for reviewing and authorizing purchase orders. She also reviews receiving reports,
approves or corrects them, and authorizes the cashier to pay vendor invoices. Which of
the following would correct control weaknesses related to these activities?
A) Controls are adequate under the current system.
B) Vendor invoices should be reviewed by accounts receivable and then cancelled when
paid.
C) Vendor invoices should be reviewed by the purchasing manager to ensure that they
are correct.
D) Accounts payable should reconcile purchase orders, receiving reports, and invoices.
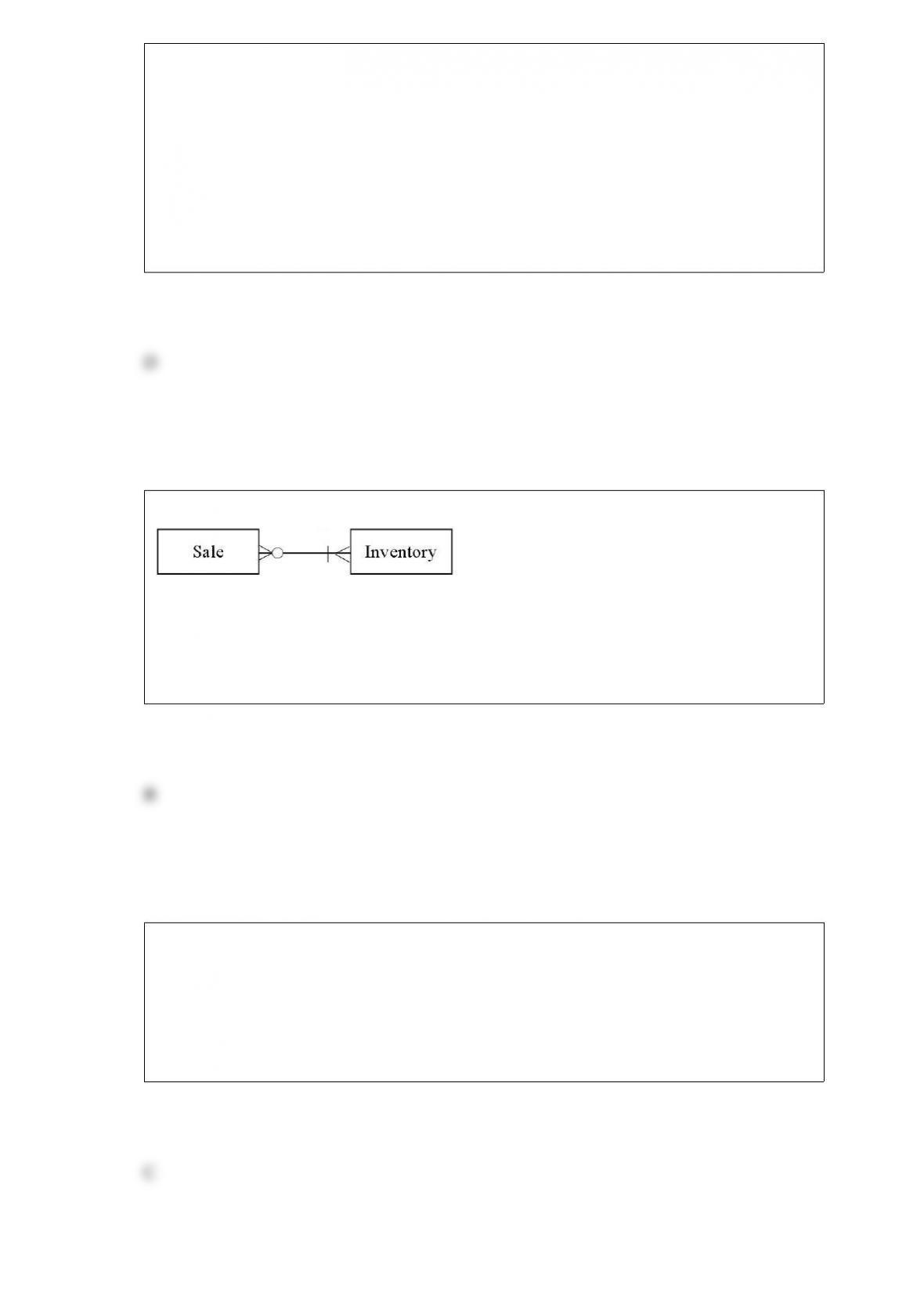
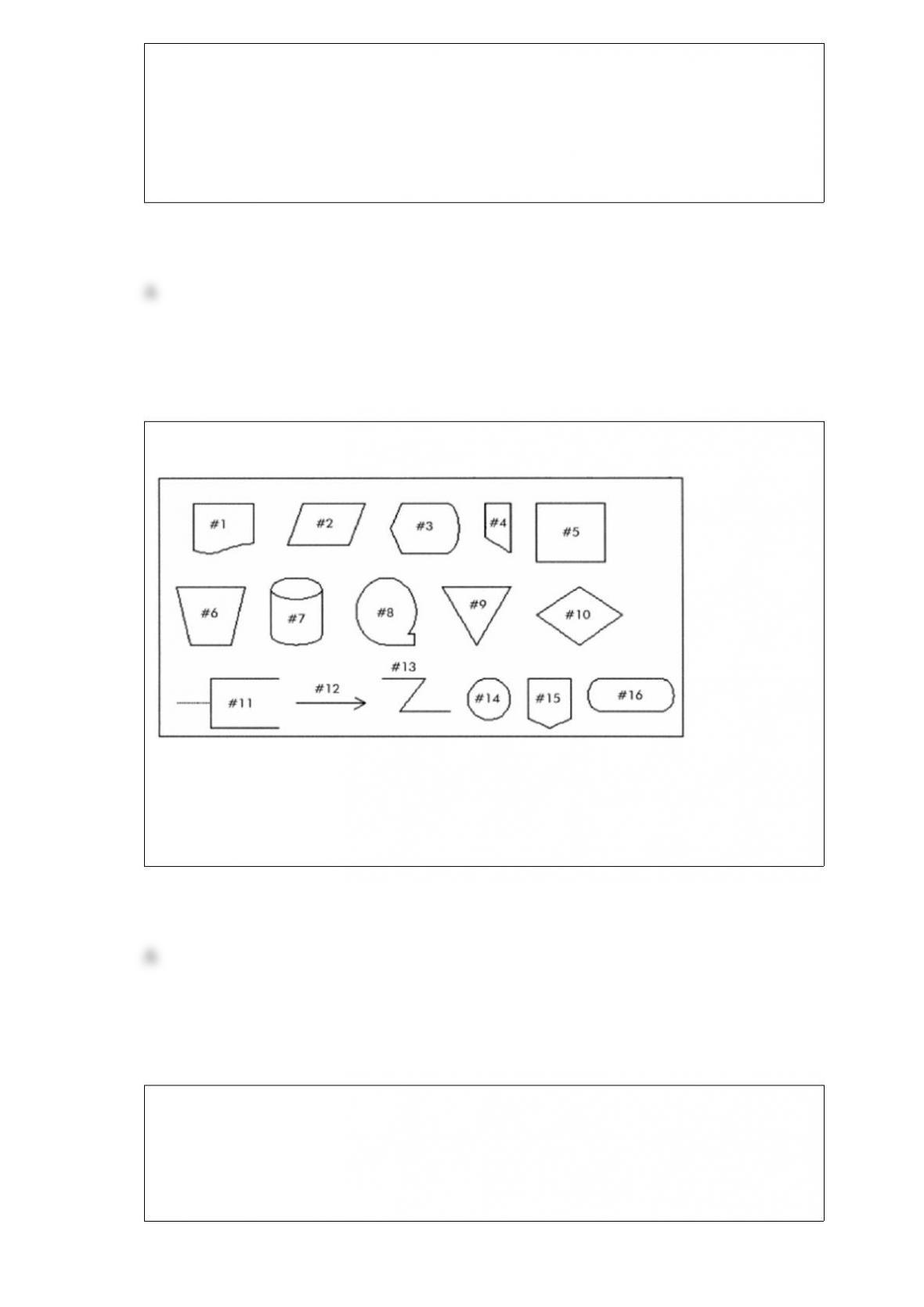
Which of the following transactions is represented by the diagram below?
A) A junkyard holds weekly sales where it sells its entire inventory.
B) A shoe store sells products to consumers.
C) A stay-at-home mom creates furniture for doll houses. When one piece is finished,
she sells it on Amazon.com.
D) Netflix sells movies to consumers through its online downloading service.
The Trust Services Framework reliability principle that states sensitive information be
protected from unauthorized disclosure is known as
A) availability.
B) security.
C) confidentiality.
D) integrity.