What is a drawback to using the requirement costing method of software and hardware
evaluation?
A) Dollar estimates of costs and benefits are not included.
B) Intangible factors such as reliability and vendor support are overlooked.
C) The weights and points used are assigned subjectively.
D) There is no drawback to using the requirements costing method.
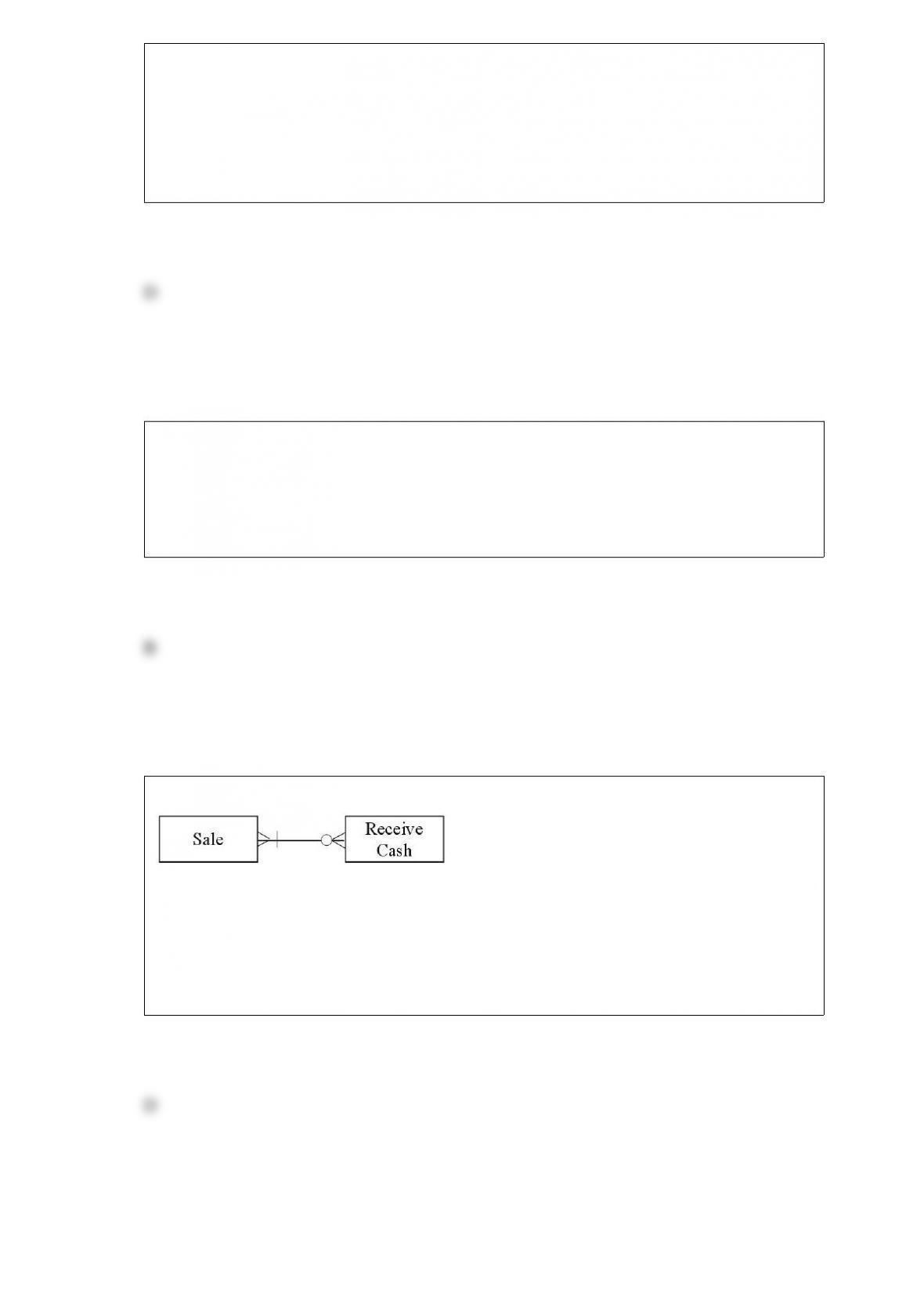
At a movie theater box office, all tickets are sequentially prenumbered. At the end of
each day, the beginning ticket number is subtracted from the ending number to calculate
the number of tickets sold. Cash is counted and compared with the number of tickets
sold. Which of the following situations does this control detect?
A) Some customers presented tickets purchased on a previous day when there wasn't a
ticket taker at the theater entrance (so the tickets didn't get torn.)
B) A group of kids snuck into the theater through a back door when customers left after
a show.
C) The box office cashier accidentally gives too much change to a customer.
D) The ticket taker admits his friends without tickets.
A(n) ________ measures company progress by comparing actual performance to
planned performance.
A) boundary system
B) diagnostic control system
C) interactive control system
D) belief system