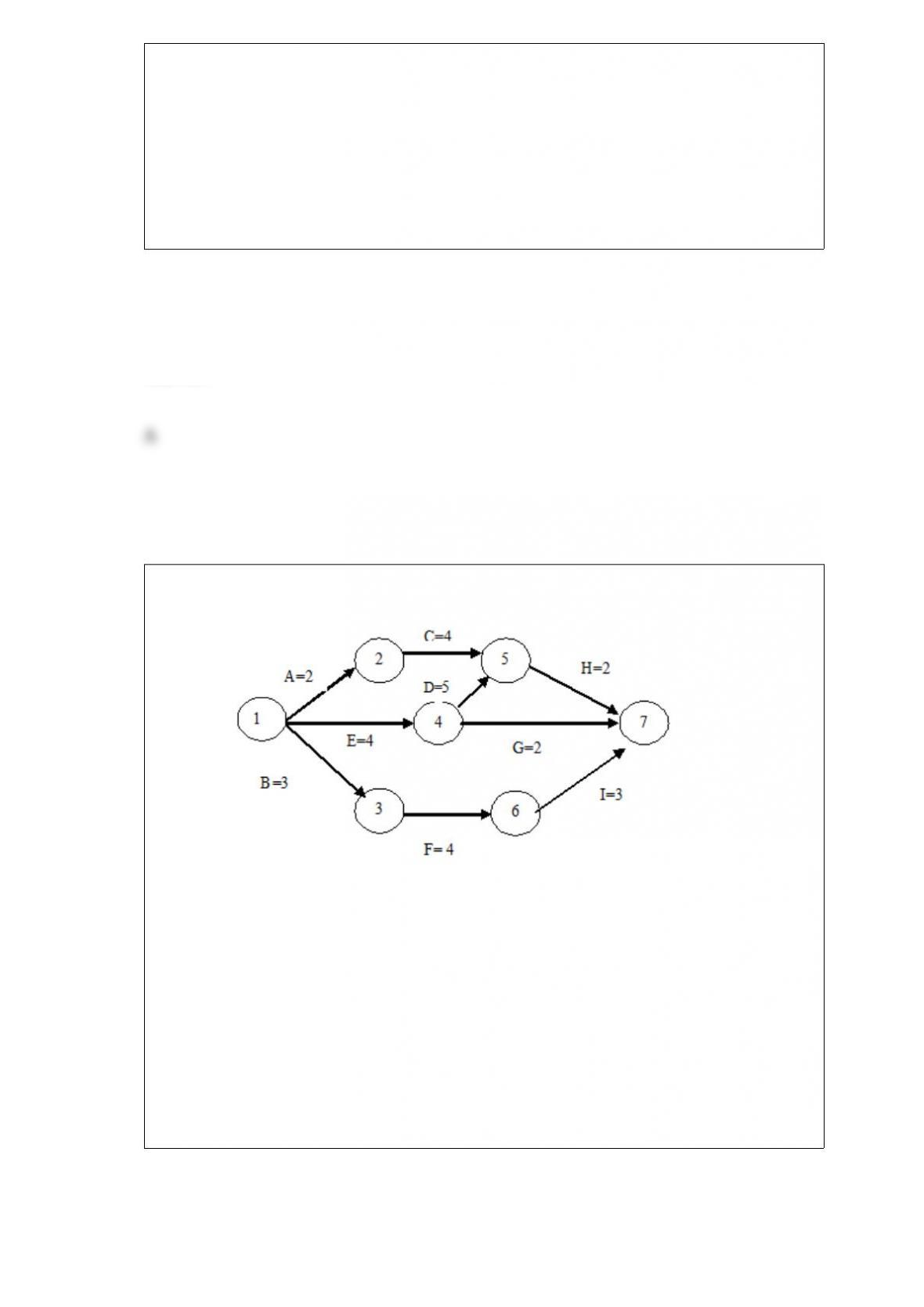
Answer:
What is the main reason why companies prefer VANs to the Internet for implementing
EDI?
a) Cost - VANs are cheaper than the Internet
b) Speed - VANs are faster than the Internet
c) Security - VANs are thought to be more secure
d) Convenience - VANs are everywhere
Answer:
Networked enterprises and globalization have enabled a new business model called
"business-without-boundaries." Which of the following statements describes this
business model?
a) Companies no longer have all of their employees in one location
b) It is called offshoring and companies contract with firms in other countries to do
such business processes as human resources, payroll, and accounting
c) Companies are under a great deal of scrutiny to manage costs and generate revenue
so they contract with foreign firms to do various business processes at a lower cost to
the company
d) all of the above statements describe this model