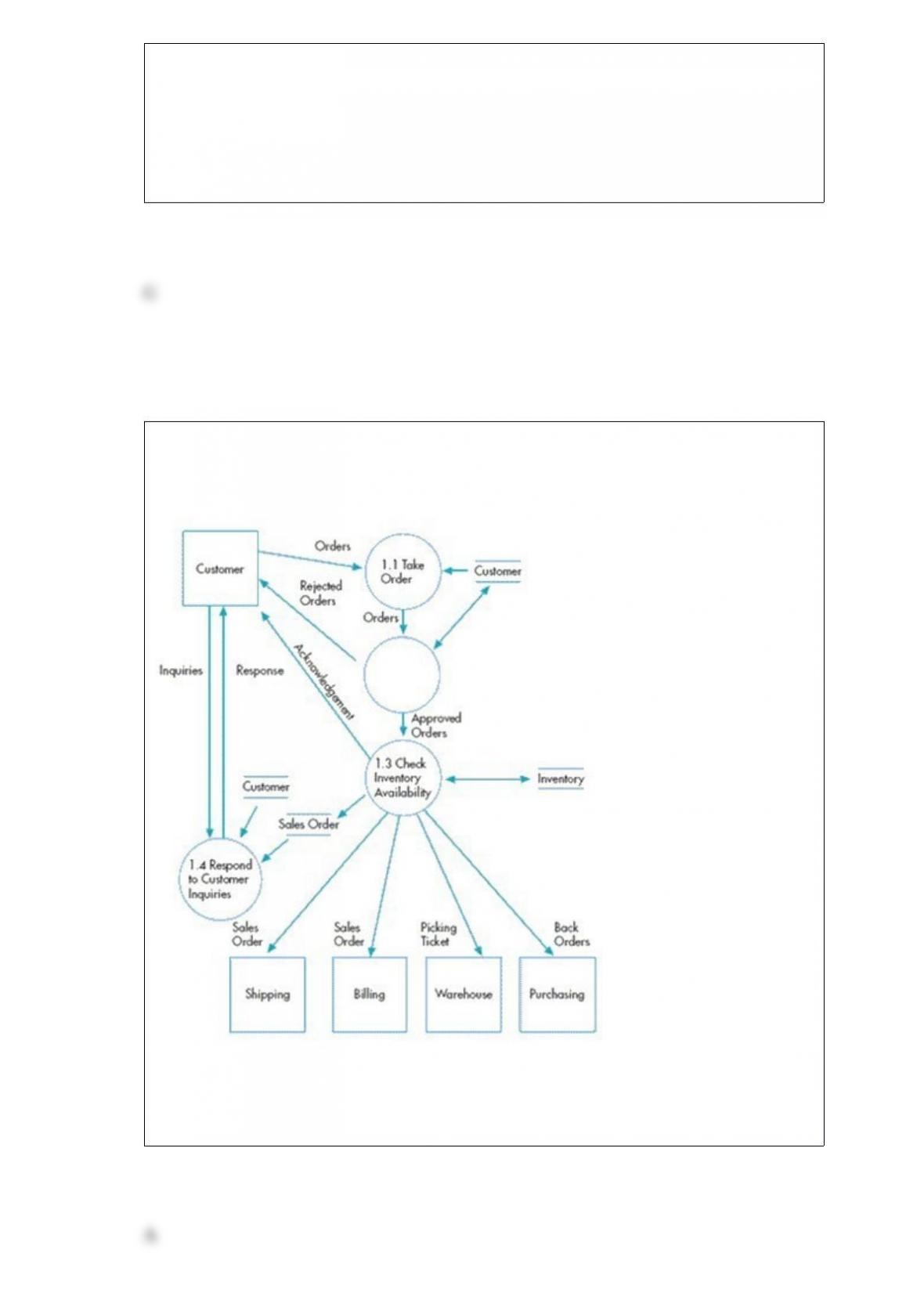
Whitewater Rapids provides canoes to tourists eager to ride Whitewater River's rapids.
Management has determined that there is one chance in a thousand of a customer being
injured or killed. Settlement of resulting lawsuits has an average cost of $850,000.
Insurance with a $100,000 deductible is available. It covers the costs of lawsuits, unless
there is evidence of criminal negligence. What is the impact of this risk without
insurance?
A) $10
B) $850
C) $100,000
D) $850,000
At a movie theater box office, all tickets are sequentially prenumbered. At the end of
each day, the beginning ticket number is subtracted from the ending number to calculate
the number of tickets sold. Then, ticket stubs collected at the theater entrance are
counted and compared with the number of tickets sold. Which of the following
situations does this control detect?
A) Some customers presented tickets purchased on a previous day when there wasn't a
ticket taker at the theater entrance (so the tickets didn't get torn.)
B) A group of kids snuck into the theater through a back door when customers left after
a show.
C) The box office cashier accidentally gives too much change to a customer.
D) The ticket taker admits his friends without tickets.
Inability to add new data to a database without violating the basic integrity of the
database is referred to as the
A) update anomaly.
B) insert anomaly.
C) integrity anomaly.
D) delete anomaly.