What is a key decision that needs to be made with regards to selling merchandise?
A) which banking institution to use
B) which employees to hire
C) which public accounting firm to employ
D) which credit cards to accept
Helge Autoparts sells new and refurbished auto parts exclusively to auto dealers. Helge
purchases inventory from distributors at trade conventions. Each time Helge makes a
purchase, the company records the suppliers name, address, date, specific items
purchased, price paid for each, and the total amount spent. Helge later researches the
inventory items to set the customer price. The company assigns an inventory number to
each item purchased and records the customer price for each item. Helge buys price
tags and display supplies from Alwin Incorporated, a company that sells them at all
trade conventions. All inventory and supplies purchases are immediately paid for with
cash or with checks from a bank account in Helge's name. All cash received from sales
are also deposited to the same bank account. Several times a year Helge rents display
space at dealer conventions. A deposit is always required, and the entire fee is due the
day the convention starts. Helge records the deposit and final payment, along with the
convention's name and address, in the same worksheet on which purchases of inventory
and supplies are recorded.
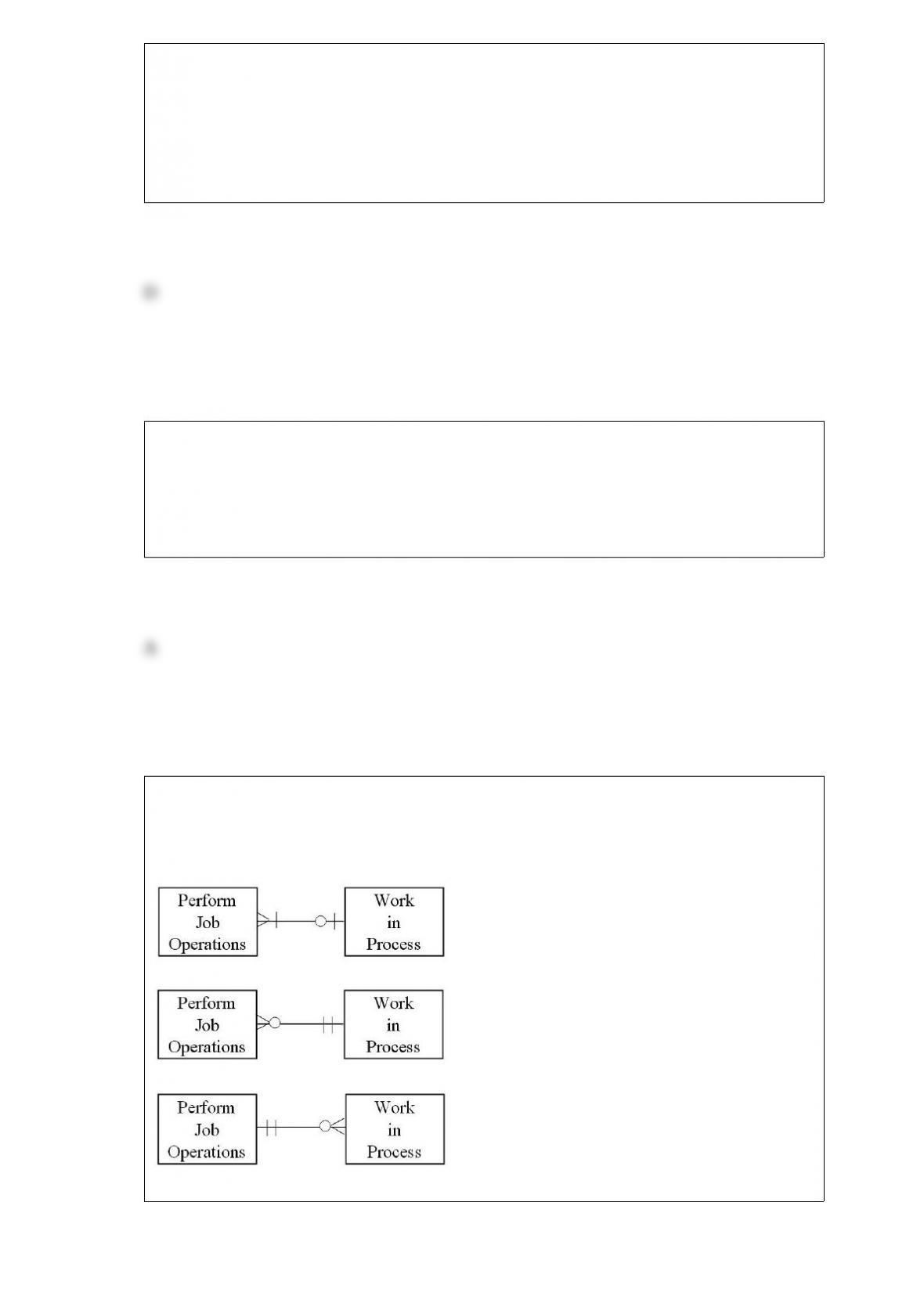
Consider Helge's processes regarding the purchasing inventory and supplies, renting
display space, and paying for purchased items. A well-designed REA diagram would
A) reflect minimum cardinalities of 1 for the relationship between Vendor and Cash
Disbursement entities.
B) reflect the same number of 0 and 1 minimum cardinalities.
C) reflect more maximum cardinalities of M than of 1.
D) reflect maximum cardinalities of M for the relationship between Inventory and
Purchase entities.
Which of the following is a financial pressure that could cause an employee to commit
fraud?
A) A feeling of not being valued.
B) Having a grumbling and drug addiction.