Which of the following statements is true?
A) Batch processing ensures that stored information is always current.
B) Batch input is more accurate than on-line data entry.
C) On-line batch processing is a combination of real-time and batch processing.
D) Batch processing is not frequently used.
Which of the following is an example of an ERP system?
A) Sam uses a computerized information system to keep track of all the financial data
generated by her restaurant.
B) Jim has a system that keeps track of the cash receipts and cash disbursements of his
mowing business. At the end of each month, the system helps him to prepare a monthly
profit and loss statement.
C) Jane is a freelance photographer. She keeps records of all expenses and revenues on
her cell phone app and the files are uploaded to the cloud on a regular basis..
D) Claire keeps records of all her business records in an Excel file. Each week she
enters all of the data into a system that automatically generates purchase orders, based
on predetermined inventory reorder points. Production quotas for the coming week are
also automatically generated based on customer orders.
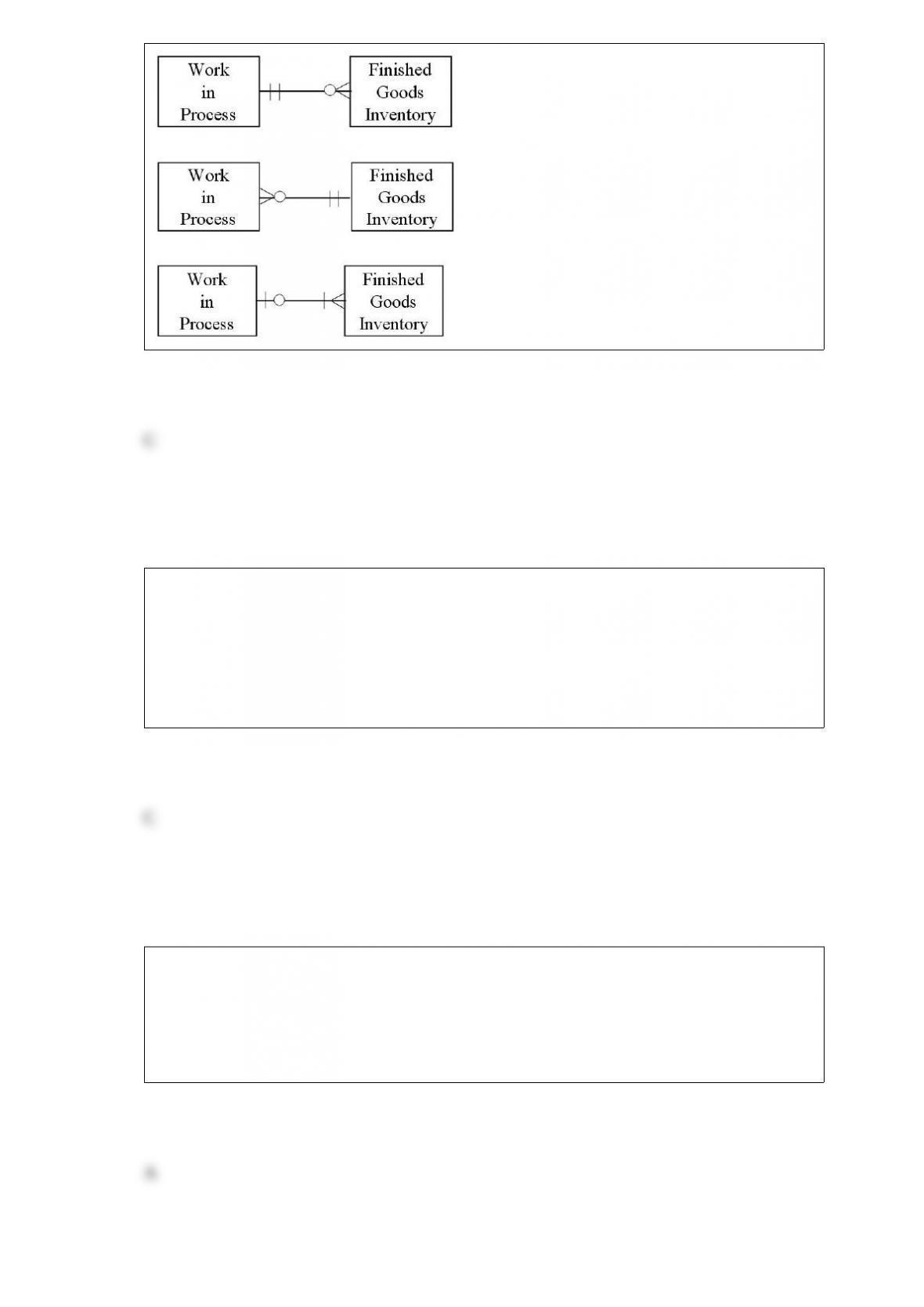
Which of the following diagrams represents the cardinality pairs in a situation where a
specific production run results in a specific finished good, and a specific finished good
is produced periodically?
A)
B)