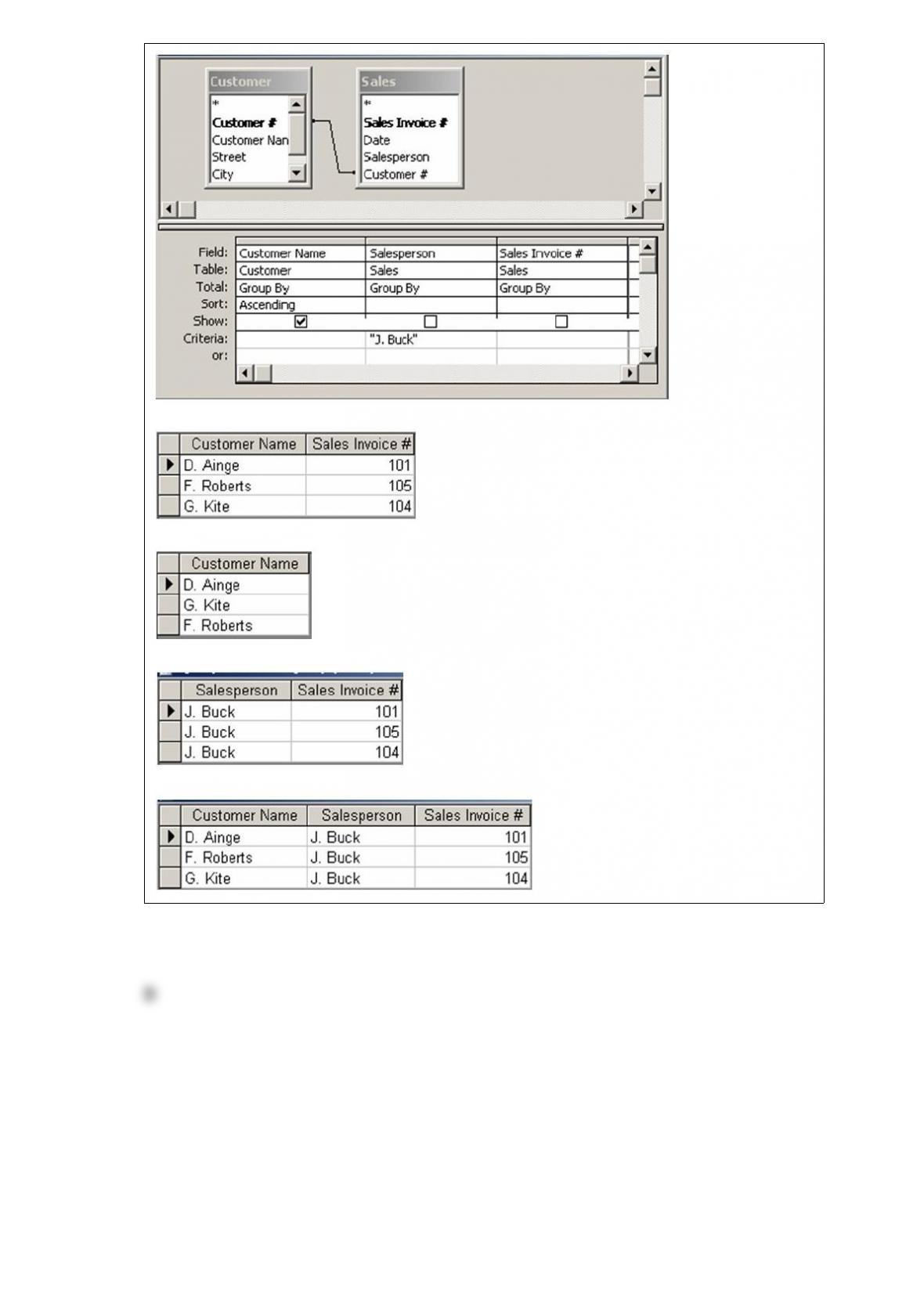
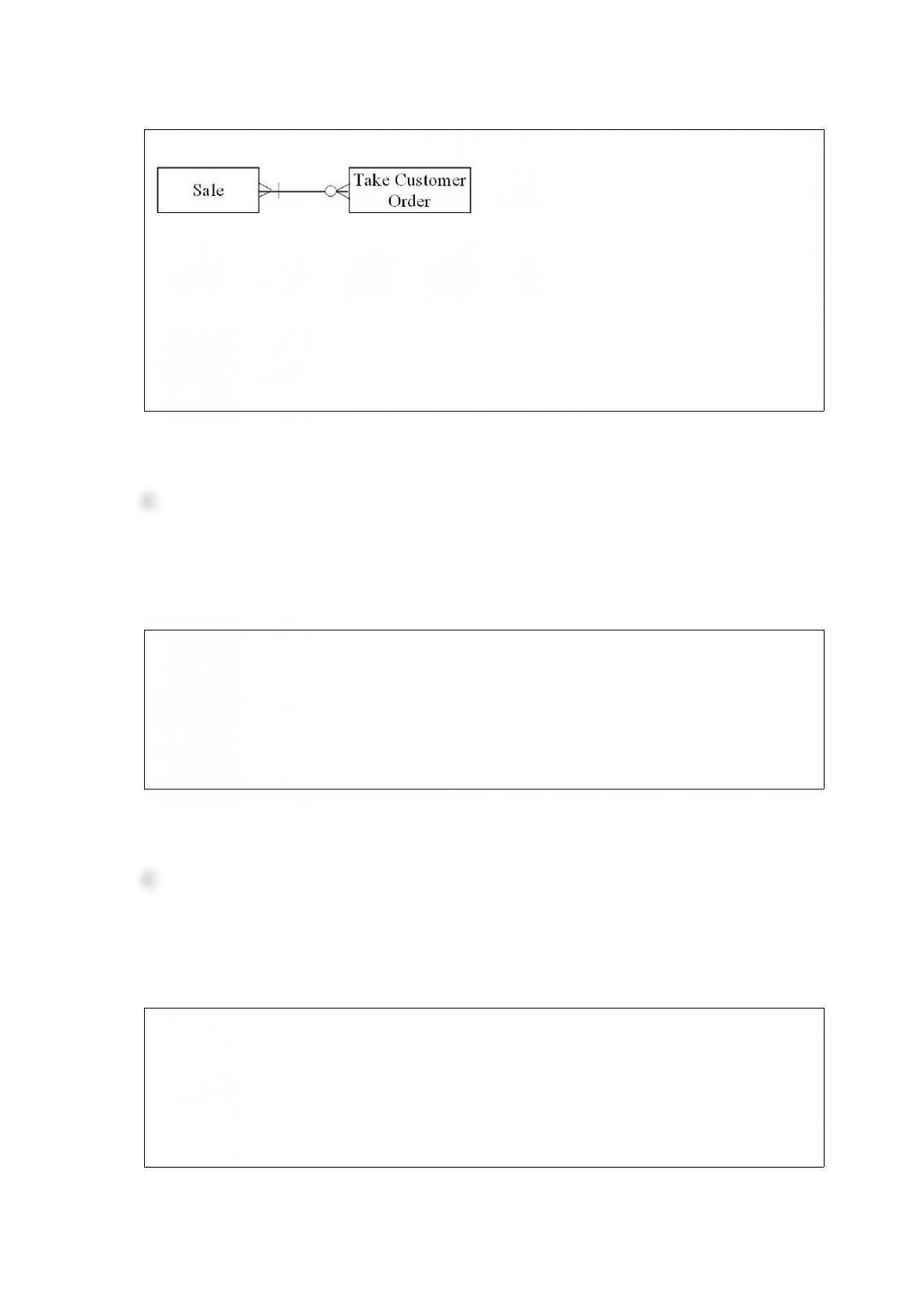
Which of the following transactions is represented by the diagram below?
A) Each sale is associated with a single order, and there is a time lag between the time
an order is taken and delivery of the product.
B) Each sale can be comprised of multiple orders, and each order can be associated
with multiple sales or no sales.
C) Each sale can be comprised of multiple orders, and each order can be associated
with one or more sales.
D) Each sale is associated with a single order, and there is no time lag between the time
an order is taken and delivery of the product.
Within the implementation planning and conversion phase of the systems development
life cycle, analysts must ________ before they can ________.
A) complete documentation; test software programs
B) install and test software; test software programs
C) test software programs; test the system
D) test the system; select and train personnel
Personnel policies such as background checks, mandatory vacations, and rotation of
duties tend to deter
A) unintentional errors.
B) employee fraud or embezzlement.
C) fraud by outsiders.
D) disgruntled employees.