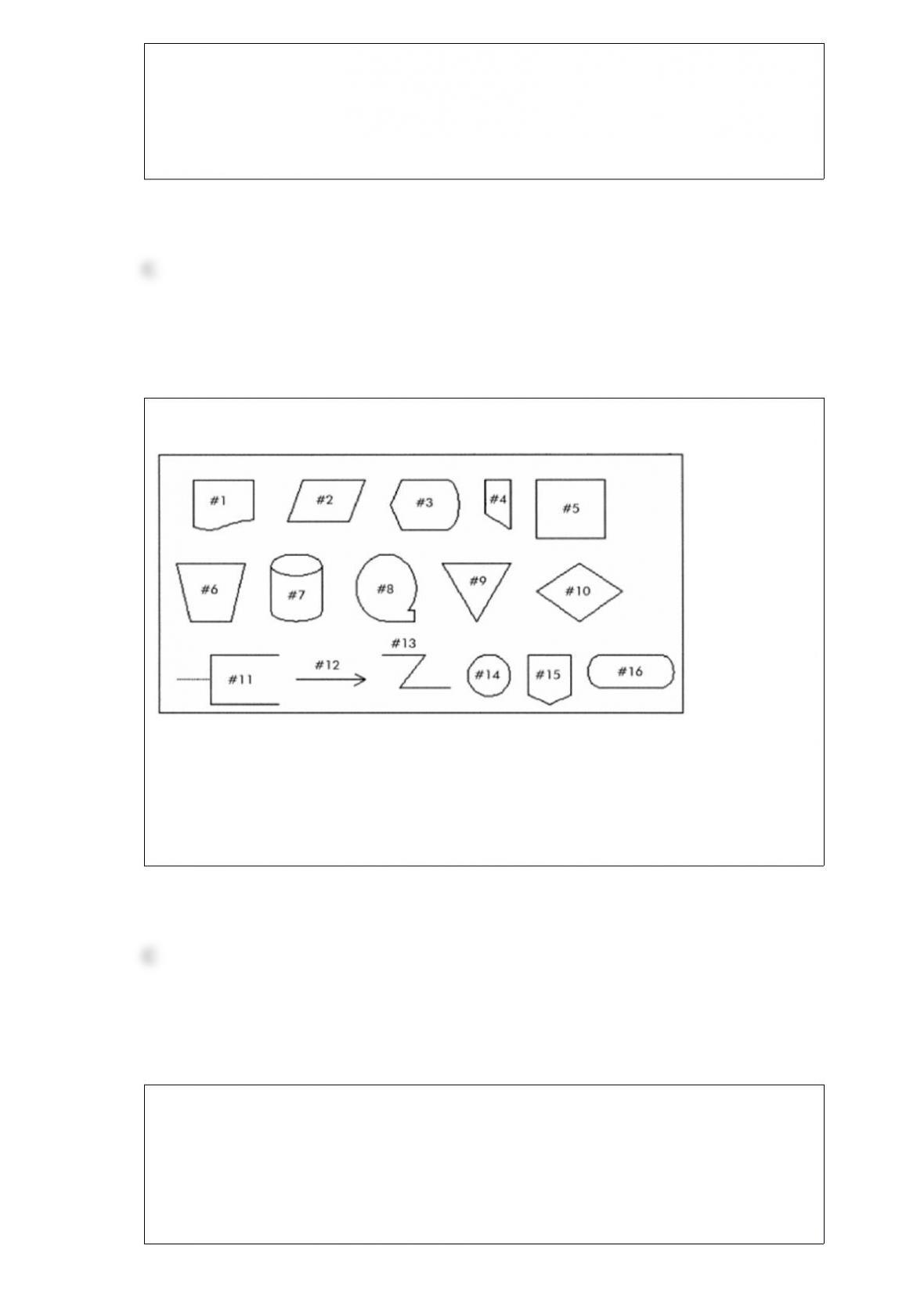
By using an ERP to merge the billing, sales, and marketing functions, the firm may be
able to
A) bill the customer right after the sale occurs.
B) market products and services on bills sent to customers.
C) use customer's past purchase history to send information about related products and
services the customer may be interested in.
D) eliminate the need for a firm to have a billing, sales, and marketing department.
The batch processing data entry control that sums the number of items in a batch is
called
A) financial total.
B) hash total.
C) record count.
D) sequence check.
There are frequently many canned software packages available. However, many
companies choose to develop their own software. Why?
A) An organization may have unique requirements that are not addressed by canned
software packages.
B) Canned software packages are often less expensive than software developed in
house.
C) The organization's size and complexity necessitates the in-house development of
software.
D) A and C above are correct.