A) centralization and defined procedures.
B) centralization and autonomy.
C) decentralization and defined procedures.
D) decentralization and autonomy.
According to The Sarbanes-Oxley Act of 2002, the audit committee of the board of
directors is directly responsible for
A) hiring and firing the external auditors.
B) performing tests of the company's internal control structure.
C) certifying the accuracy of the company's financial reporting process.
D) overseeing day-to-day operations of the internal audit department.
Data diddling is
A) verifying credit card validity; buying and selling stolen credit cards.
B) inserting a sleeve into an ATM so that it will not eject the victim's card, pretending to
help the
victim as a means of obtaining his PIN, and using the card and PIN to drain the account.
C) a technique that tricks a person into disclosing confidential information.
D) changing data before, during, or after it is entered into the system in order to delete,
alter, or add key system data.
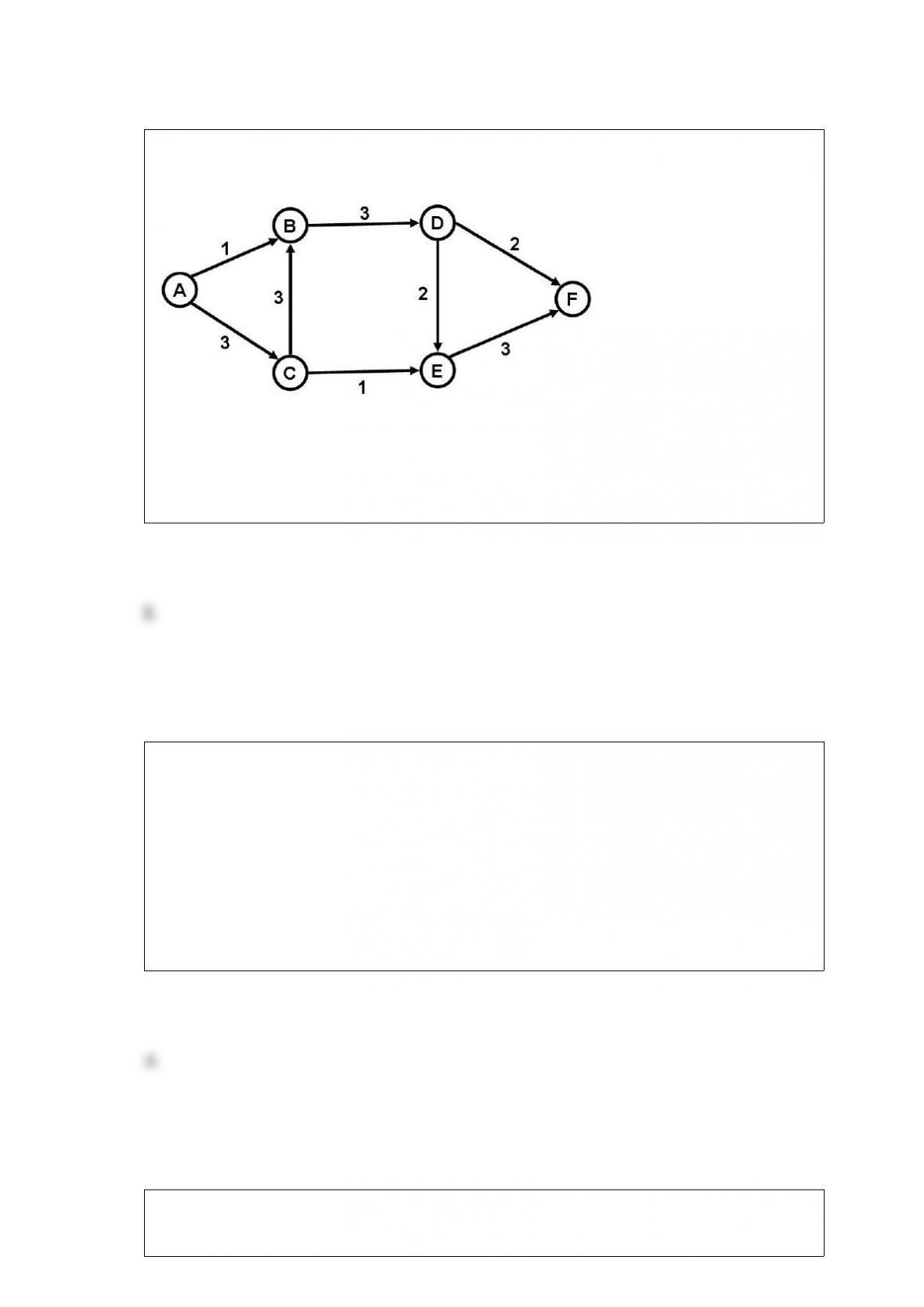
The general ledger and reporting system consists of the ________ involved in
________ the general ledger and ________ reports.