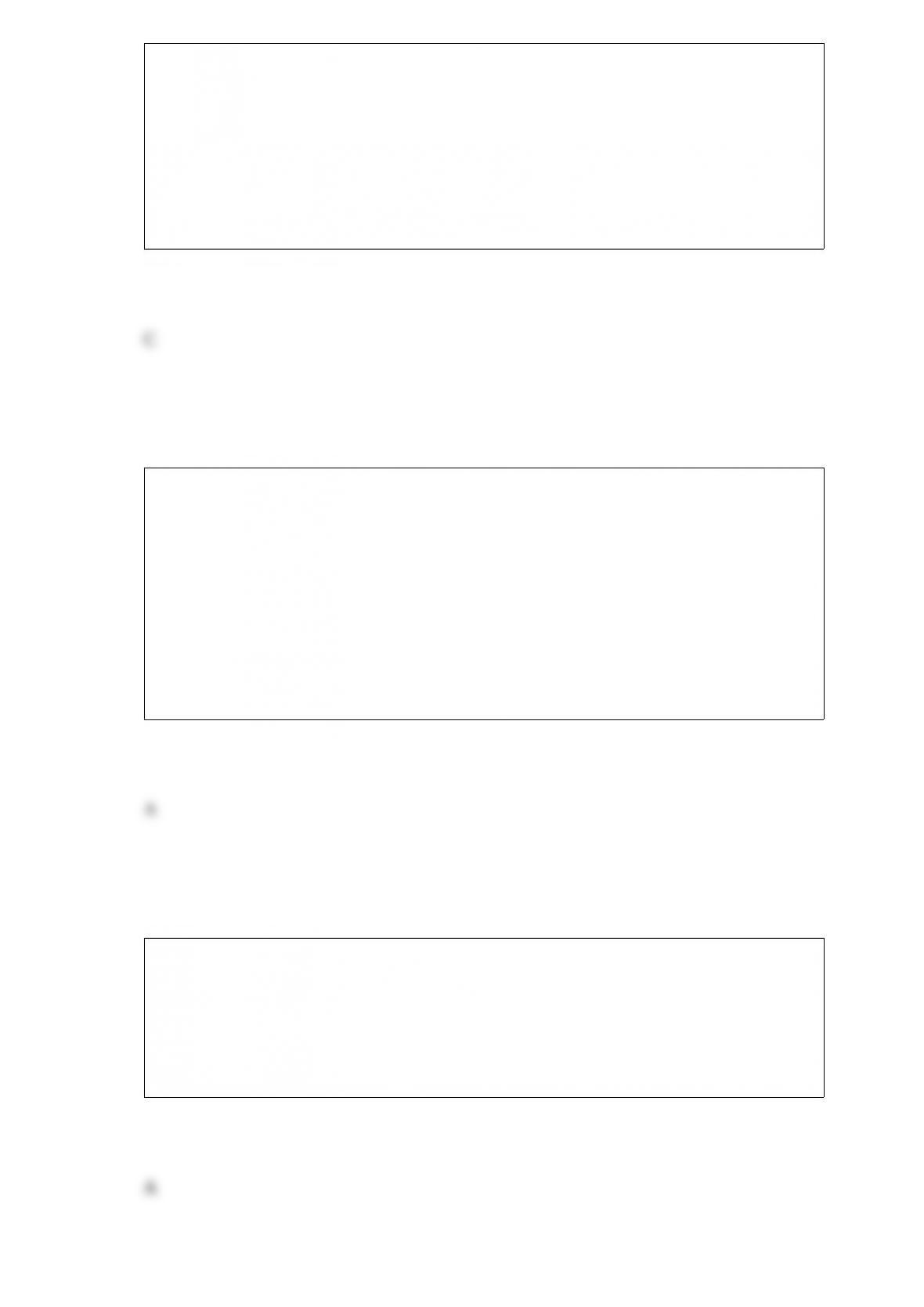
A) It is an attack when the perpetrator is inserting malicious query in input such that it
is passed to and executed by an application program.
B) It is an attack when the perpetrator is inputting so much data that the input buffer
overflows. The overflow contains code that takes control of the company's computer.
C) It is an attack when the perpetrator uses software to guess company's addresses, send
employees blank e-mails, and add unreturned messages to spammer e-mail list.
D) It is an attacked when the perpetrator sends hundreds of messages from randomly
generated false addresses, overloading an Internet service provider's e-mail server.
A relationship between Skills and Employees is typically modeled as M:N in an REA
database model since
A) one employee may possess many skills, and one skill may be possessed by more
than one employee.
B) many employees possess skills, and many skills are possessed by employees.
C) employees can be trained to learn all skills, and all skills are possessed by at least
one employee.
D) The relationship would be 1:N not M:N, because most employees are hired for a
specific job that requires a specific skill, even though a specific job could be done by
many employees.
When an organization seeks to modify canned software, it is best when ________
because unauthorized modifications may make the program unreliable.
A) the vendor modifies the software
B) the intended end-user modifies the software
C) programmers with software experience modify the software
D) the organization's IT modifies the software