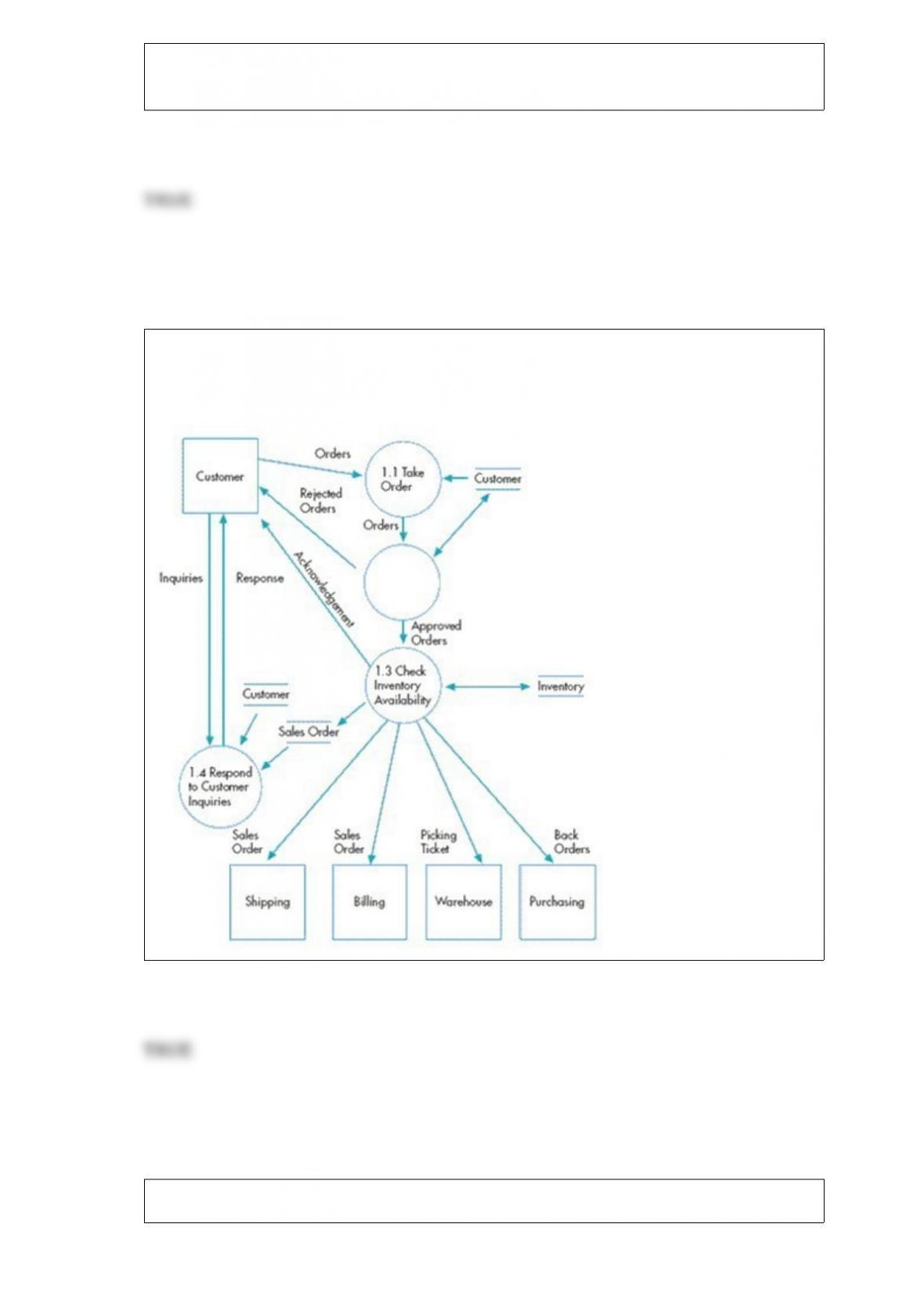
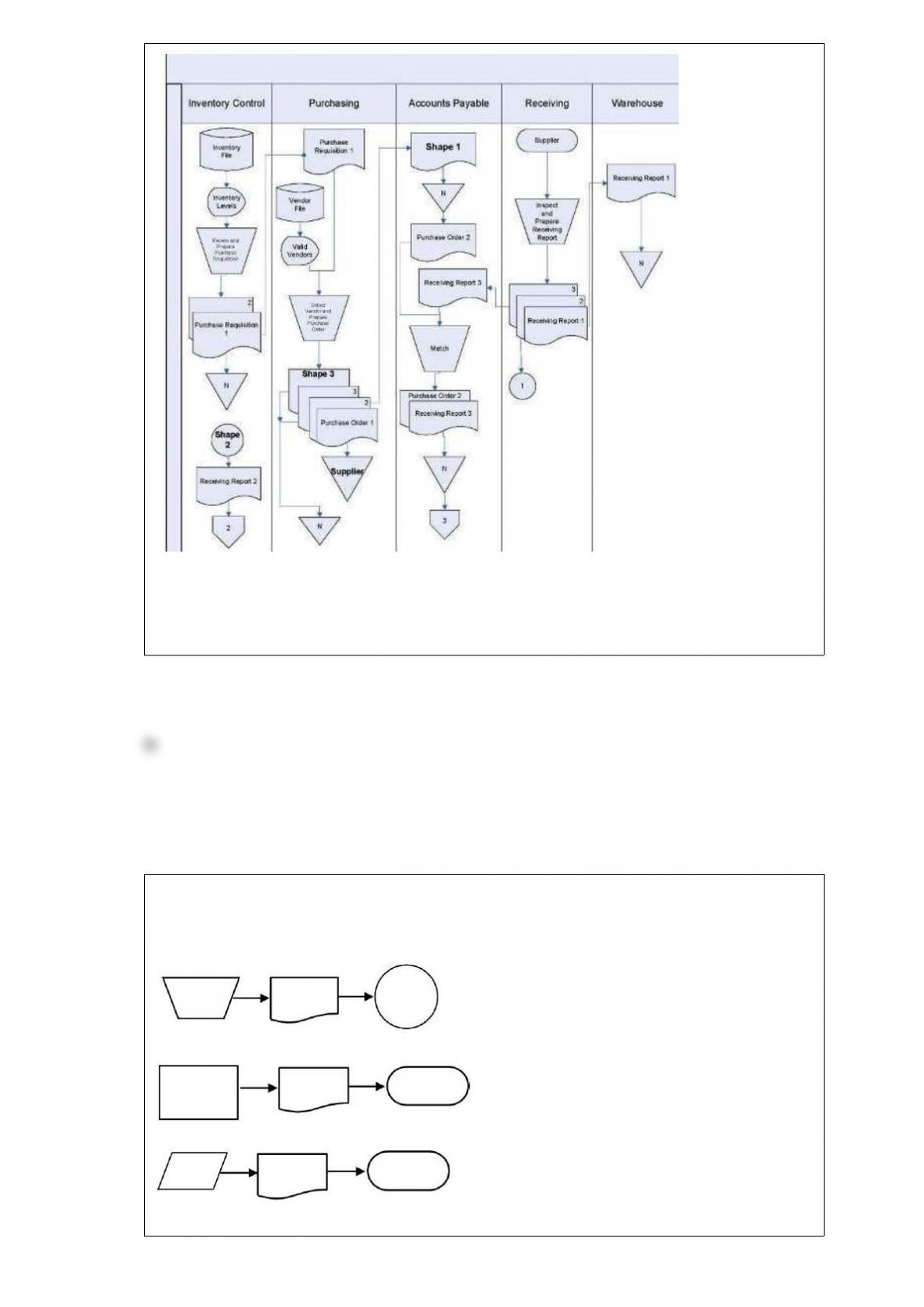
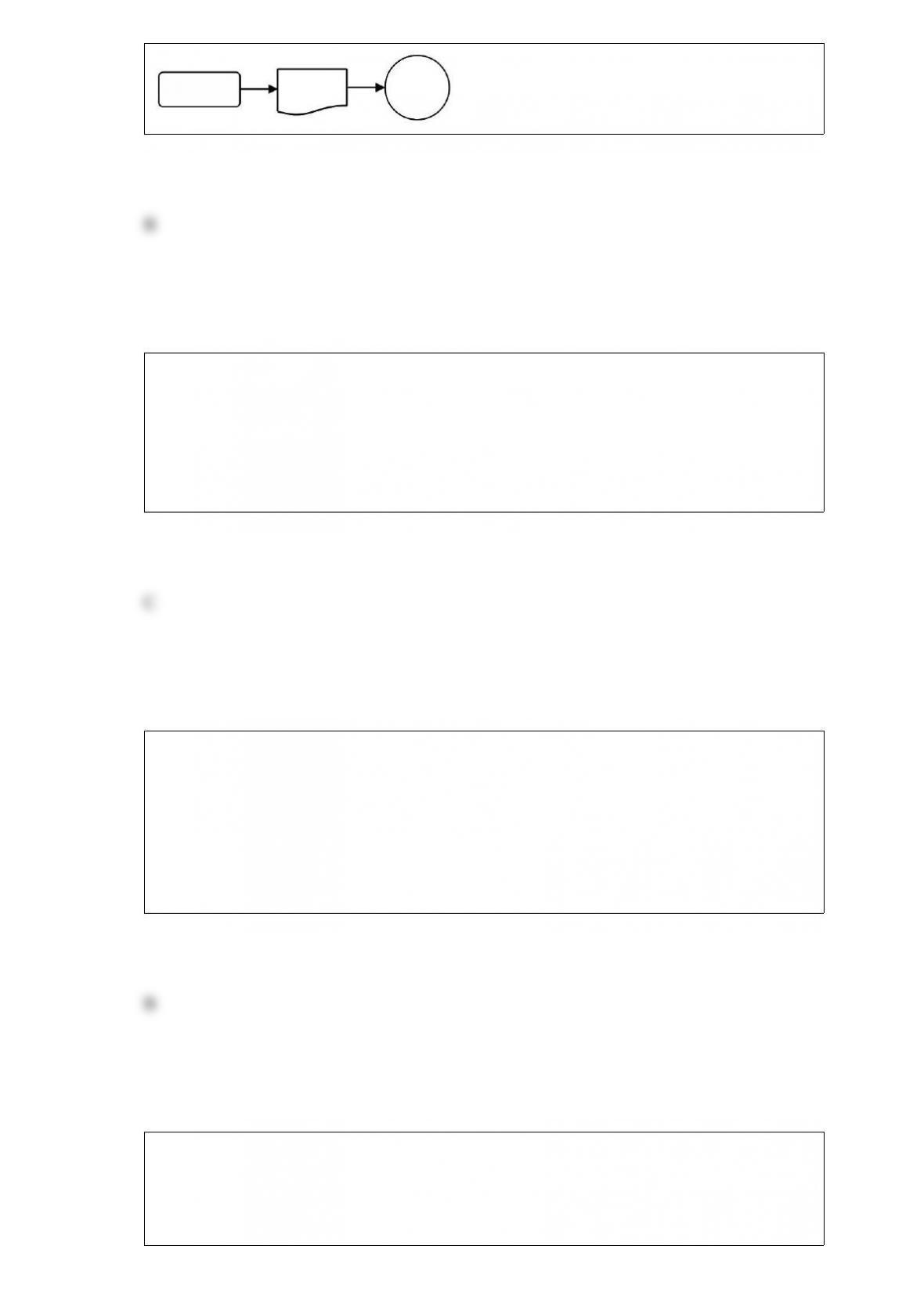
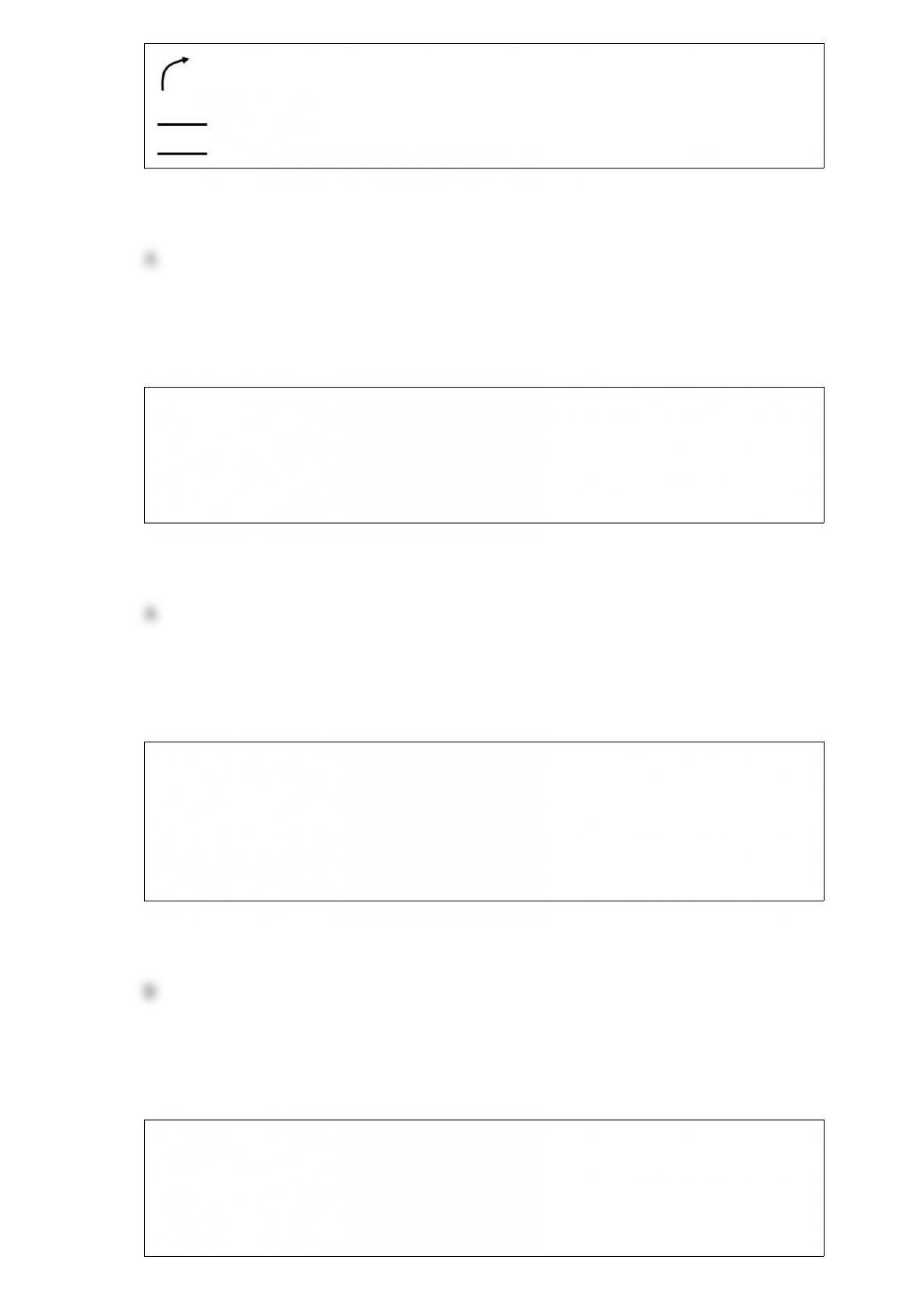
Which of the following controls can minimize the threat of poorly designed reports and
graphs?
A) Training and experience in applying IFRS and XBRL.
B) Responsibility accounting.
C) Backup and disaster recovery procedures.
D) Restriction of access to general ledger.
The best control procedure for accurate data entry is
A) the use of on-line terminals.
B) an access control matrix.
C) passwords and user IDs.
D) automation of data collection.
Terrell and Monique Anderson run an antique store in their hometown of Dayton, Ohio.
To find items to sell in their shop, they travel around the United States and Europe
buying unique artifacts. Within an hour of making a purchase, they use their
smartphone to take a picture of the item and post a short tweet about the item on
Twitter. Then, they ship the item back to Dayton for sale in their shop. Which symbol
should be used to represent Twitter in a context diagram of this process?
A)
B)
C)