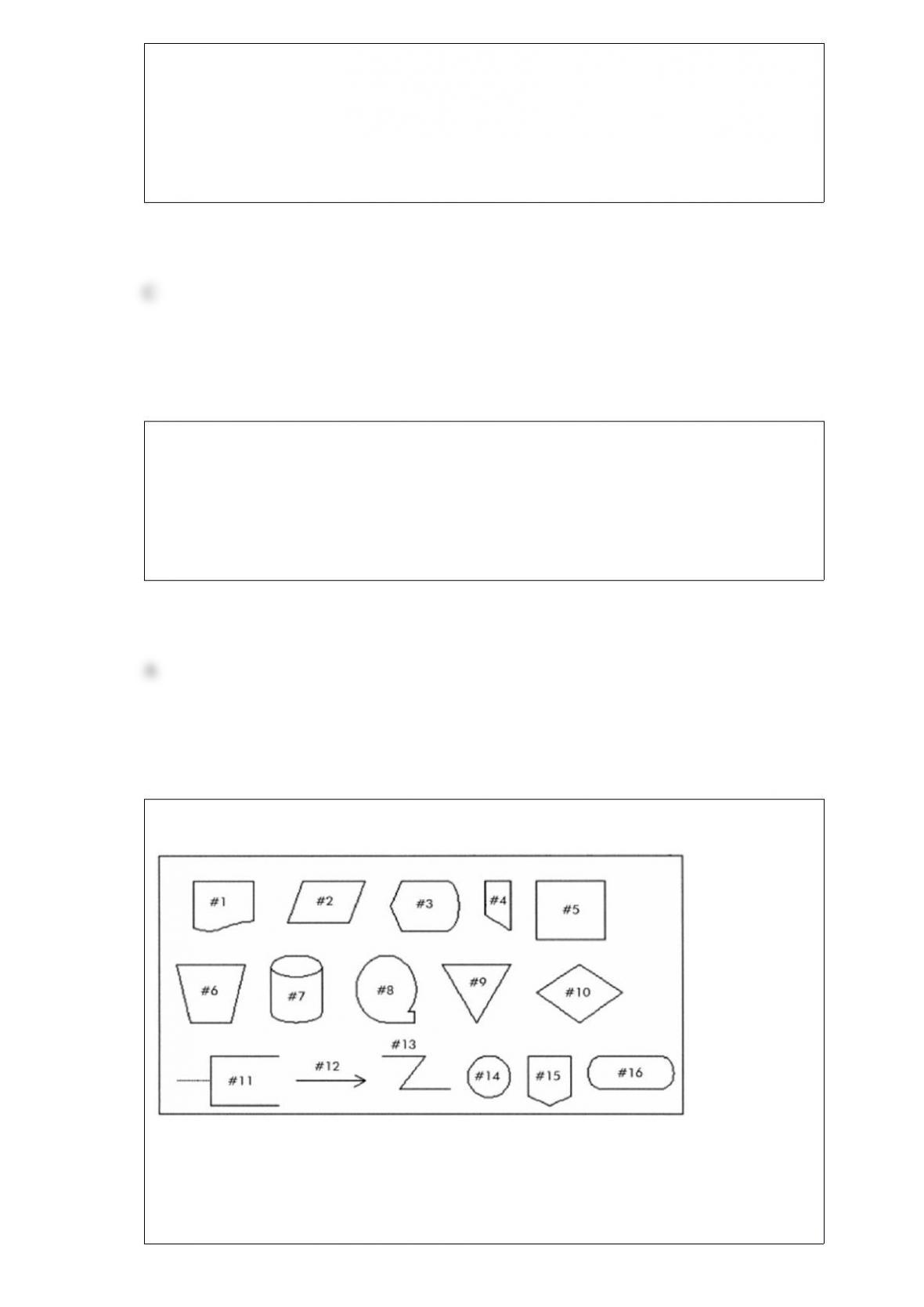
A) rectangles
B) ovals
C) diamonds
D) There is no industry standard.
A Logical model used to gather information about an existing system
A) comes only after a physical model of the existing system is created.
B) describes how a system actually works, rather than how it should work.
C) illustrates how a system functions by describing the flow of documents and
computer processes.
D) illustrates what is being done, regardless of how that flow is actually accomplished.
What is a denial of service attack?
A) It is an attack when the perpetrator is inserting malicious query in input such that it
is passed to and executed by an application program.
B) It is an attack when the perpetrator is inputting so much data that the input buffer
overflows. The overflow contains code that takes control of the company's computer.
C) It is an attack when the perpetrator uses software to guess company's addresses, send
employees blank e-mails, and add unreturned messages to spammer e-mail list.
D) It is an attacked when the perpetrator sends hundreds of messages from randomly
generated false addresses, overloading an Internet service provider's e-mail server.
During the sales order entry process, a ________ is performed to compare the quantity