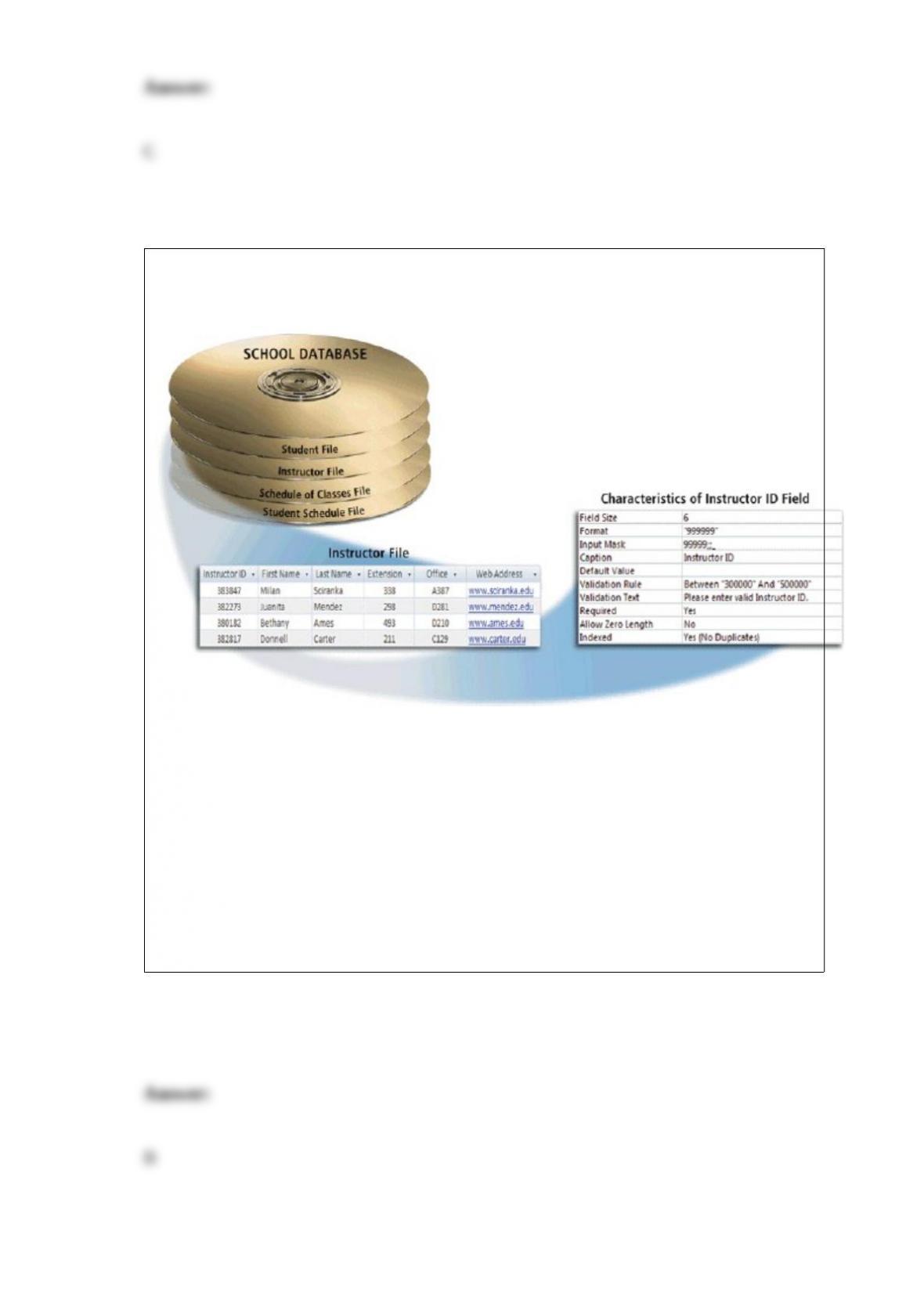
b. power mapping
c. integration
d. hot-swapping
Case 1
In your new role as a DBA, you have inherited a database that has a lot of problems.
Your first task, you decide, is to identify the qualities of the information in your
database, or, in some unfortunate cases, the absence of these qualities.
The manager for the eastern division sales force is upset because she wants to
determine which members of her sales force need awards for high monthly sales, and
which employees need remediation because they have not sold enough product during
the past month. However, all of the sales information has not yet been entered into the
database. What kind of information is at issue in this instance?
a. useful information
b. accessible information
c. timely information
d. verifiable information