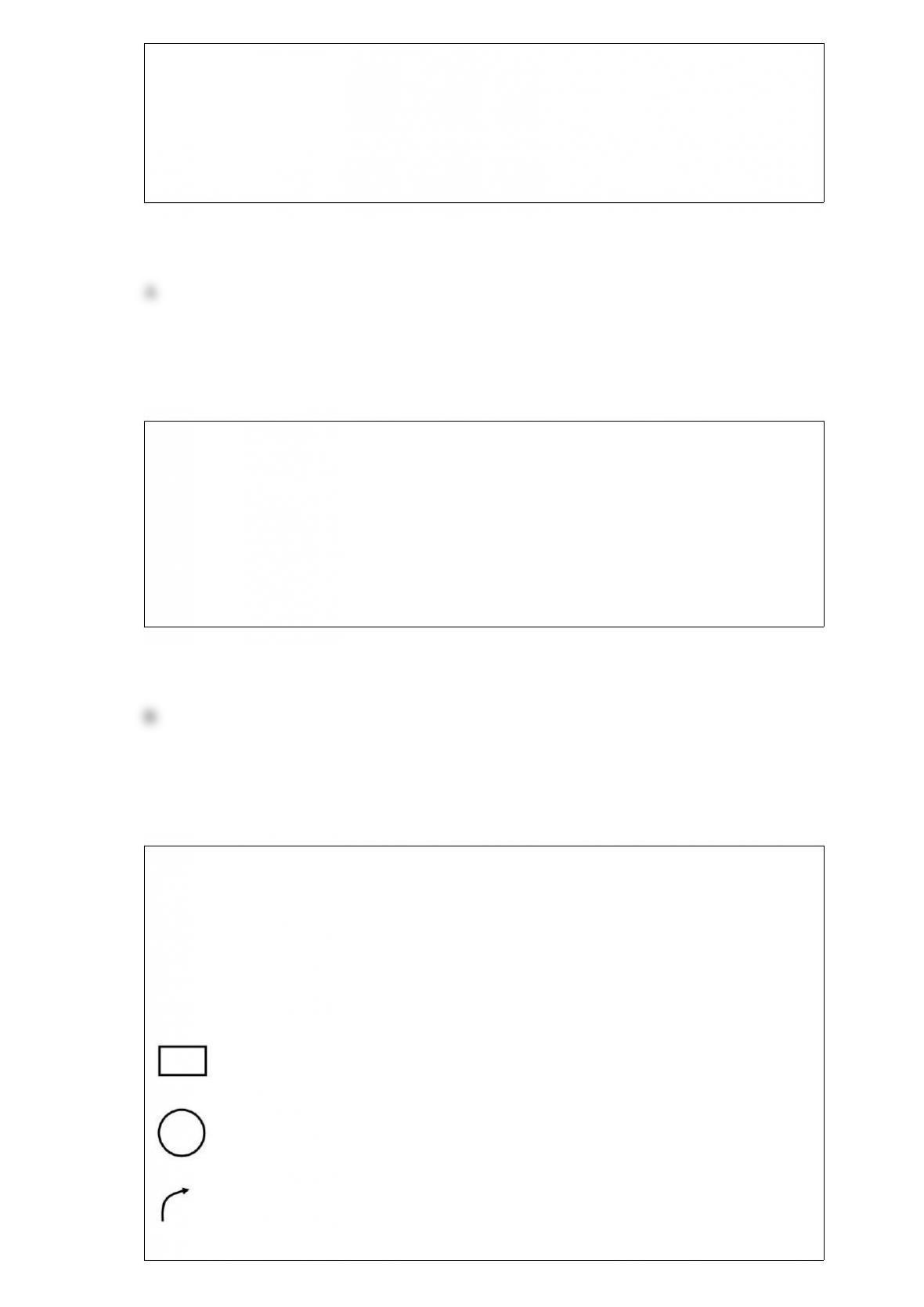
In a payroll processing DFD, the "prepare reports" activity will be represented by
________, the "employee payroll file" will be represented by ________, and the
"management" will be represented by ________.
A) a circle; two horizontal lines; a square.
B) a circle; two horizontal lines; two horizontal lines.
C) a rectangle; a square; a circle.
D) a square; two horizontal lines; a circle.
Identify the most correct statement with regard to how the various accounting
subsystems update the general ledger.
A) Individual journal entries for each accounting subsystem transaction update the
general ledger every 24 hours.
B) Summary journal entries that represent the results of all transactions for a certain
time period are used to update the general ledger.
C) The controller or treasurer must approve accounting subsystem journal entries before
any updating may occur.
D) Nonroutine transactions are entered into the system by the treasurer's office.
Fairfax Corporation uses two systems for revenue cycle transaction processing. One
system keeps track of customer sales. The other system keeps track of accounts
receivable. Last year, Fairfax Corporation decided to merge the two systems into one so
that both functions could be performed in the same system. This is an example of
A) competitive advantage.
B) technological innovation.
C) productivity gains.
D) systems integration.