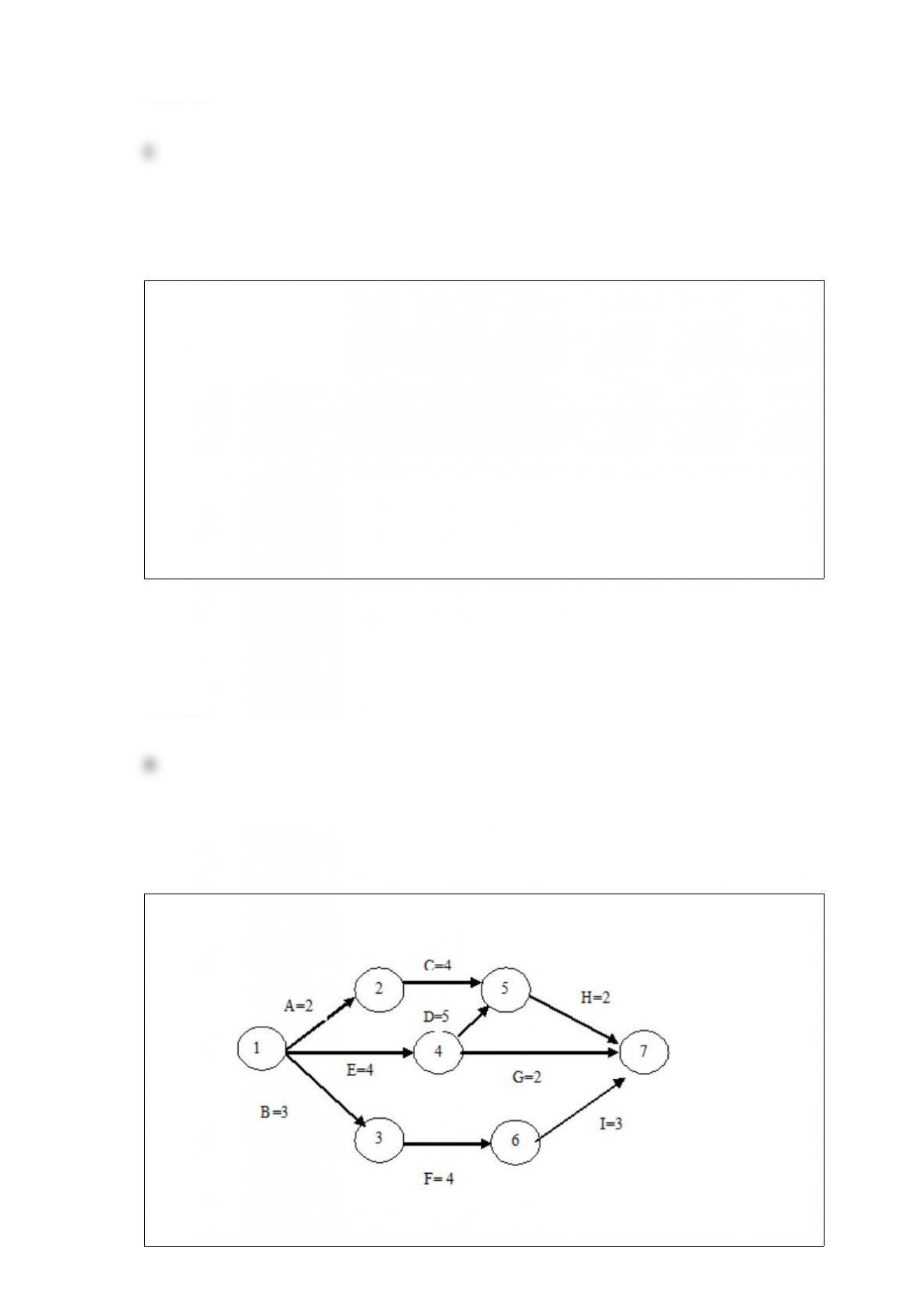
D. A markup language designed specifically for businesses and financial reporting
E. A transmission protocol enabling users to send voice-grade messages over the
Internet
F. A transmission protocol used to send email messages sent over the Internet
G. An activity designed to steal a person's financial identity
H. An authenticating document issued by a third party called a certificate authority
I. An encryption standard used by the U.S. government
J. An extension of HTML that allows users to create their own markup tags
K. Inflating the number of uses of a link to an alternate website
L. Software typically used for web conferencing
M. The exchange of electronic documents such as contracts
N. The markup language typically used to display web pages in a web browser
Answer:
The most important factor in planning for a major change in a computer-based system
is:
a) The organization of the IT department
b) The ability of the systems programmers to write appropriate software
c) The selection of the most advanced computer equipment
d) Giving the systems people a free hand in all changes
e) The participation of top management in the planning process