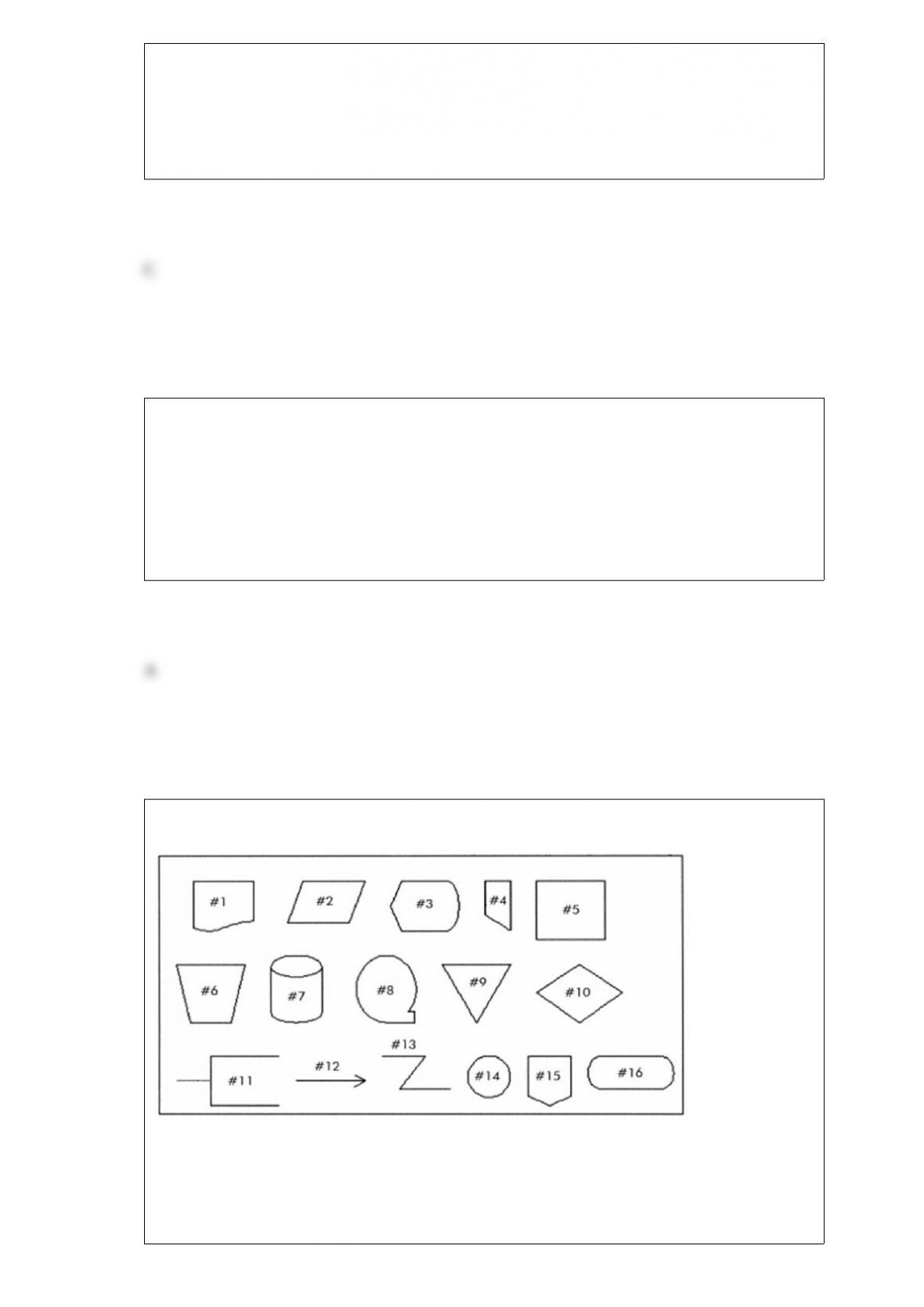
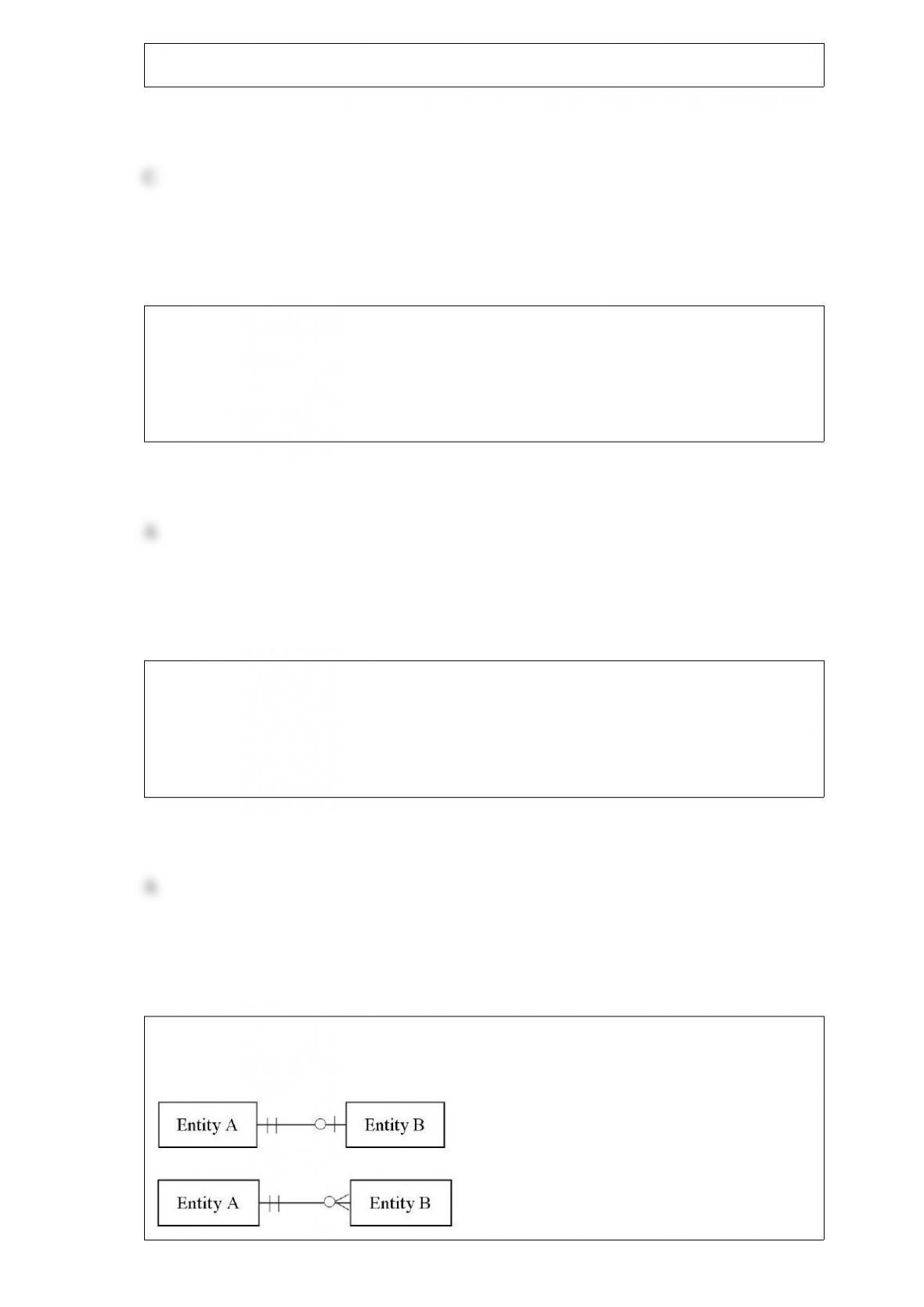
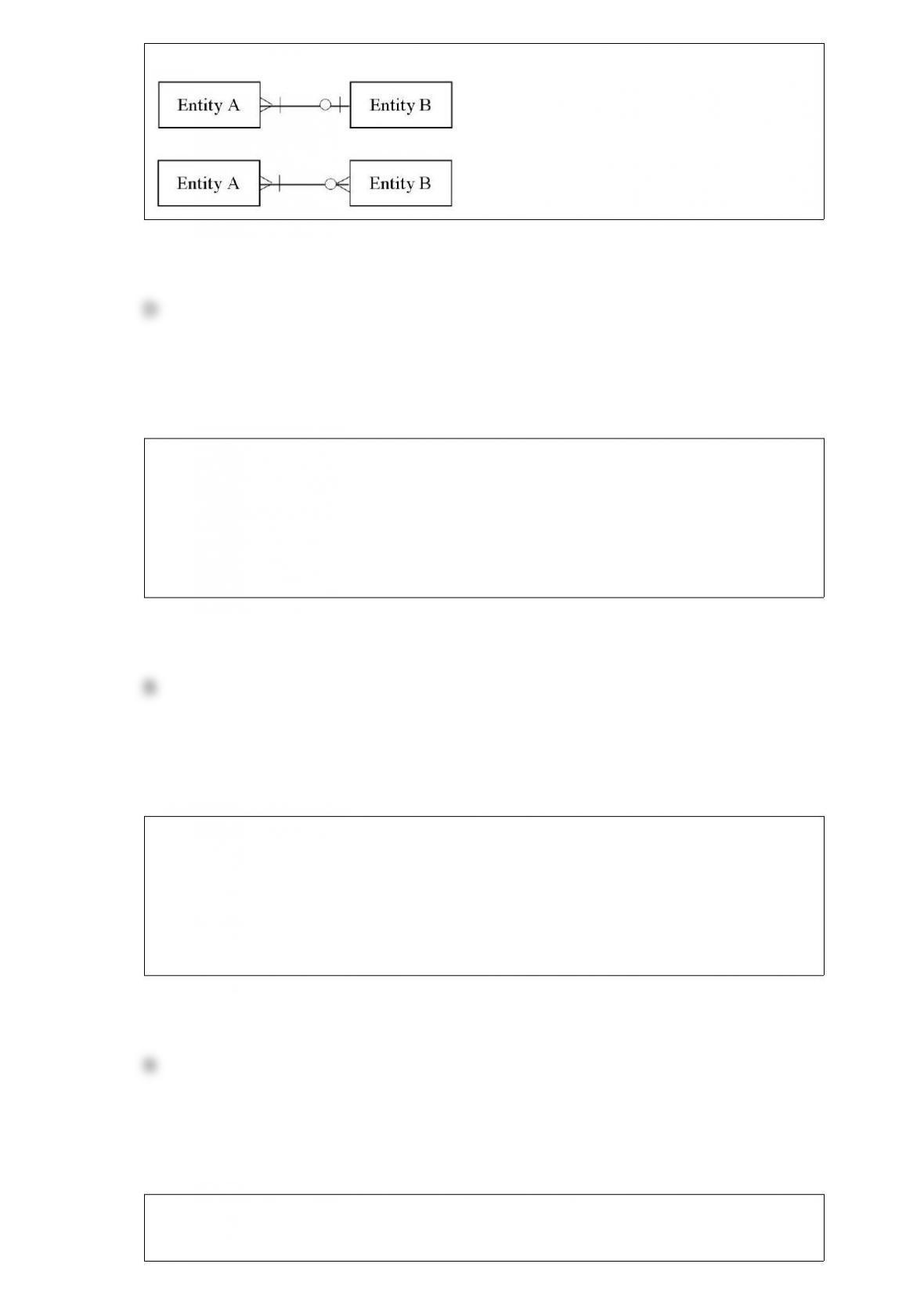
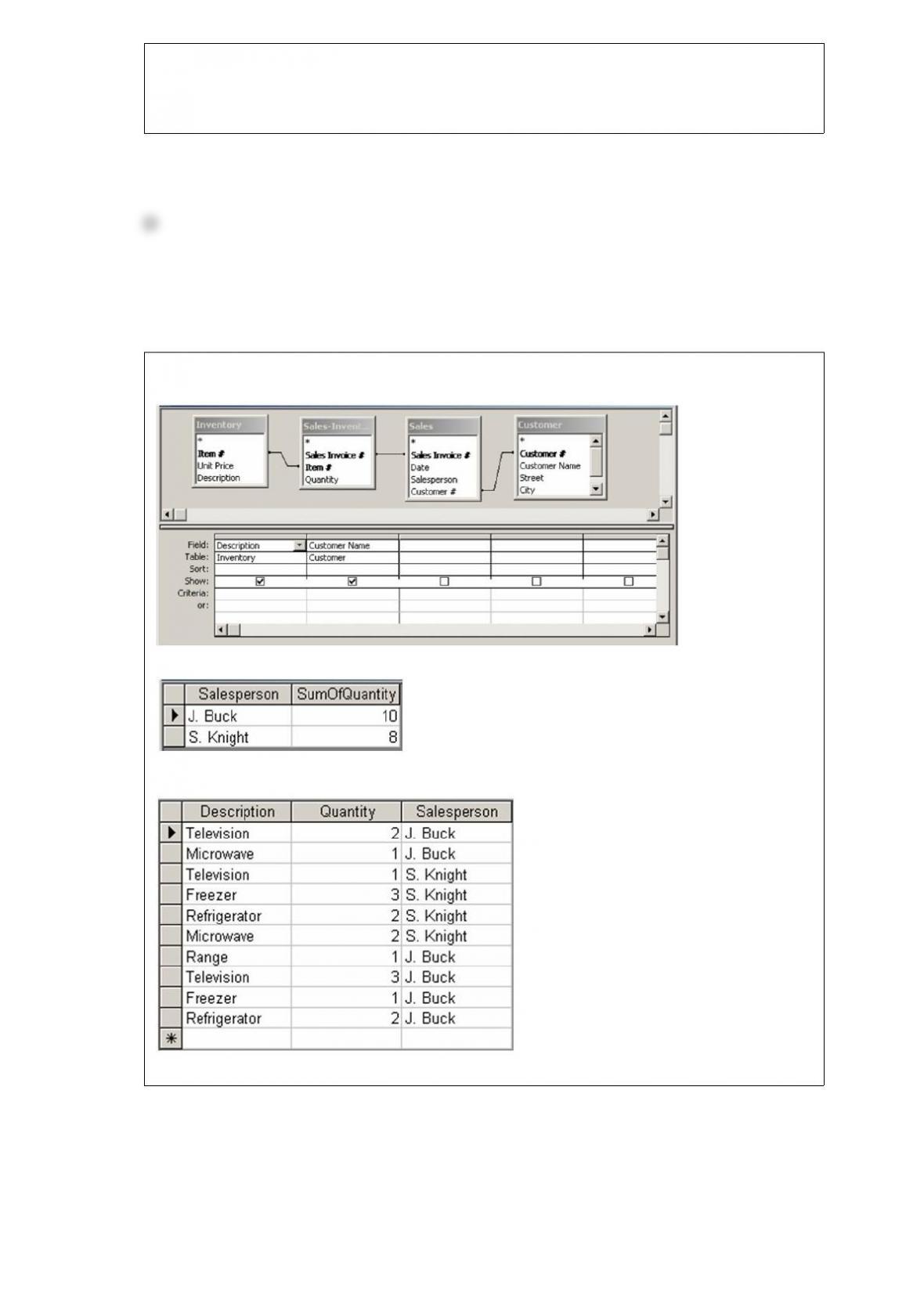
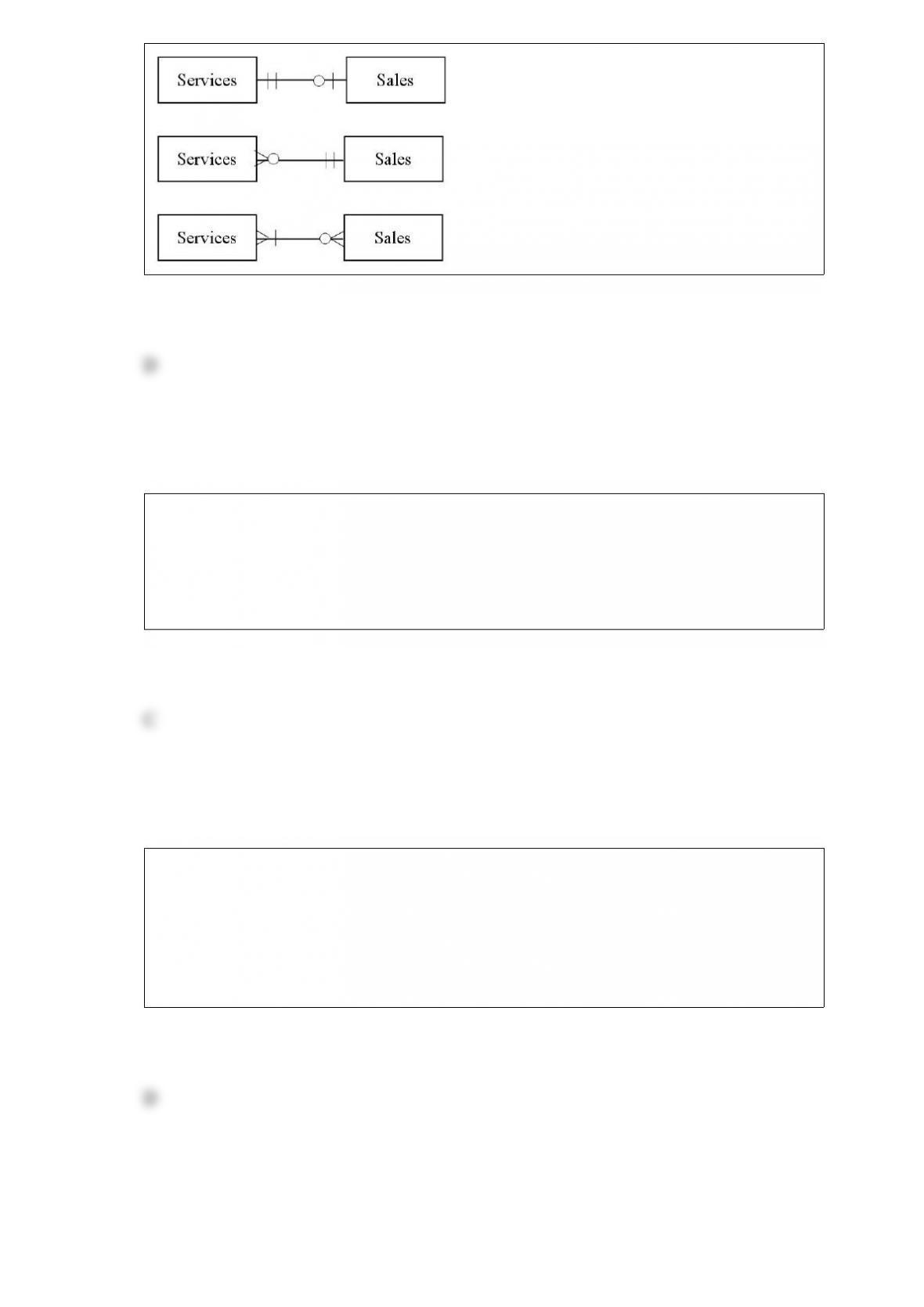
C) creating new products.
D) both A and B
In recent years, many of the attacks carried out by hackers have relied on this type of
vulnerability in computer software.
A) Code mastication.
B) Boot sector corruption.
C) URL injection.
D) Buffer overflow.
What is a SQL injection attack?
A) It is an attack when the perpetrator is inserting malicious query in input such that it
is passed to and executed by an application program.
B) It is an attack when the perpetrator is inputting so much data that the input buffer
overflows. The overflow contains code that takes control of the company's computer.
C) It is an attack when the perpetrator uses software to guess company's addresses, send
employees blank e-mails, and add unreturned messages to spammer e-mail list.
D) It is an attacked when the perpetrator sends hundreds of messages from randomly
generated false addresses, overloading an Internet service provider's e-mail server.
Identify one potential drawback in the design and implementation of database systems
for accounting.
A) Double-entry accounting relies on redundancy as part of the accounting process, but