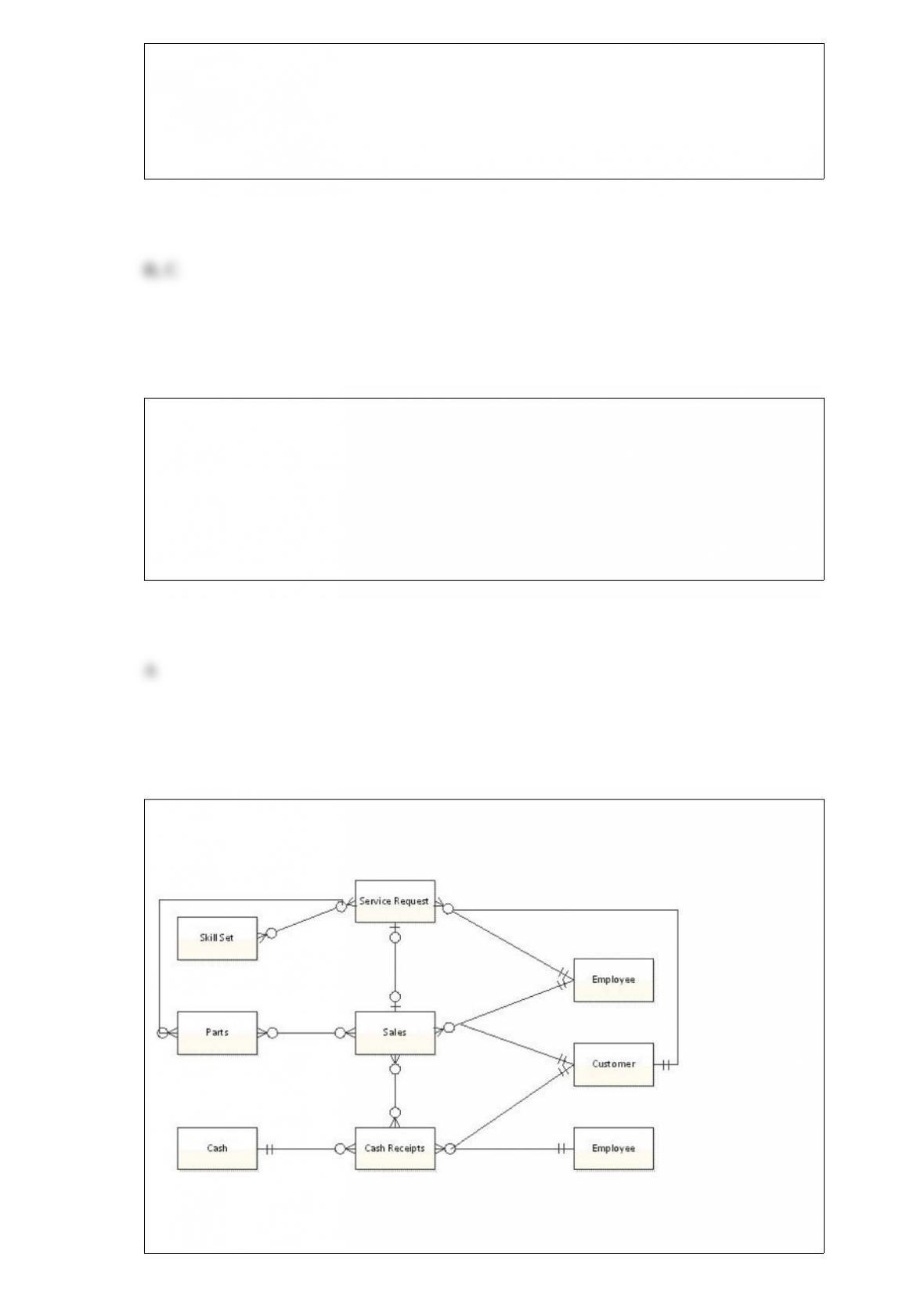
D) The primary key for Sales would be a foreign key for Service Request.
Identify the statement below that is false with regards to basic requirements of a
relational database model.
A) Primary keys can be null.
B) Foreign keys, if not null, must have values that correspond to the value of a primary
key in another table.
C) All non-key attributes in a table should describe a characteristic about the object
identified by the primary key.
D) Every column in a row must be single-valued.
In an REA diagram for the HR/Payroll cycle, the relationship between Employees and
Training is typically M:N for all except which of the following reasons?
A) One employee may attend the same training event more than once.
B) Each employee may attend more than one training event.
C) Each training event may have more than one employee attend.
D) One training event may be offered more than once.
An accounting information system (AIS) processes ________ to provide users with
________.
A) data; information
B) data; transactions
C) information; data