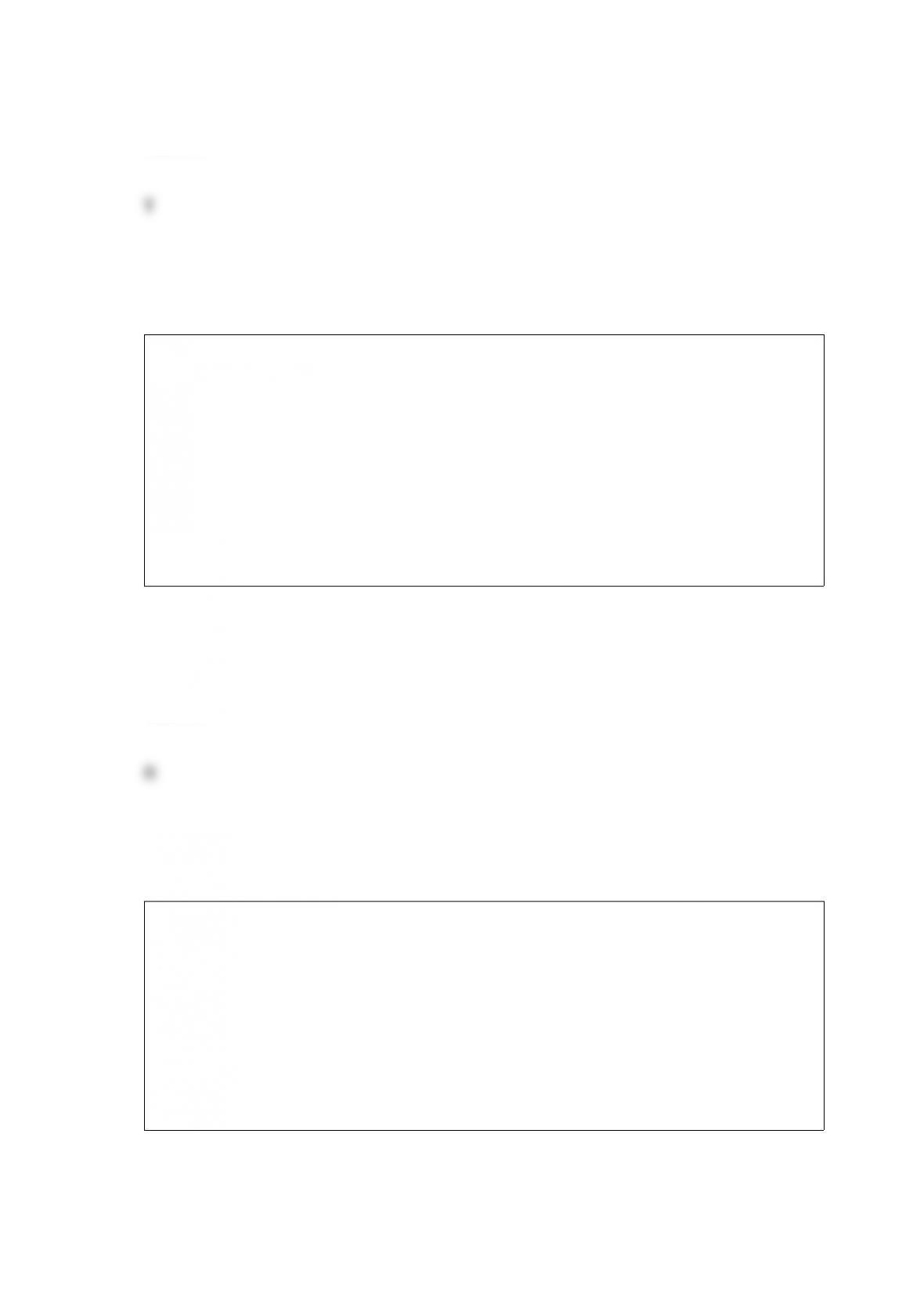
17) ______ output controls
18) ______ security policy
19) ______ eavesdropping
20) ______ computer facility controls
21) ______ application controls
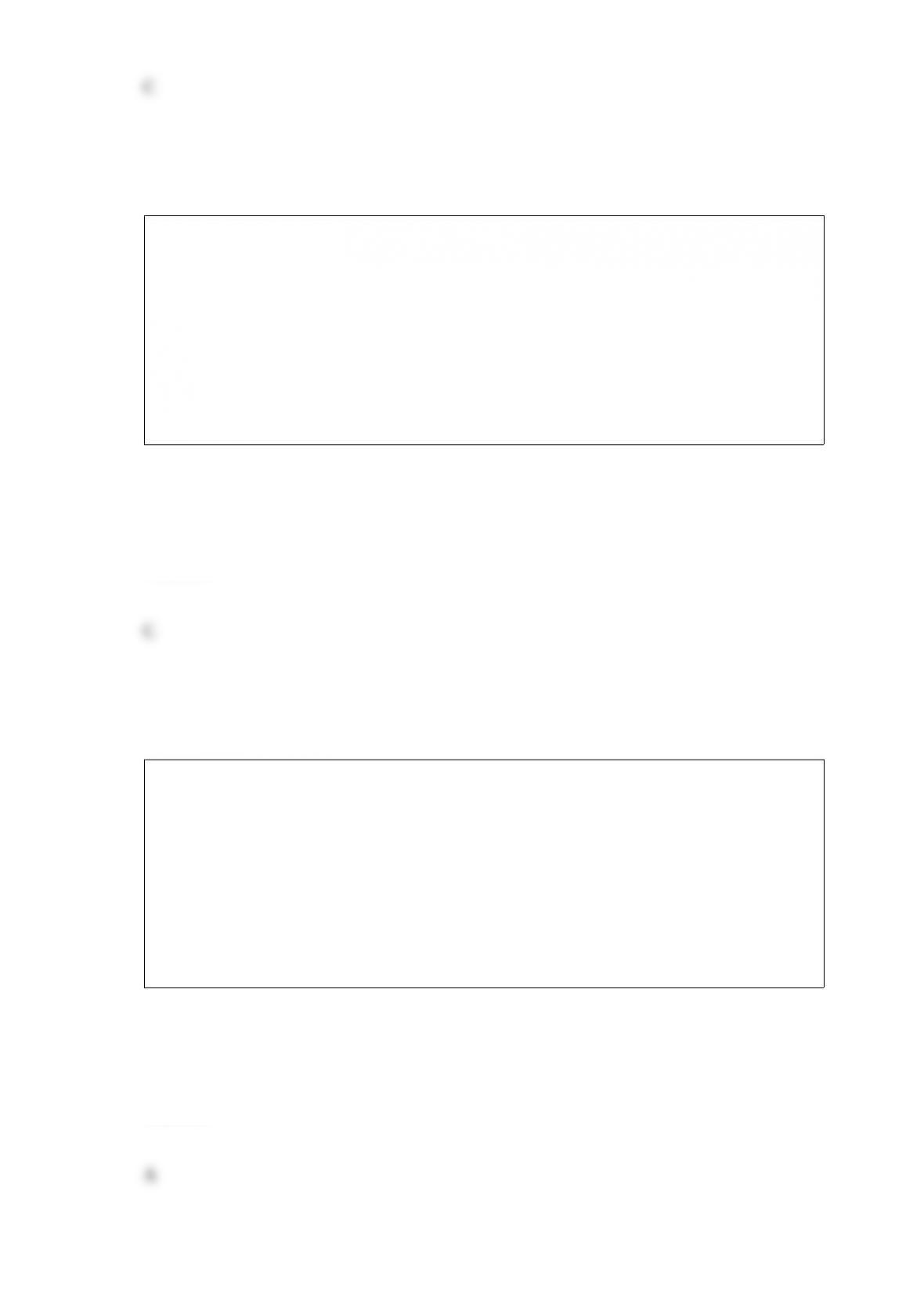
Definitions:
A. Enable computer systems to deal with errors and keep functioning, and is often
based on the concept of redundancy
B. This control limits only authorized individuals access to the organization's systems
and information
C. The purpose of this control is to securely transmit data to a remote site
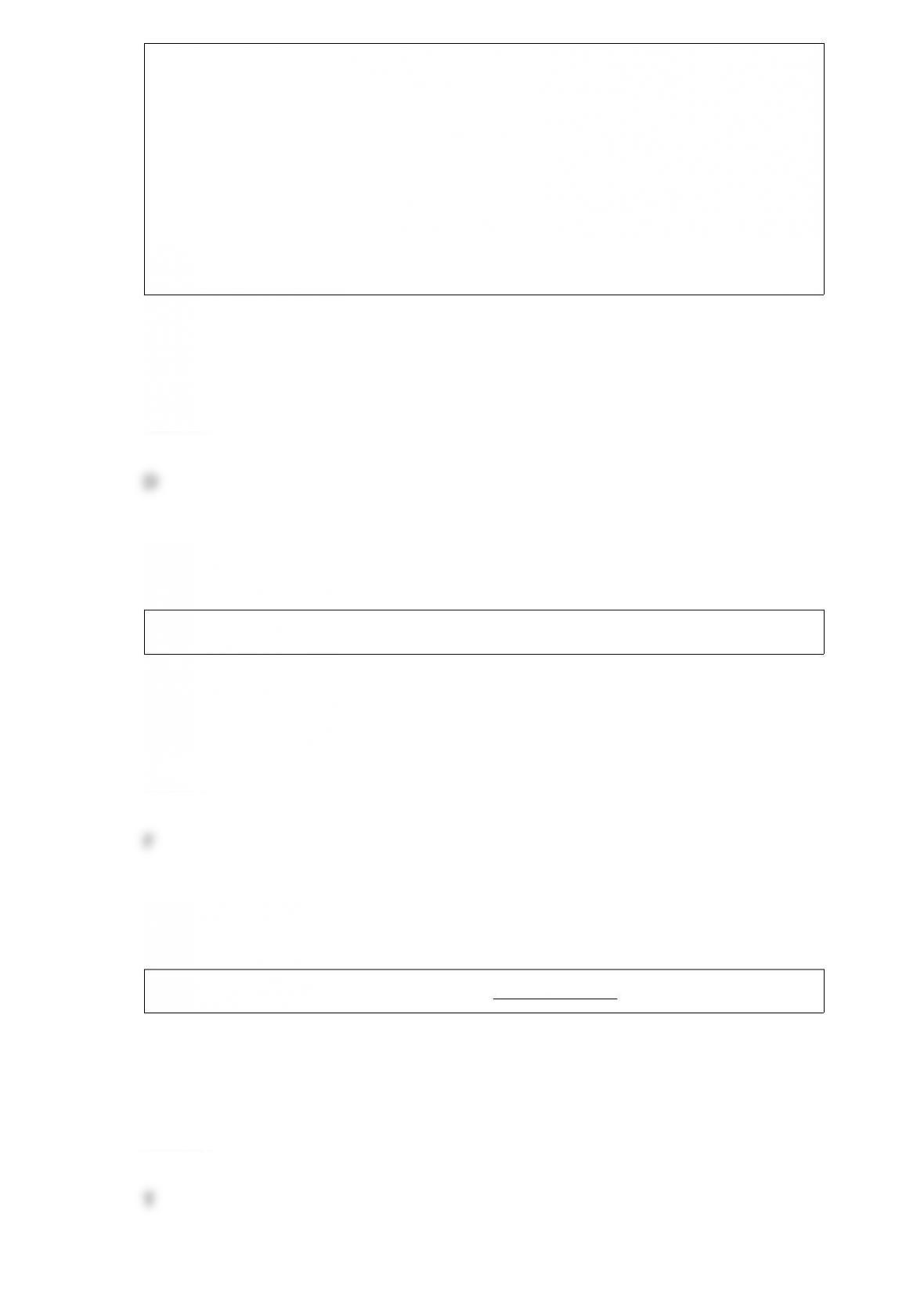
D. A disaster recovery site that hasa computer system with capabilities similar to the
system it will replace and also has up-to-date backup data
E. Certain behaviors exhibited by employees that can alert co-workers and supervisors
to trouble (i.e., fraud)
F. Acomprehensive plan that helps protect an enterprise from both internal and external
threats
G. A process whereby management identifies possible events that represent a problem
to the firm and then identifies appropriate responses to those problems
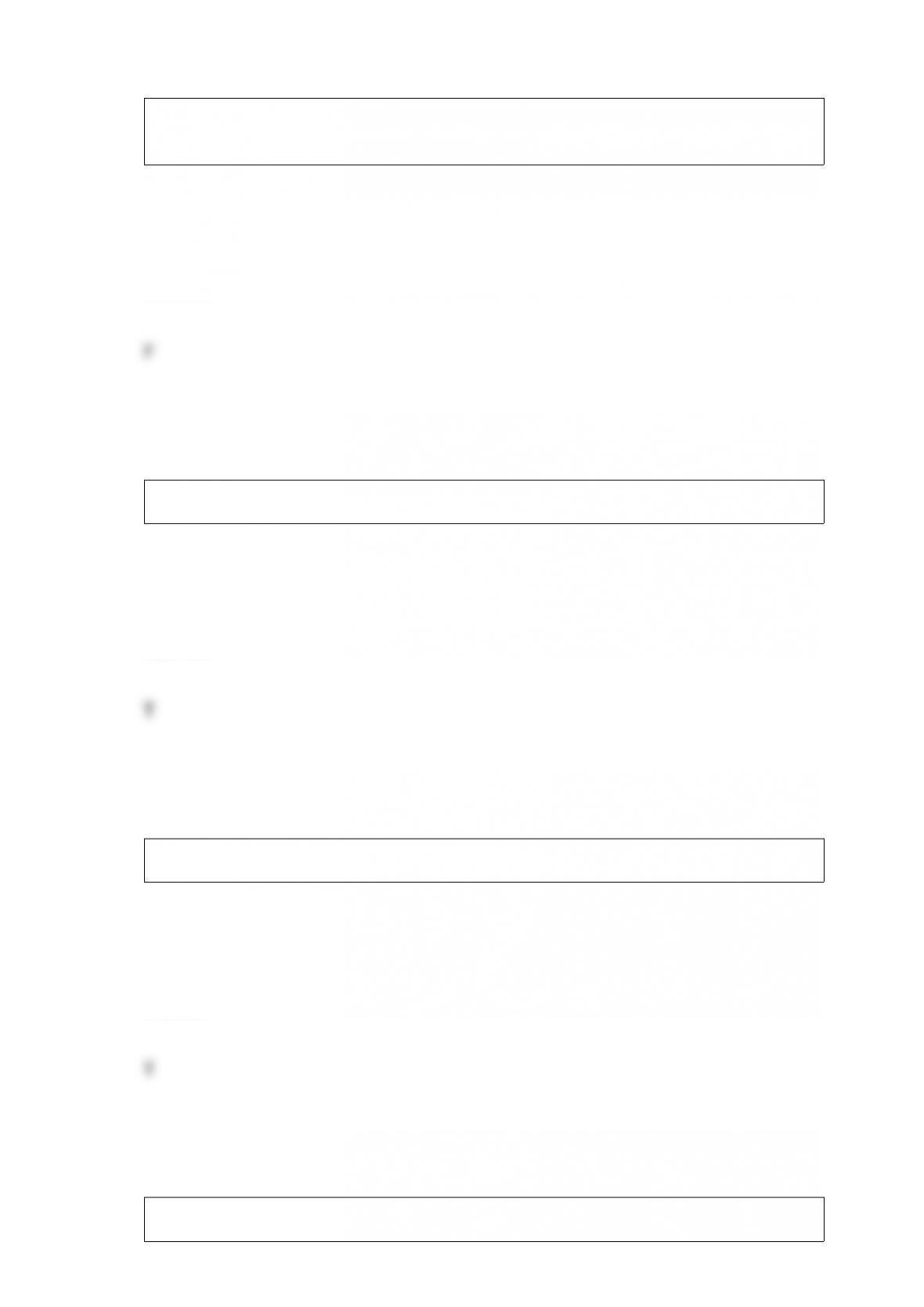
H. A disaster recovery site that hasa computer system with capabilities similar to the
system it will replace
I. A comprehensive approach to making sure organizational activities continue normally
J. An example of this type of control is a "man trap"
K. When organizations combine a number of logical and physical security technologies
(i.e., firewalls, intrusion detection systems, virus protection)
L. Any measures that an organization uses to protect its facilities, resources, or its
proprietary data that are stored on physical media
M. The process and procedures that organizations follow to resume business after a
disruptive event such as an earthquake, a terrorist attack, or a serious computer virus
N. Disaster recovery site that has power, environmentally controlled space, and
processing equipment that can be installed on short notice