Accounting Information Systems
12-39
12.10 The Family Support Center is a small charitable organization. It has only four full-
time employees: two staff, an accountant, and an office manager. The majority of its
funding comes from two campaign drives, one in the spring and one in the fall.
Donors make pledges over the telephone. Some donors pay their pledge by credit
card during the telephone campaign, but many prefer to pay in monthly
installments by check. In such cases, the donor pledges are recorded during the
telephone campaign and they are then mailed pledge cards. Donors mail their
contributions directly to the charity. Most donors send a check, but occasionally
some send cash. Most donors return their pledge card with their check or cash
donation, but occasionally the Family Support Center receives anonymous cash
donations. The procedures used to process donations are as follows:
The accountant enters the information from the list into the computer to
update the Family Support Center’s files. The accountant then prepares a
deposit slip (in duplicate) and deposits all cash and checks into the charity’s
bank account at the end of each day. No funds are left on the premises
overnight. The validated deposit slip is then filed by date. The accountant
also mails an acknowledgment letter thanking each donor. Monthly, the
accountant retrieves all deposit slips and uses them to reconcile the Family
Support Center’s bank statement. At this time, the accountant also reviews
the pledge files and sends a follow-up letter to those people who have not yet
fulfilled their pledges.
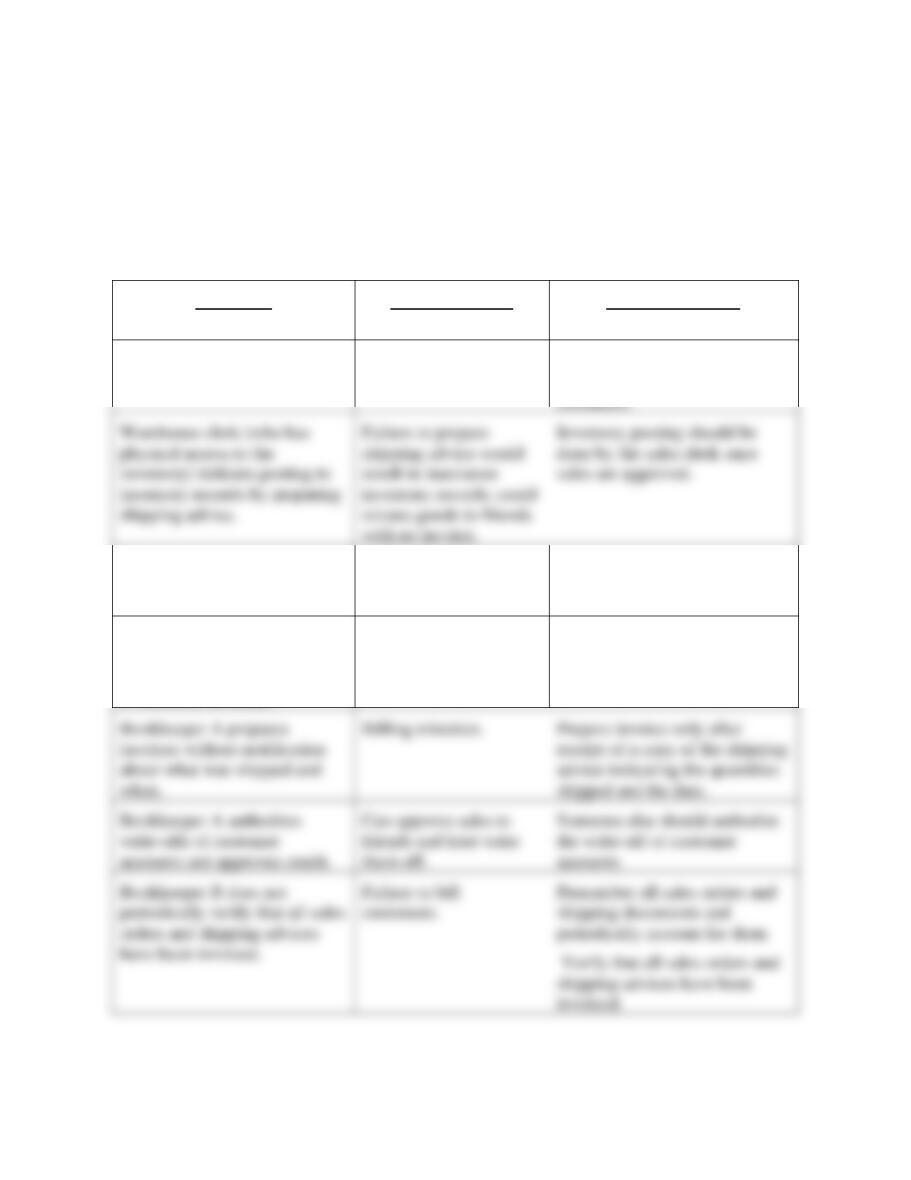
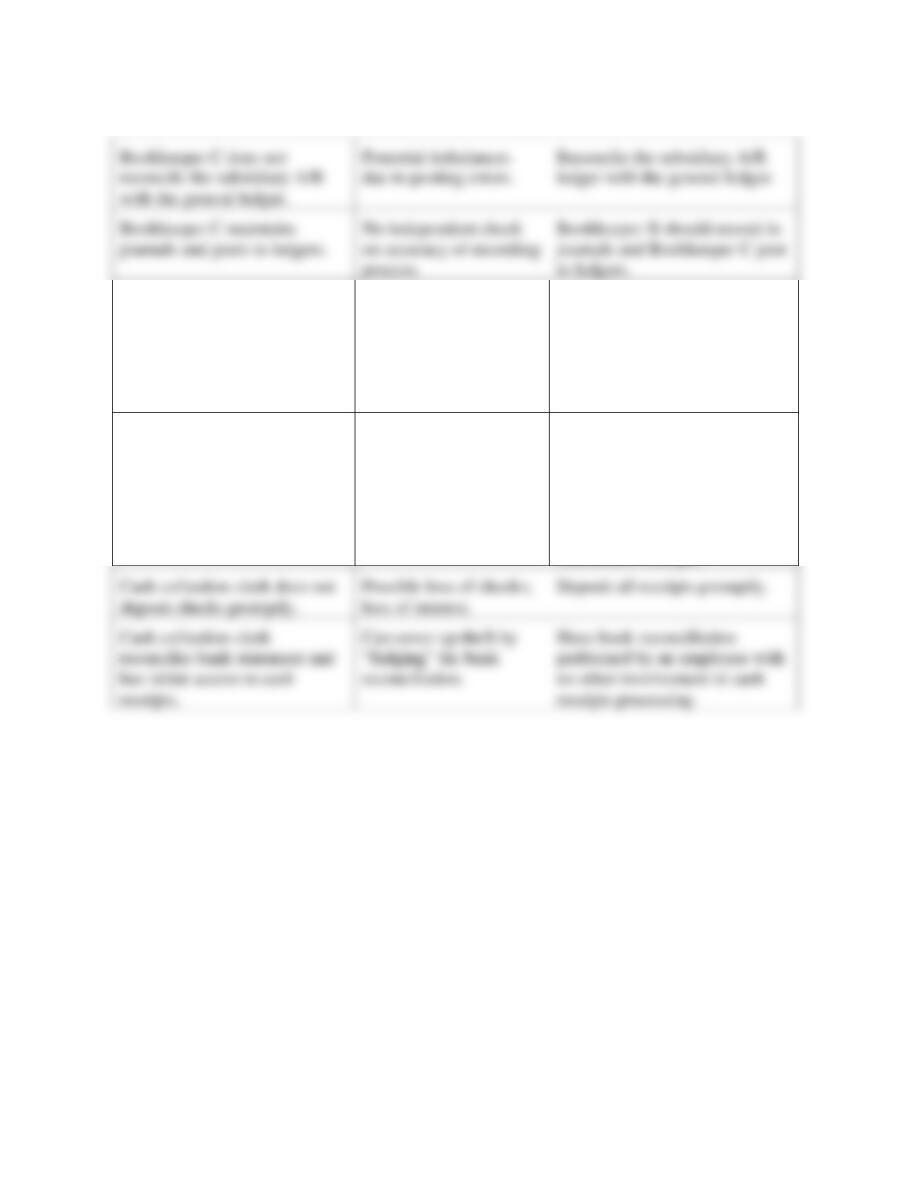
1. Weakness - Sarah opens all mail and prepares a list of donations (cash and
checks). Sarah could misappropriate anonymous cash donations.