B) use an ERP.
C) proper segregation of duties.
D) use multiple master data files.
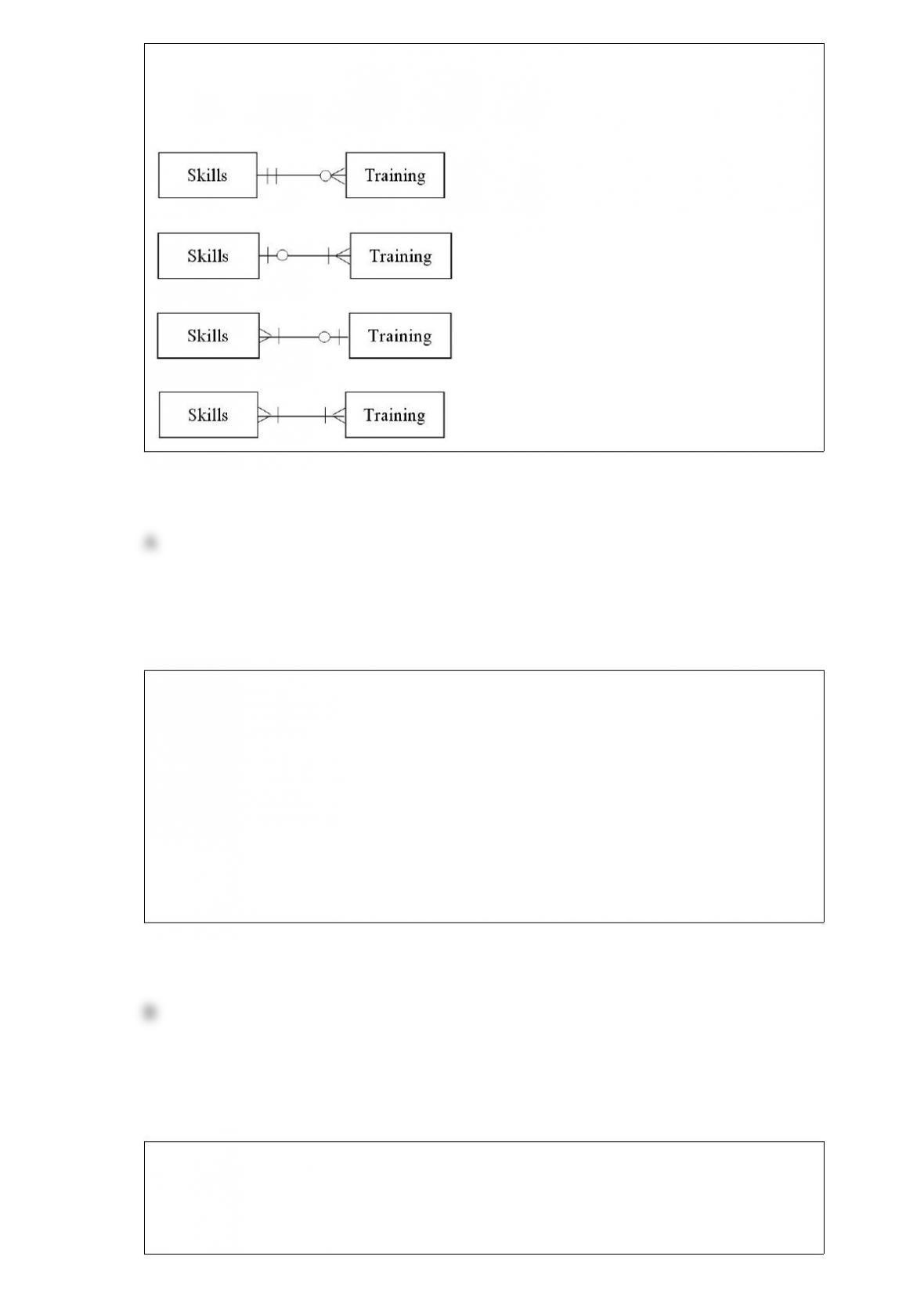
Which of the following lists represent the sequence of elements in developing the
conceptual design specifications?
A) Input, data storage, processing procedures and operations, and output.
B) Input, output, data storage, and processing procedures and operations.
C) Output, data storage, input, and processing procedures and operations.
D) Processing procedures and operations, input, data storage, and output.
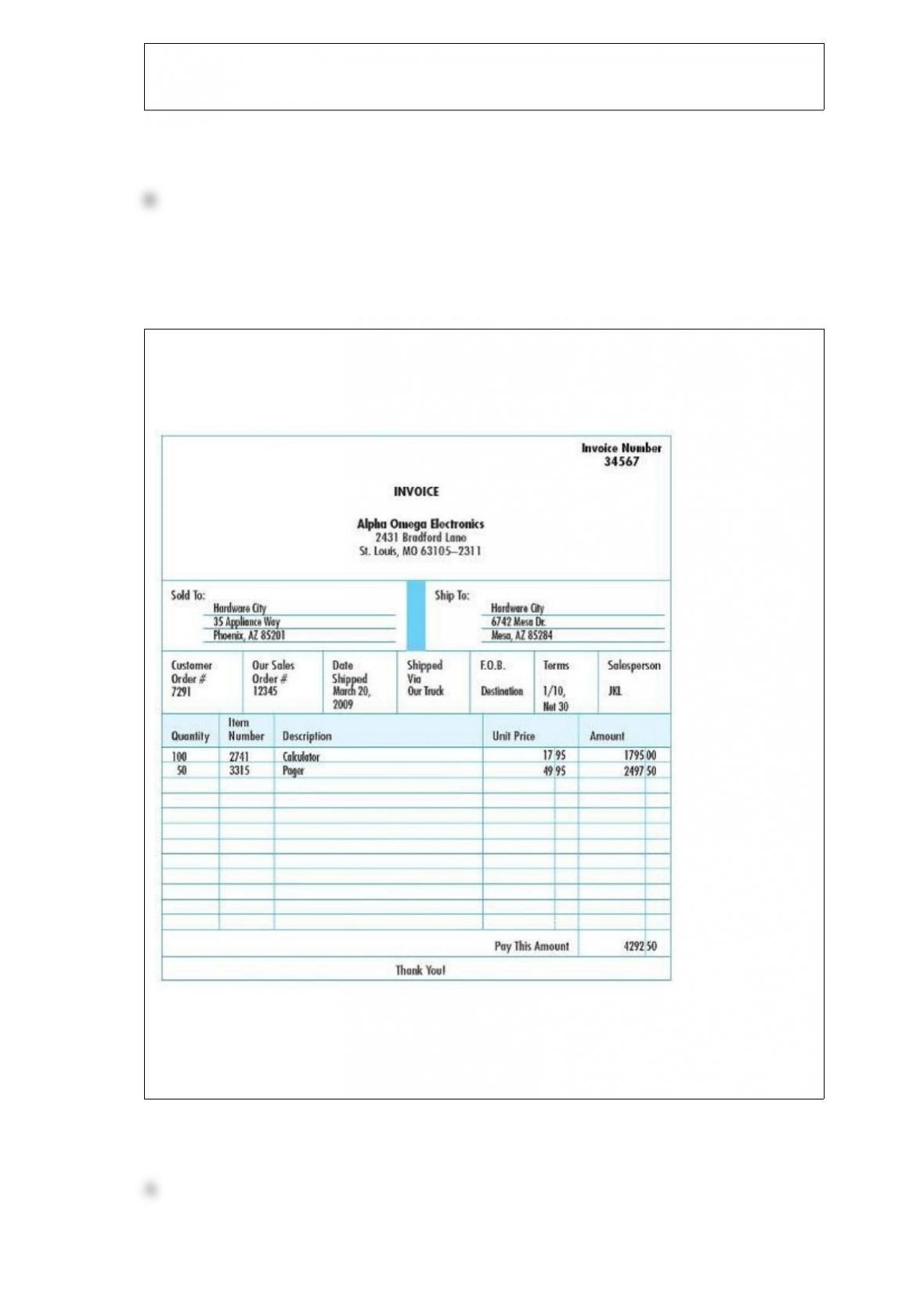
Which of the following is generally not shown on a receiving report?
A) price of the items
B) quantity of the items
C) purchase order number
D) counted and inspected by
Abby Burke has created custom statues made out of scrap metal for over ten years.
Abby has kept detailed records of every statue she has ever created. For every sale, she
obtains the customer's name and address, a description of the statue, and a picture of the
statue sold to the customer. Her unique style has recently attracted the attention of
several celebrities. Ready to take her business to the next level, Abby has hired you to
construct an accounting information system, which she wants modeled after her paper