13. Using HTML format for your e-mails increases your risks of receiving a virus.
14. An estimated 66% of spam circulating on the Internet is sent through botnets.
15. Bots are harder to detect than viruses or worms.
16. Software publishers often put links to software patches directly in an e-mail.
17. Bad bots were originally called remote-access Trojan horses.
18. Some worms can block users from accessing certain Web sites and can change the home page settings
of a computer.
19. A denial-of-service attack disables your antivirus software on your computer.
20. A polymorphic virus mutates by changing its signature to escape detection.
21. When you receive an e-mail about a virus, you should follow the instructions in it to protect yourself
from contracting the virus.
22. A checksum is a calculation of bytes used to identify a known virus.
23. The Windows Registry is always open, so it may not be copied by backup software without being
directed to.
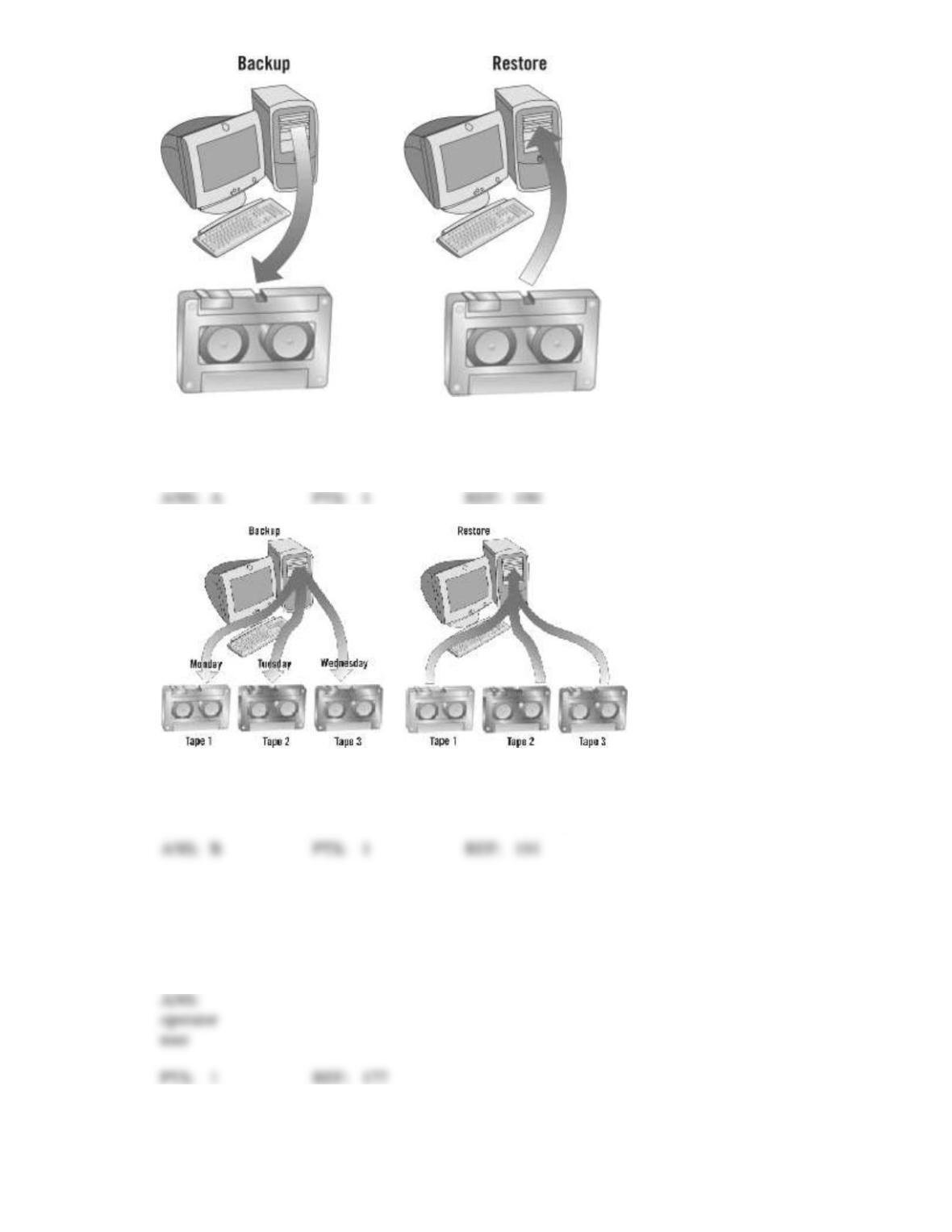
24. A full backup makes copies of every file on your computer.
25. An incremental backup makes a backup of only the files that were added or changed since your last
full backup session.