Ch. 10: Information Systems Controls for Systems Reliability – Part 3: Processing Integrity and
Availability
i. When entering a large credit sale, the clerk typed in the customer’s account
number as 45982 instead of 45892. That account number did not exist. The
mistake was not caught until later in the week when the weekly billing process
was run. Consequently, the customer was not billed for another week, delaying
receipt of payment.
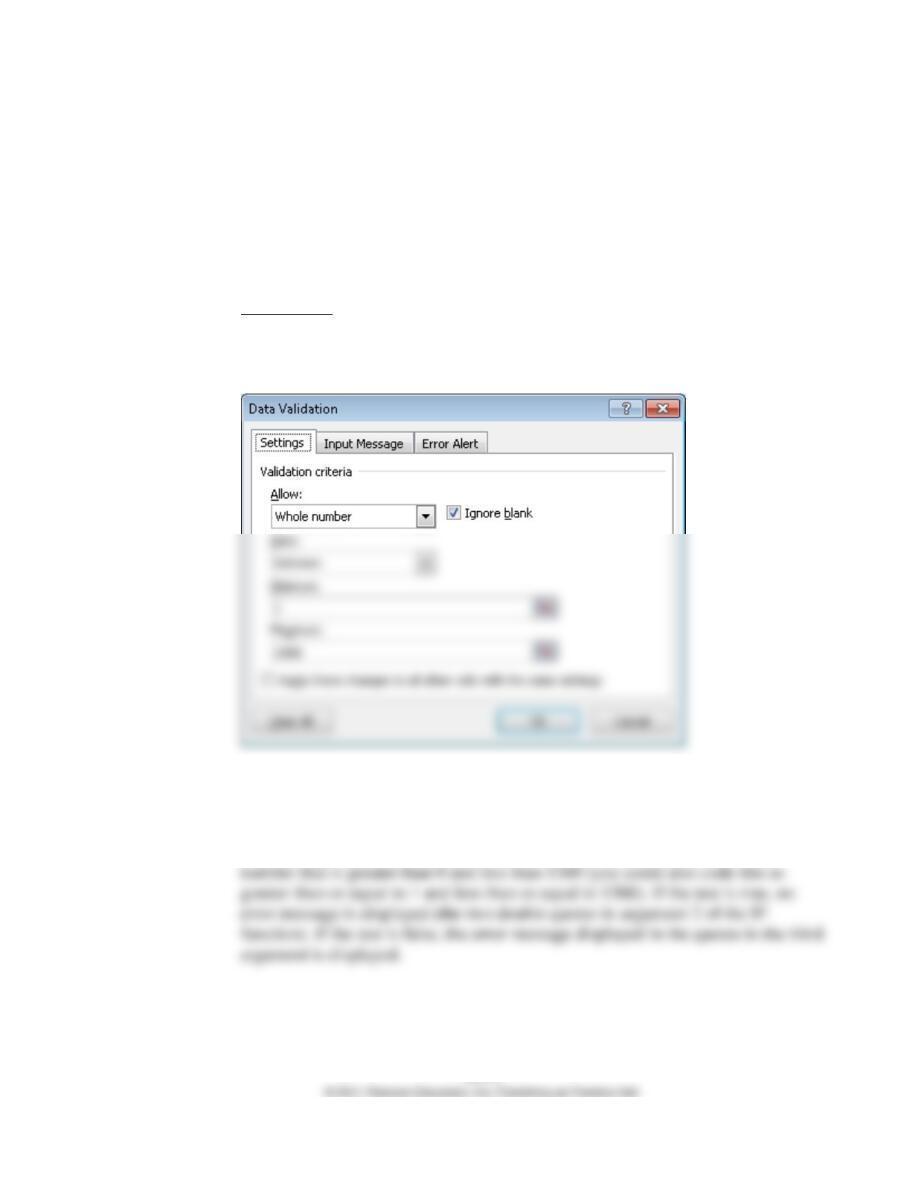
Check digit verification on each customer account number
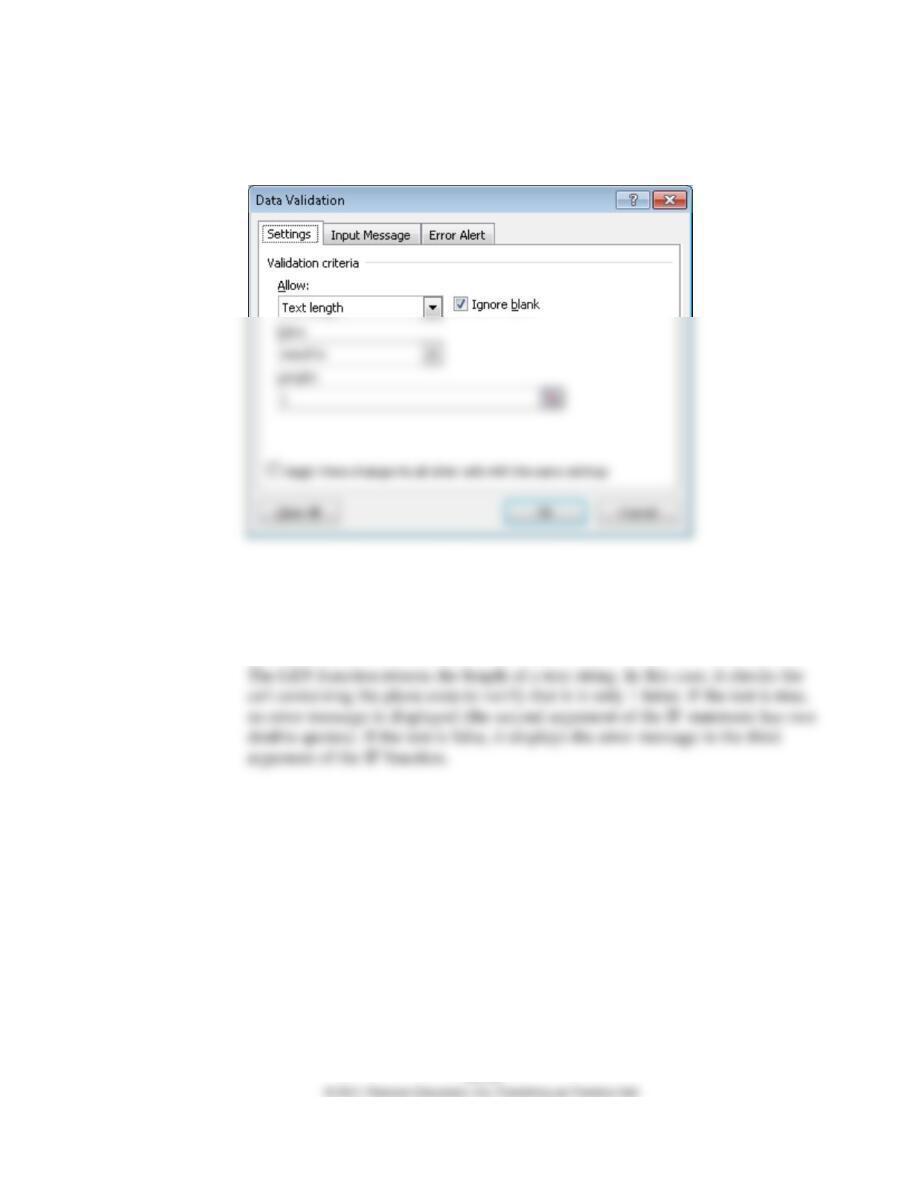
j. A visitor to the company’s Web site entered 400 characters into the five-digit Zip
code field, causing the server to crash.
A size check would prevent 400 characters from being entered into a field that allows
for only 5 characters.
k. Two traveling sales representatives accessed the parts database at the same time.
Salesperson A noted that there were still 55 units of part 723 available and
entered an order for 45 of them. While salesperson A was keying in the order,
salesperson B, in another state, also noted the availability of 55 units for part 723
and entered an order for 33 of them. Both sales reps promised their customer
next-day delivery. Salesperson A’s customer, however, learned the next day that
the part would have to be back-ordered. The customer canceled the sale and
vowed to never again do business with the company.
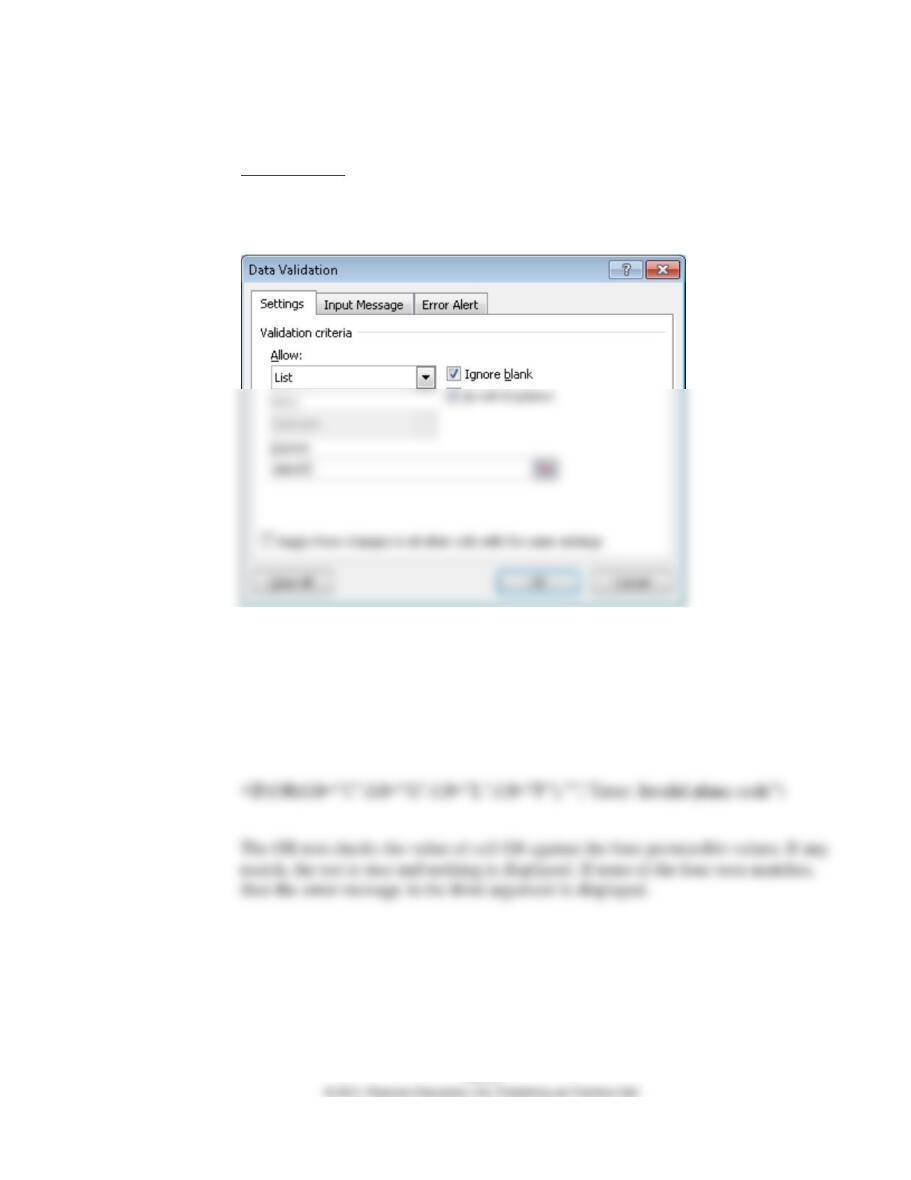
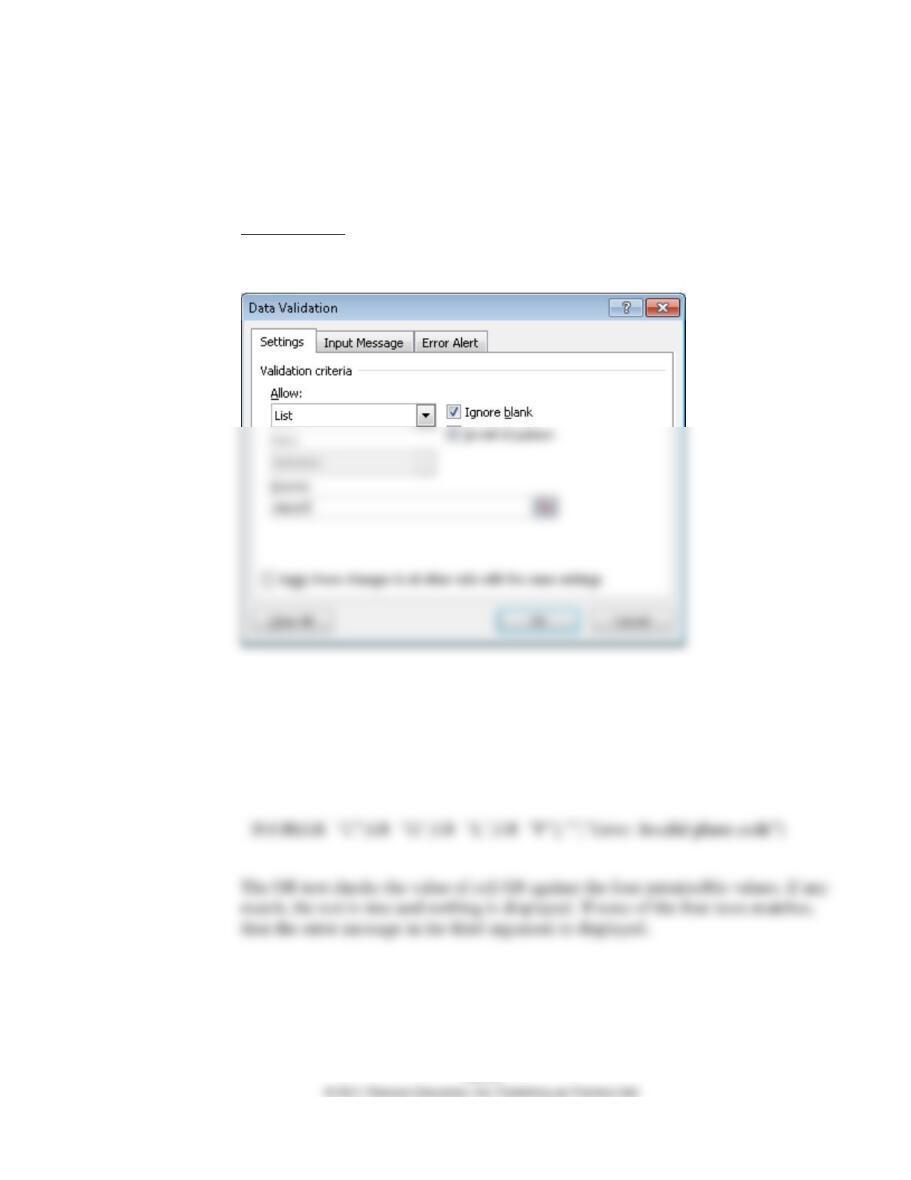
Concurrent update controls protect records from errors when more than one salesman
l. The warranty department manager was upset because special discount coupons
were mailed to every customer who had purchased the product within the past 3
years, instead of to only those customers who had purchased the product within
the past 3 months.