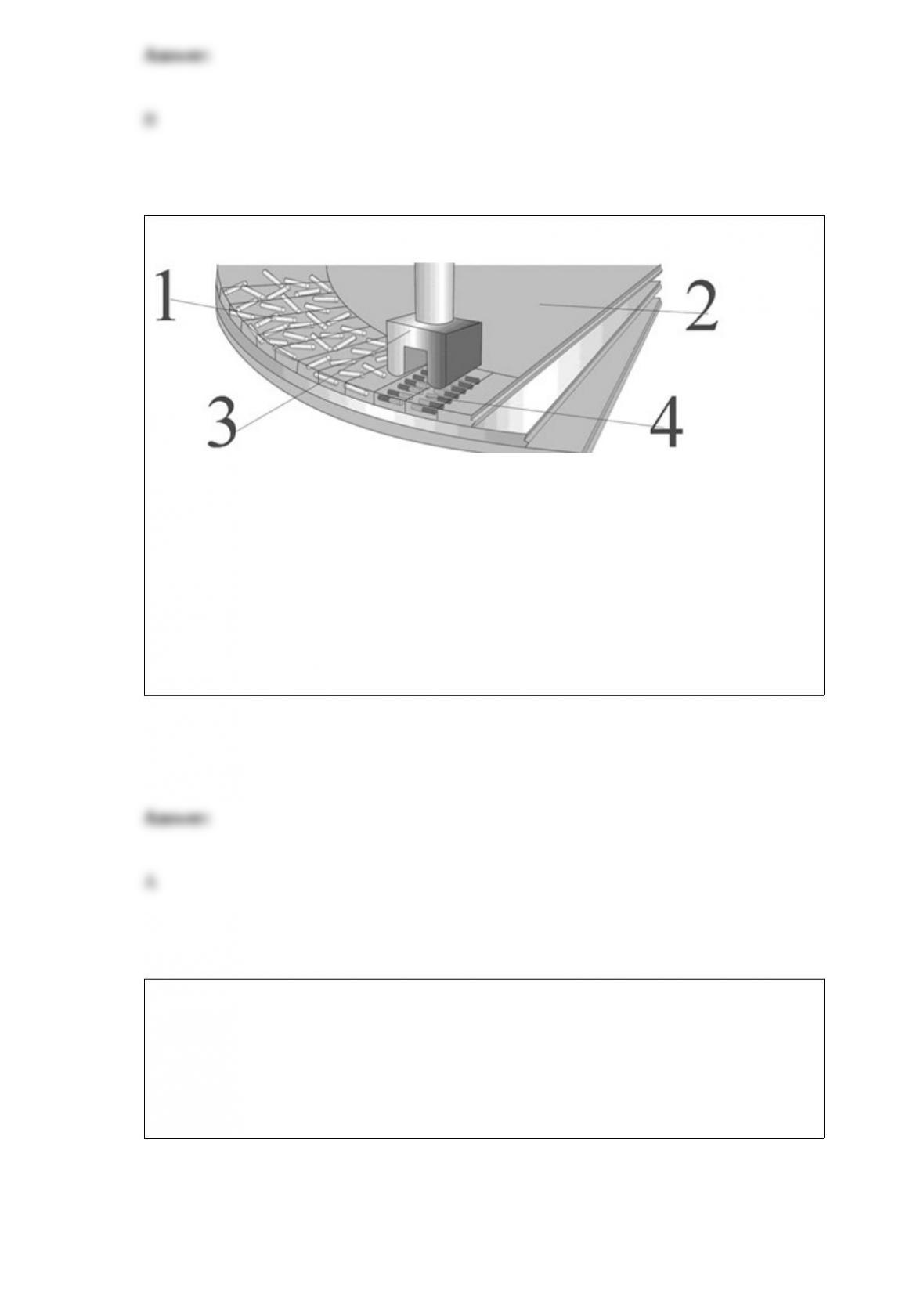
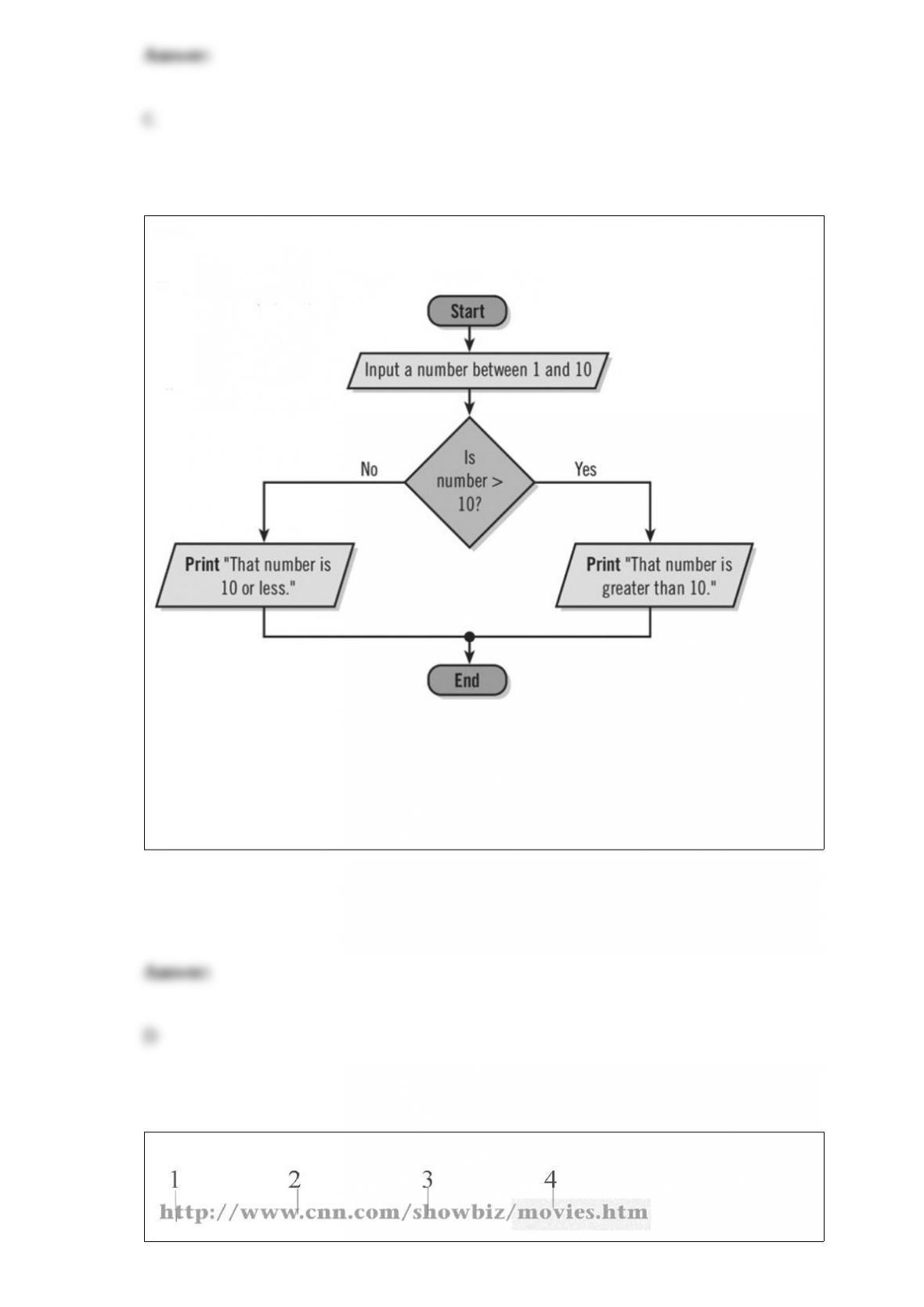
What does a Compact Privacy Policy do?
a. Blocks a company from installing cookies on your computer.
b. Describes how cookie data is used by a Web site.
c. Encrypts credit card information in a secure connection.
d. Acts as a contract between a consumer and a business for e-commerce purchases.
____ analytics focus on anticipating future probabilities and trends.
a. Data cubing c. Classification
b. Predictive d. OLAP
Which of the following is NOT true about USB ports?
a. Most computers only have one.
b. Mice, scanners, and joysticks can be used in USB ports.
c. USB ports can support storage devices.
d. Windows recognizes most USB devices when they are plugged into the port.