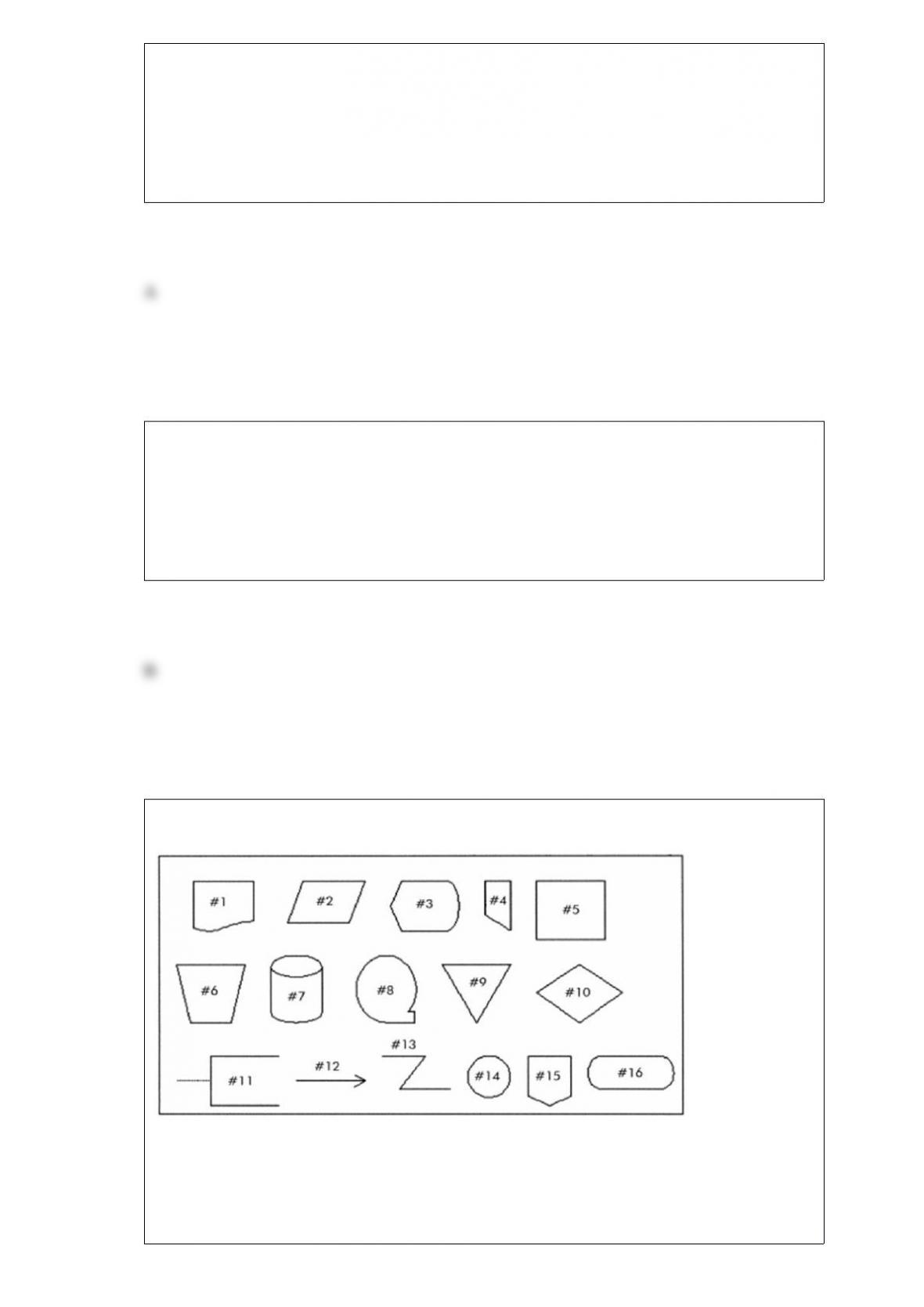
B) Persistent.
C) Protest.
D) Projection.
A delivery of inventory from a vendor, with whom a credit line is already established,
would be initially recorded in which type of accounting record and as part of what
transaction cycle?
A) purchases journal; expenditure cycle
B) general journal; expenditure cycle
C) general ledger; expenditure cycle
D) cash disbursements journal; production cycle
Which type of software provides an additional layer of protection to sensitive
information that is stored in digital format, offering the capability not only to limit
access to specific files or documents but also to specify the actions that individuals who
are granted access to that resource can perform?
A) Anti-virus software.
B) Data loss prevention software.
C) A digital watermark.
D) Information rights software.
Which of the following is false with regards to REA models?
A) Many financial statement accounts are represented as resources in the REA model.