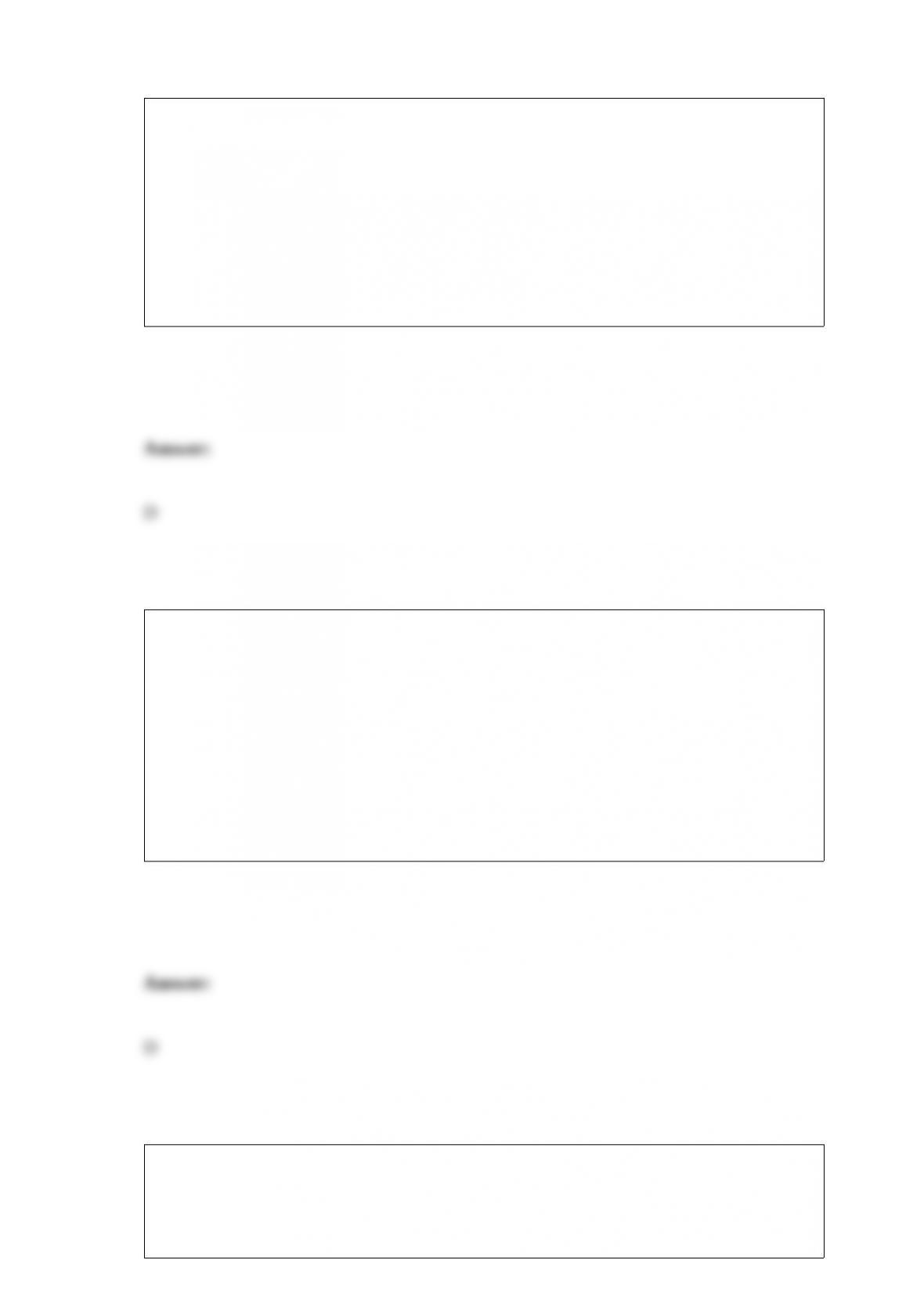
To limit the number of rows retrieved from a table, use the SQL construct ________.
A) SELECT *
B) SELECT TOP n *
C) SELECT COUNT(TOP n)
D) SELECT COUNT(*)
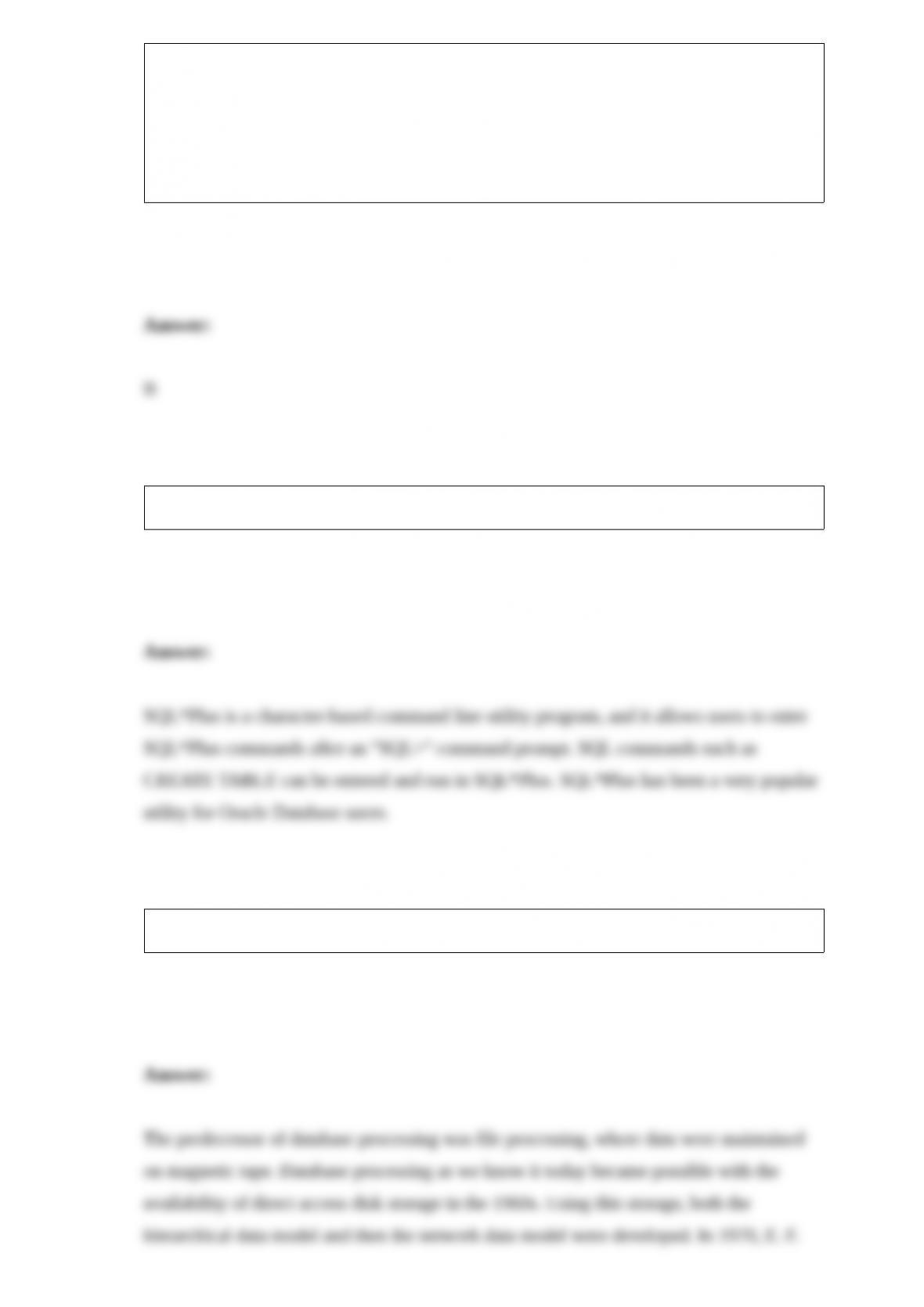
If T3 is a table with three columns C1, C2, and C3, where C1 is integer data, C2 is
character data, and C3 is date data, which of the following would be the proper
statement to have Oracle Database enter the date 02/10/03 into a row in table T3 while
making sure that it is formatted correctly as shown?
A) SET INTO T3 VALUES (101, 'Smith', '02/10/13');
B) SET INTO T3 VALUES (101, 'Smith', TO_DATE ('02/10/13', 'DD/MM/YY'));
C) INSERT INTO T3 VALUES (101, 'Smith', '02/10/2013');
D) INSERT INTO T3 VALUES (101, 'Smith', TO_DATE ('02/10/13', 'DD/MM/YY'));
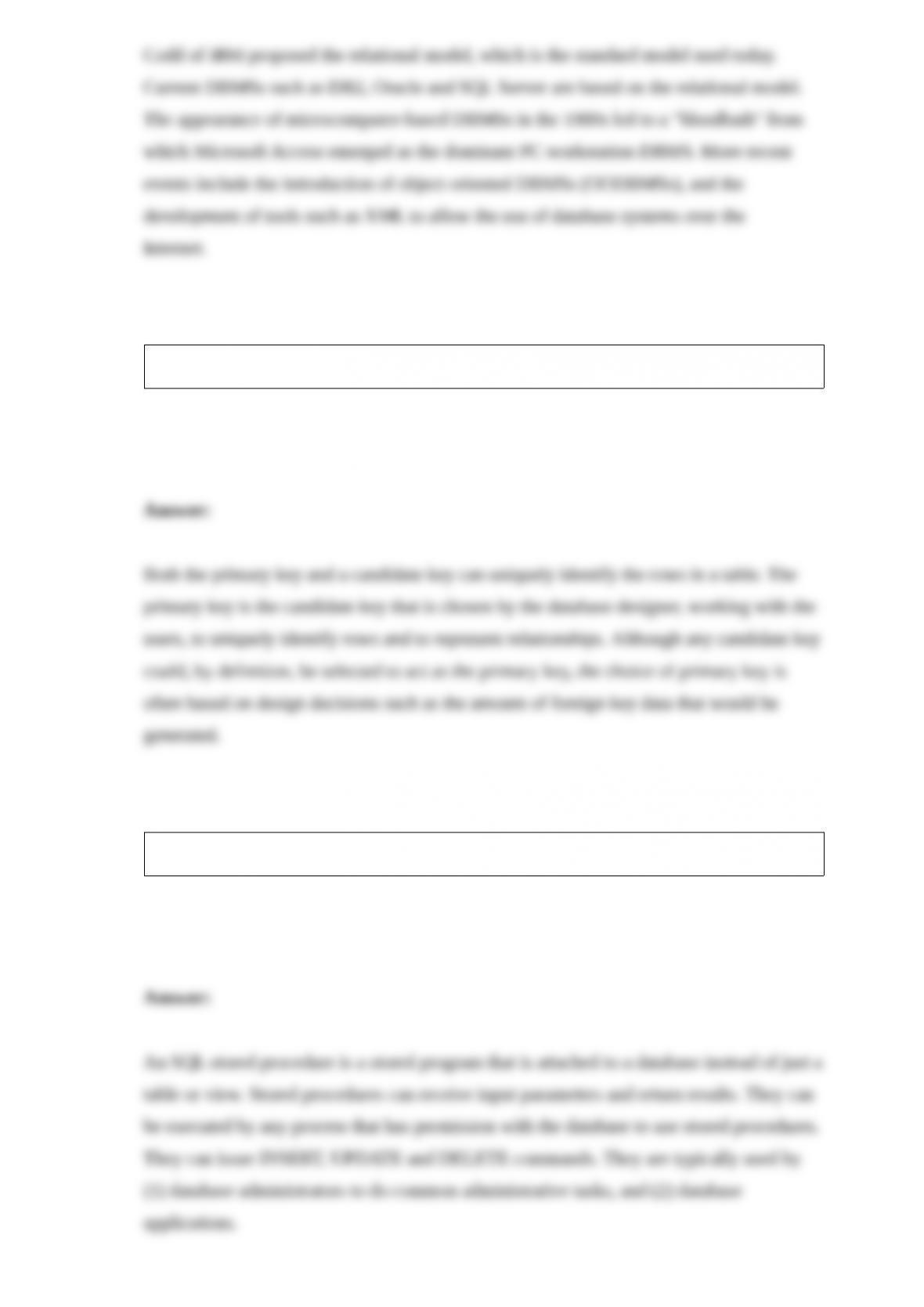
Having to enter facts about two entities when we want to enter facts about only one is
an example of ________.
A) insertion anomaly