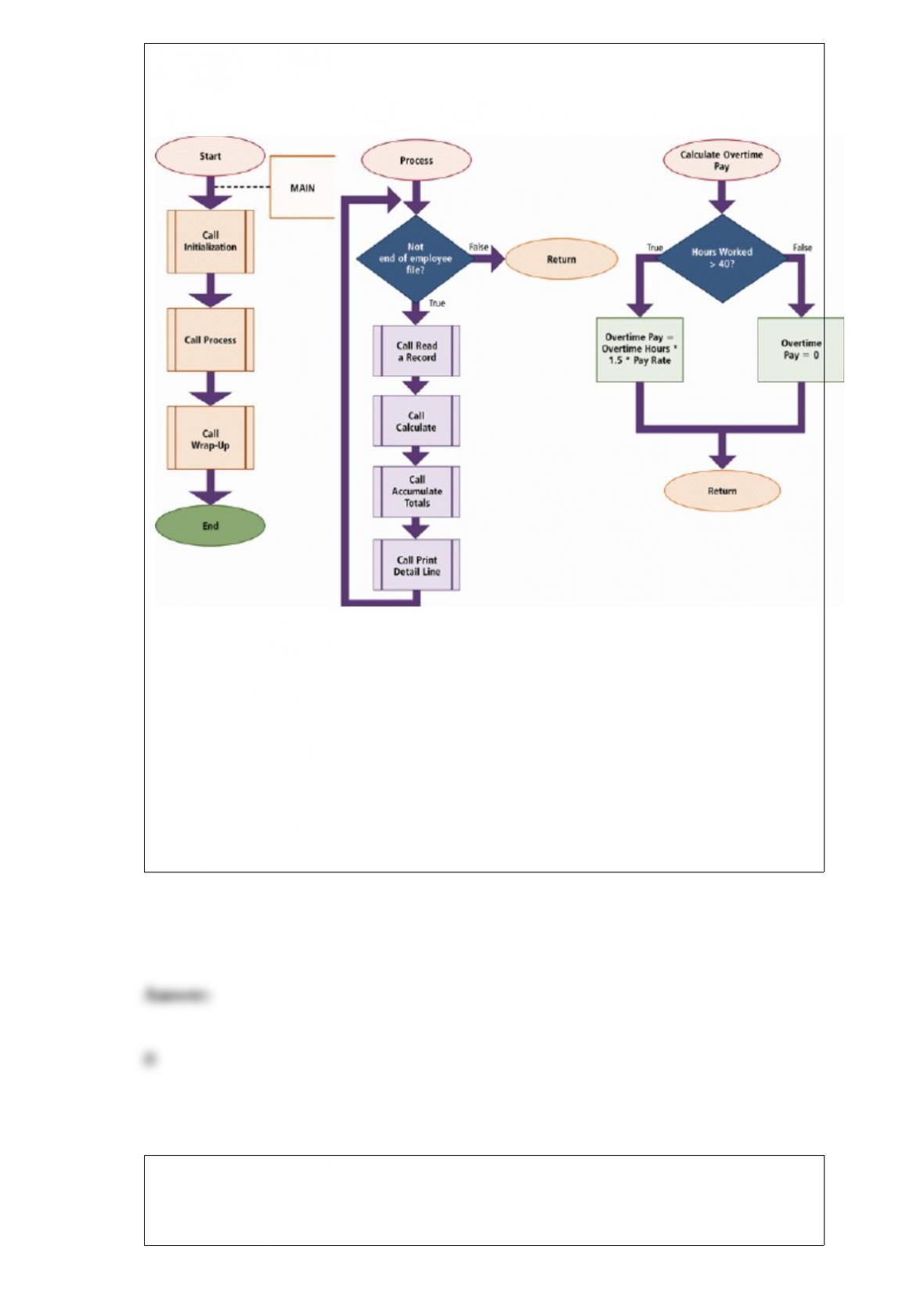
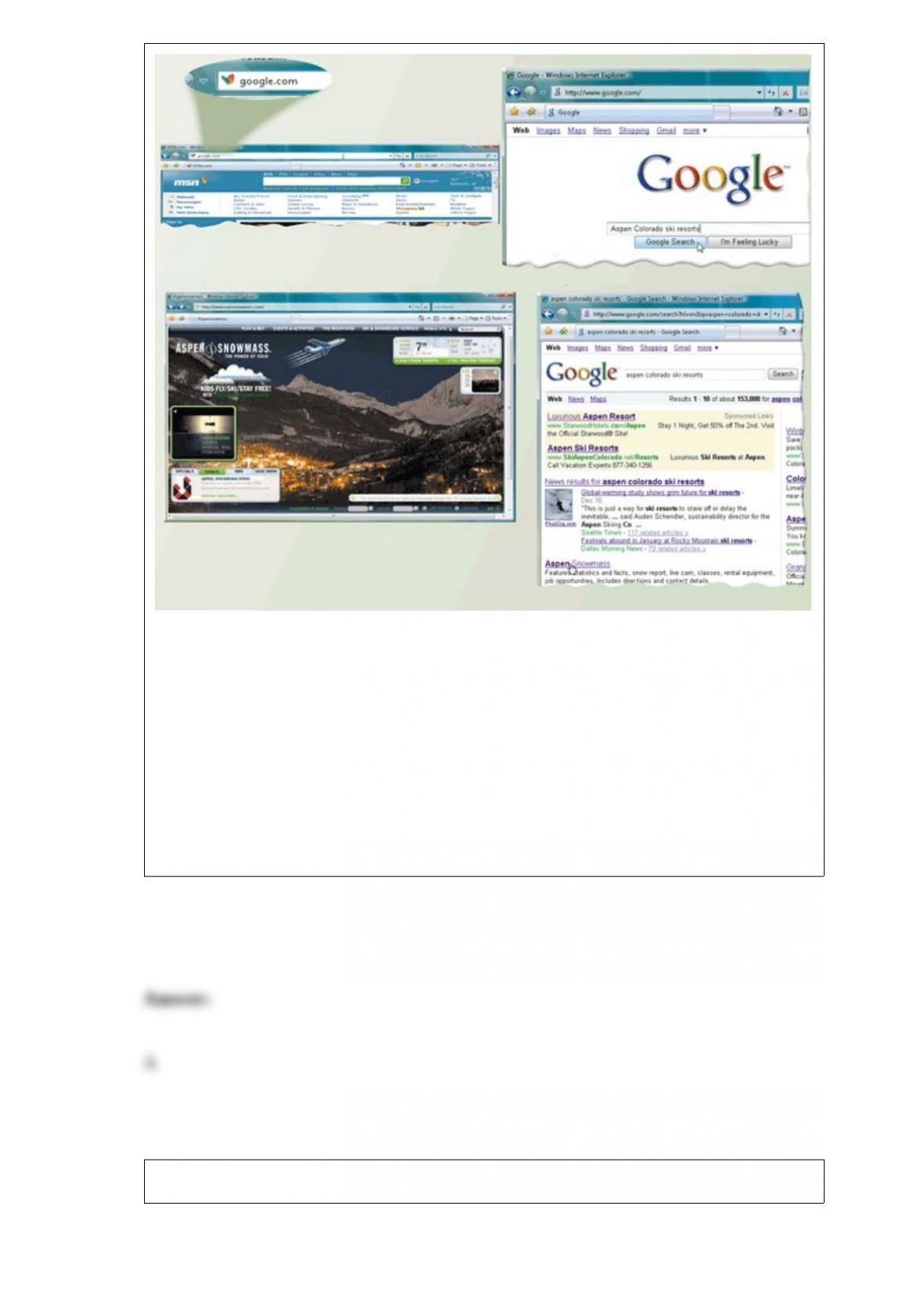
With a(n) ____, users choose which folders and files to include in a backup.
a. full backup
b. incremental backup
c. differential backup
d. selective backup
Case 2
In your introductory course on computers, your professor has decided to dedicate a
lecture to computer ethics. There is a lot of ambiguity in this topic, and she has
presented a range of circumstances for you and your classmates to review.
Which is NOT an issue surrounding the concept of fair use, from copyright law?
a. The right of students to post their own term papers on the Web.
b. The rights of a faculty member to print material from the Web and distribute it to the
members of her class for instructional purposes.
c. The use of an anonymizer program to surf the Web anonymously.
d. The rights of individuals to download contents of your Web site, modify it, and then
put it on the Web again as their own.