The primary objective of accounting is to
A) implement strong internal controls.
B) provide useful information to decision makers.
C) prepare financial statements.
D) ensure the profitability of an organization.
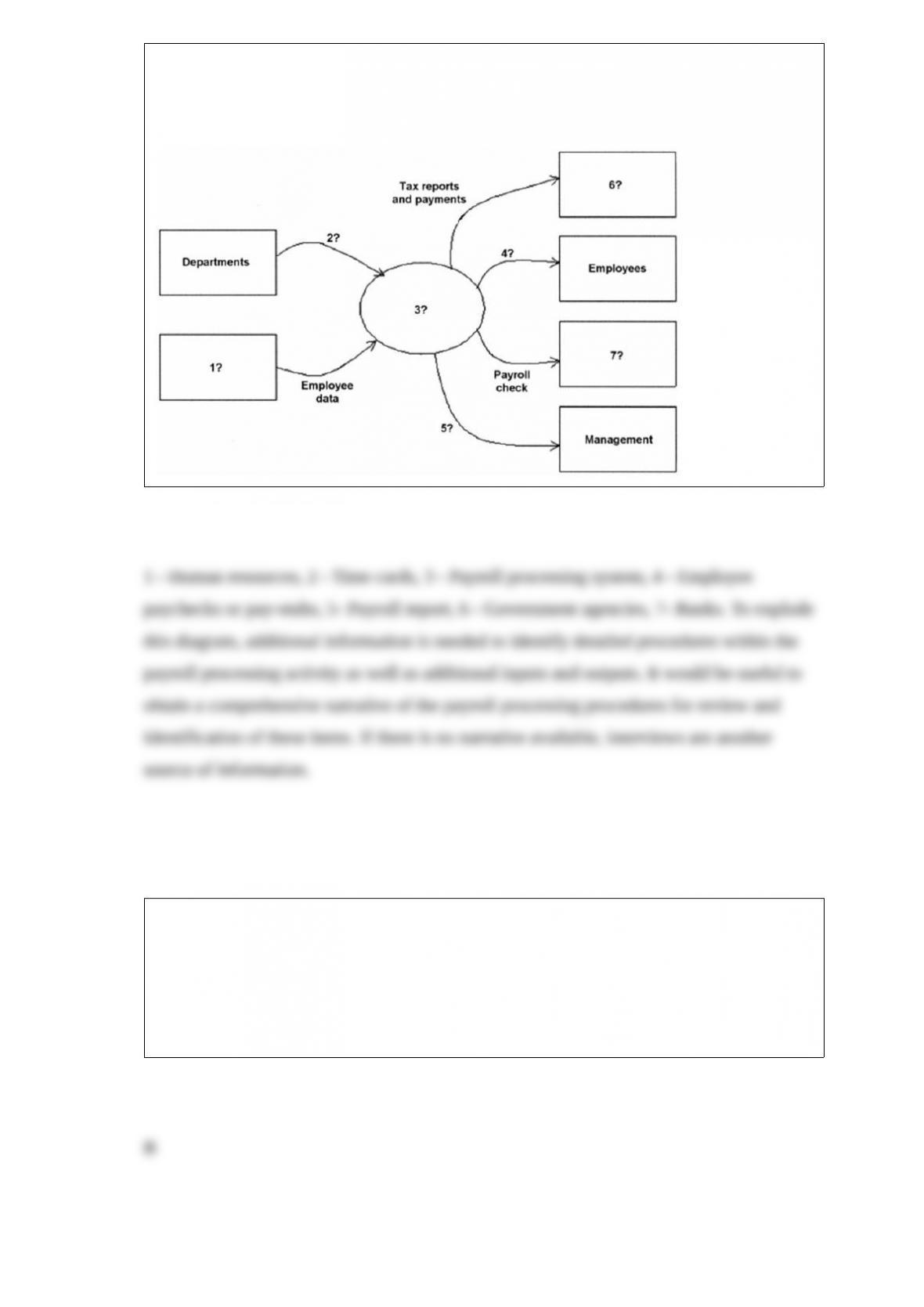
A workforce inventory report
A) is filed each quarter to reconcile monthly tax payments with total tax liability for the
quarter.
B) is used in preparing labor-related reports for government agencies.
C) is used for employee information and annual payroll reports.
D) is used to document compliance with applicable regulations.
The ________ is the basic building block of information systems planning.
A) master plan
B) project development plan
C) systems analysis plan
D) implementation plan
A query that extracts, for a given time period, all purchases for which there is no
corresponding disburse cash event will yield
A) a cash account ledger.
B) a credit sales journal.