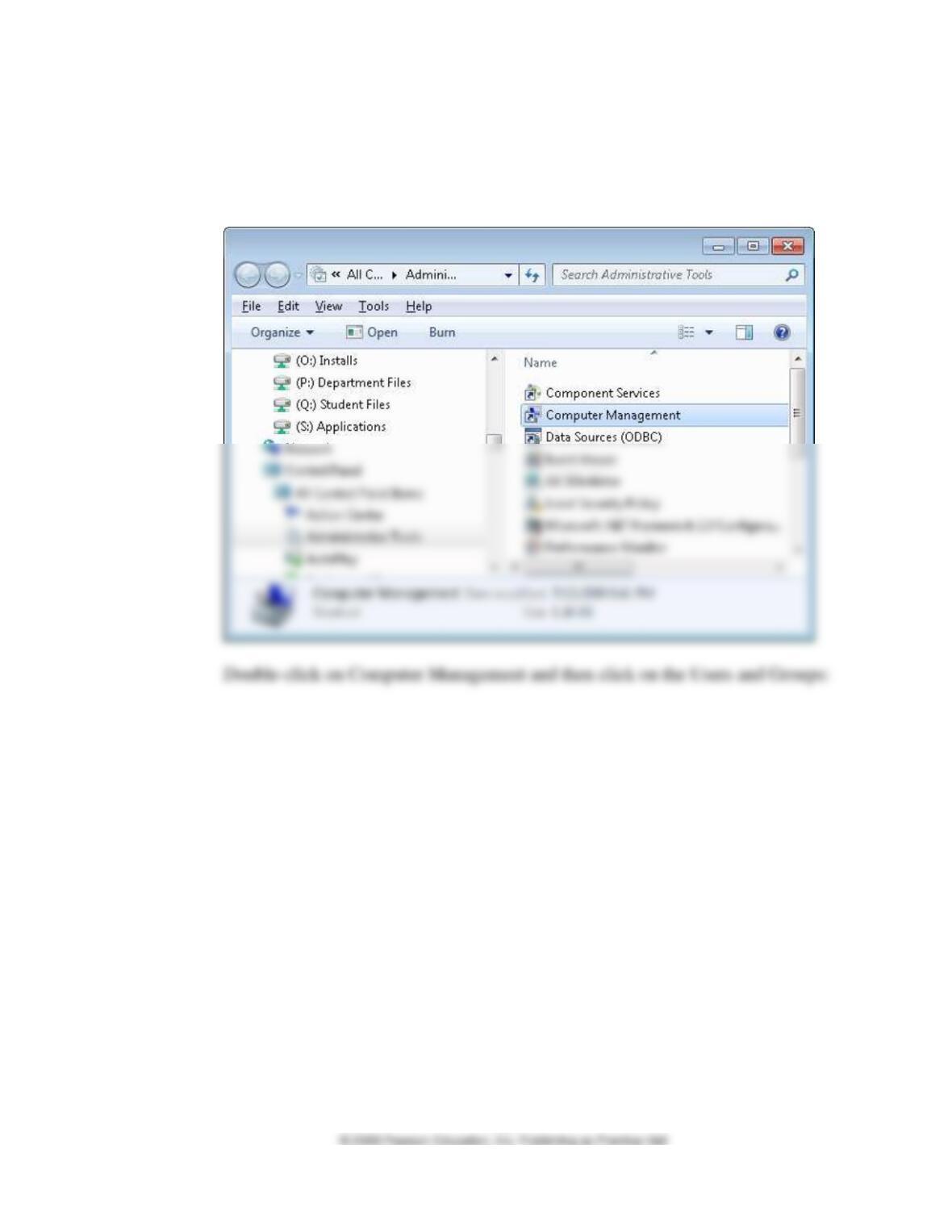
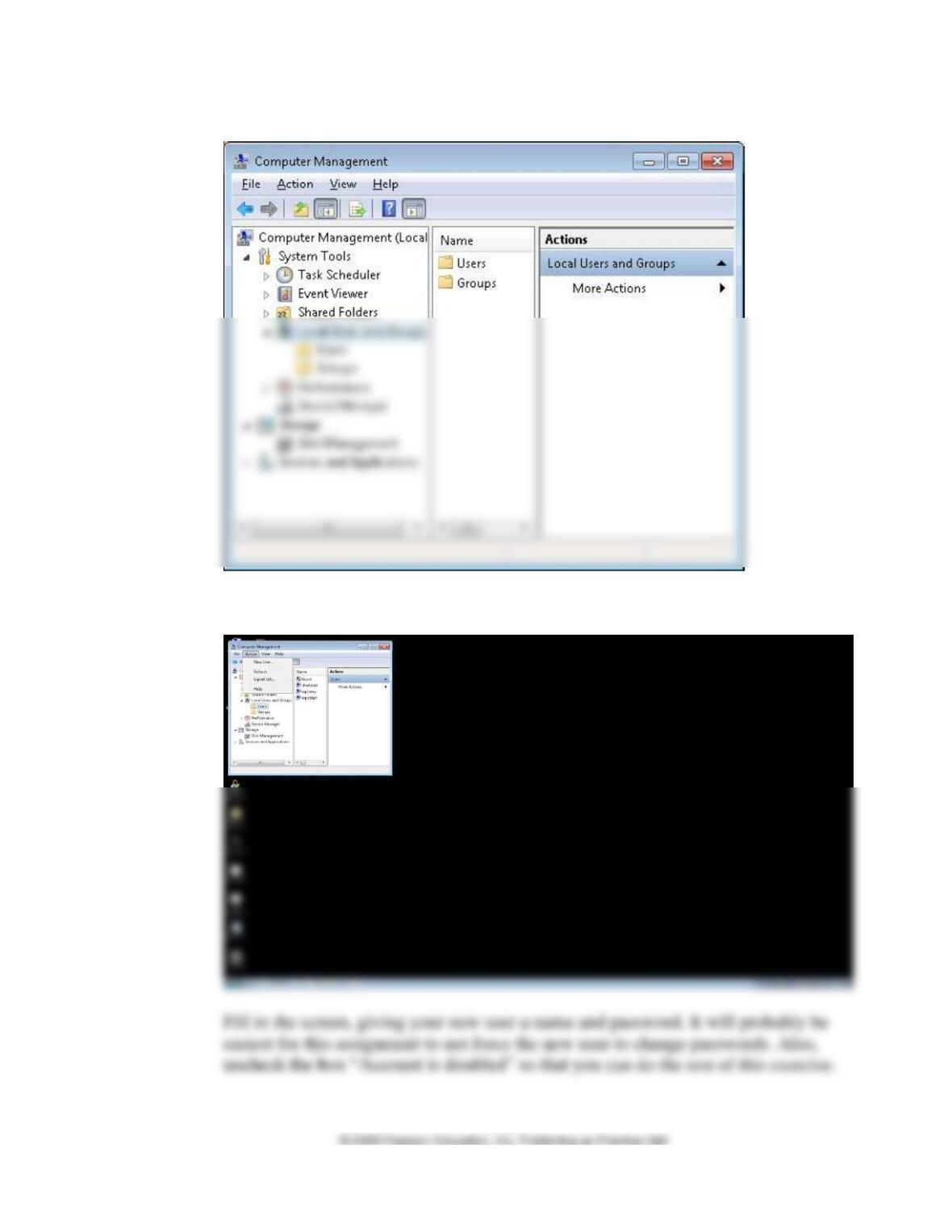
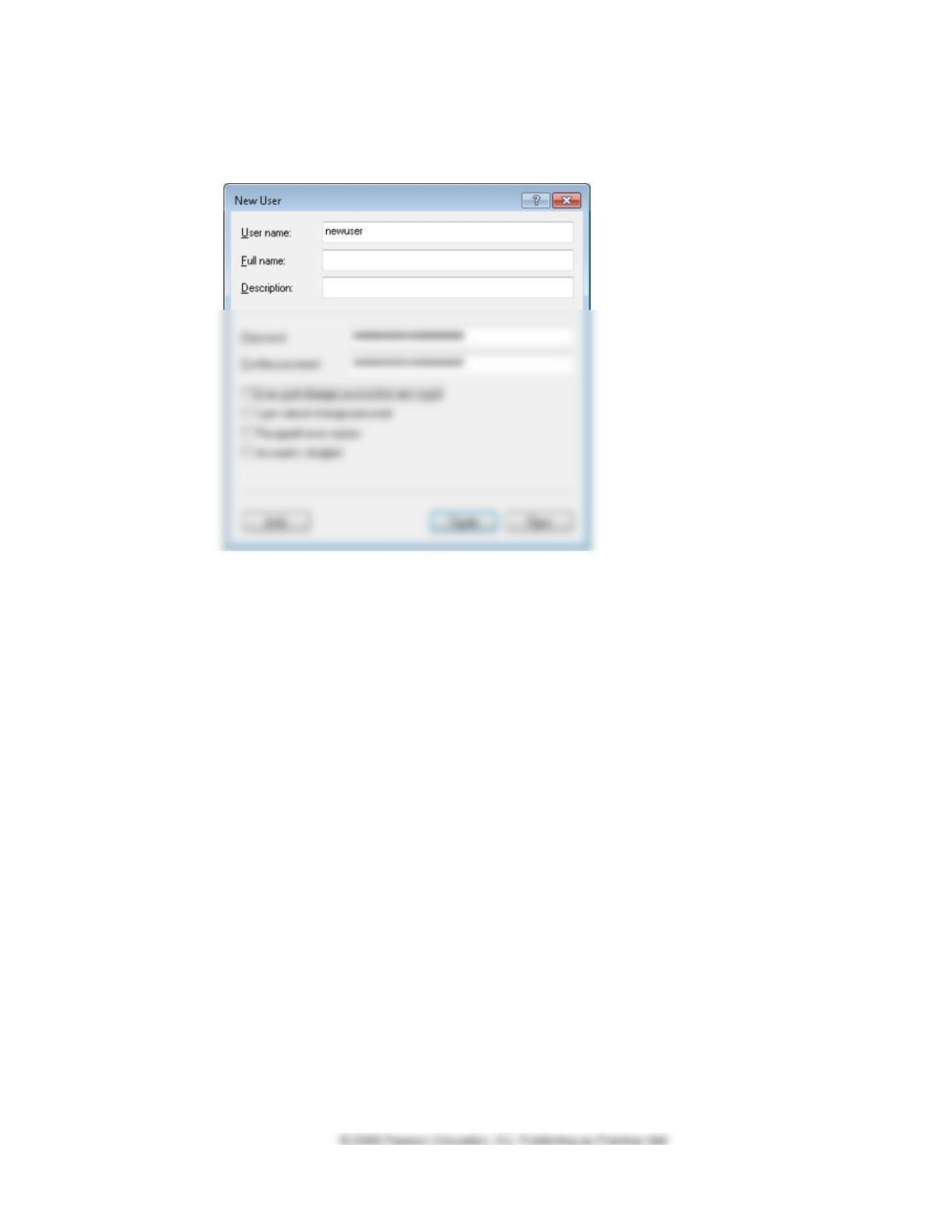
IMPORTANT NOTE TO INSTRUCTORS: Tell students to delete the new user
account that they created to do this problem after they finish the assignment.
b. TrueCrypt is one of several free software programs that can be used to encrypt
files stored on a USB drive. Download and install a copy of TrueCrypt (or
another program recommended by your professor). Use it to encrypt some files
on a USB drive. Compare its functionality to that of the built-in encryption
functionality provided by your computer’s operating system.
9.9 Research the problem of identity theft and write a report that explains:
a. Whether the problem of identity theft is increasing or decreasing