Ch. 9: Information Systems Controls for System Reliability – Part 2: Confidentiality and Privacy
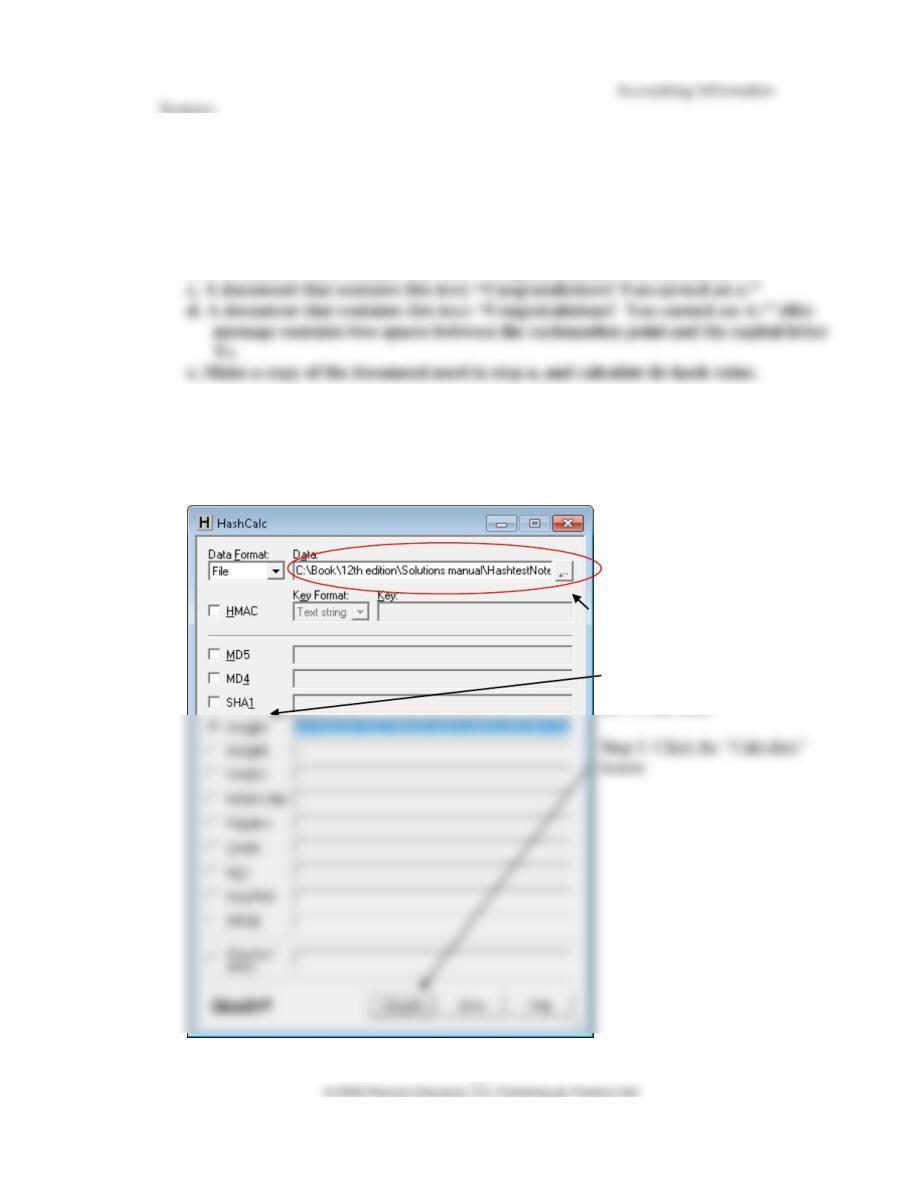
The exact hash values will differ depending upon the program used to create the text
documents (e.g., Word versus Notepad). Below are SHA-256 hashes of files created in
Word for Windows 2007 on a computer running Windows 7:
And here are the SHA-256 hash values of the same files created in NotePad:
Part a: 414b6e3799ccd6ff1fe7fb5c0b720b22995e8f28a0e0eedf00feaf54ed541490
Notice how any change, no matter how small results in a different hash value:
• changing a “+” to a “-“ sign (compare hashes for parts a and part b)
• changing from uppercase “A” to lowercase “a” (compare hashes for parts b and c)
• inserting a space (compare hashes for parts a and d)
This is the reason that hashes are so important – they provide a way to test the “integrity”
of a file. If two files are supposed to be identical, but they have different hash values,
then one of them has been changed.
The solution to part e depends upon whether you are using a simple text editor like
NotePad or a more powerful word processing program like Word. If you are using
If you are using Word, then the “Save As” command will generate a document that has
the same text, but a different hash value because Word incorporates system data when
saving the file:
• Word document for part a:
866af63d78f6546b95e48919e9007309b1cd646da384035c5e6f4790b90cbf24
• Word document for part e: