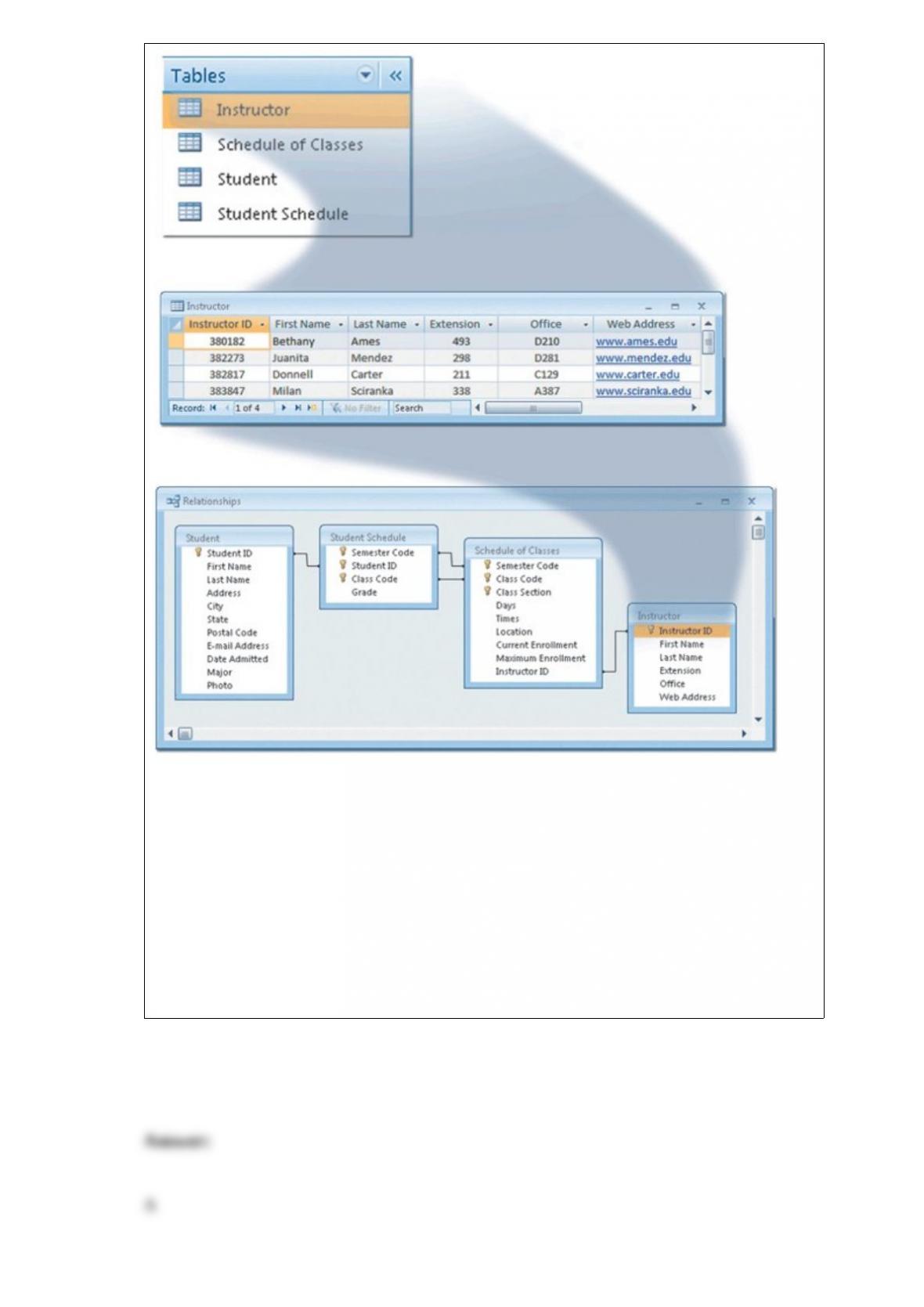
In your work in the IT department, you are charged with asking the difficult questions
about the feasibility of new systems as they are being developed.
Knowing that you are an expert on feasibility assessment, a colleague has come to you
for advice on an issue of schedule feasibility. His project deadline has been adjusted
twice before and cannot be extended again. What is an option for him?
a. Creating a new schedule
b. Reducing the project scope
c. Increasing the project creep
d. Performing a payback analysis
With ____, users access account balances, pay bills, and copy monthly transactions
from a bank's computer right into their personal computers.
a. online investing
b. online banking
c. neural networks
d. All of the above
Unless otherwise specified by a license agreement, users do not have the right to ____