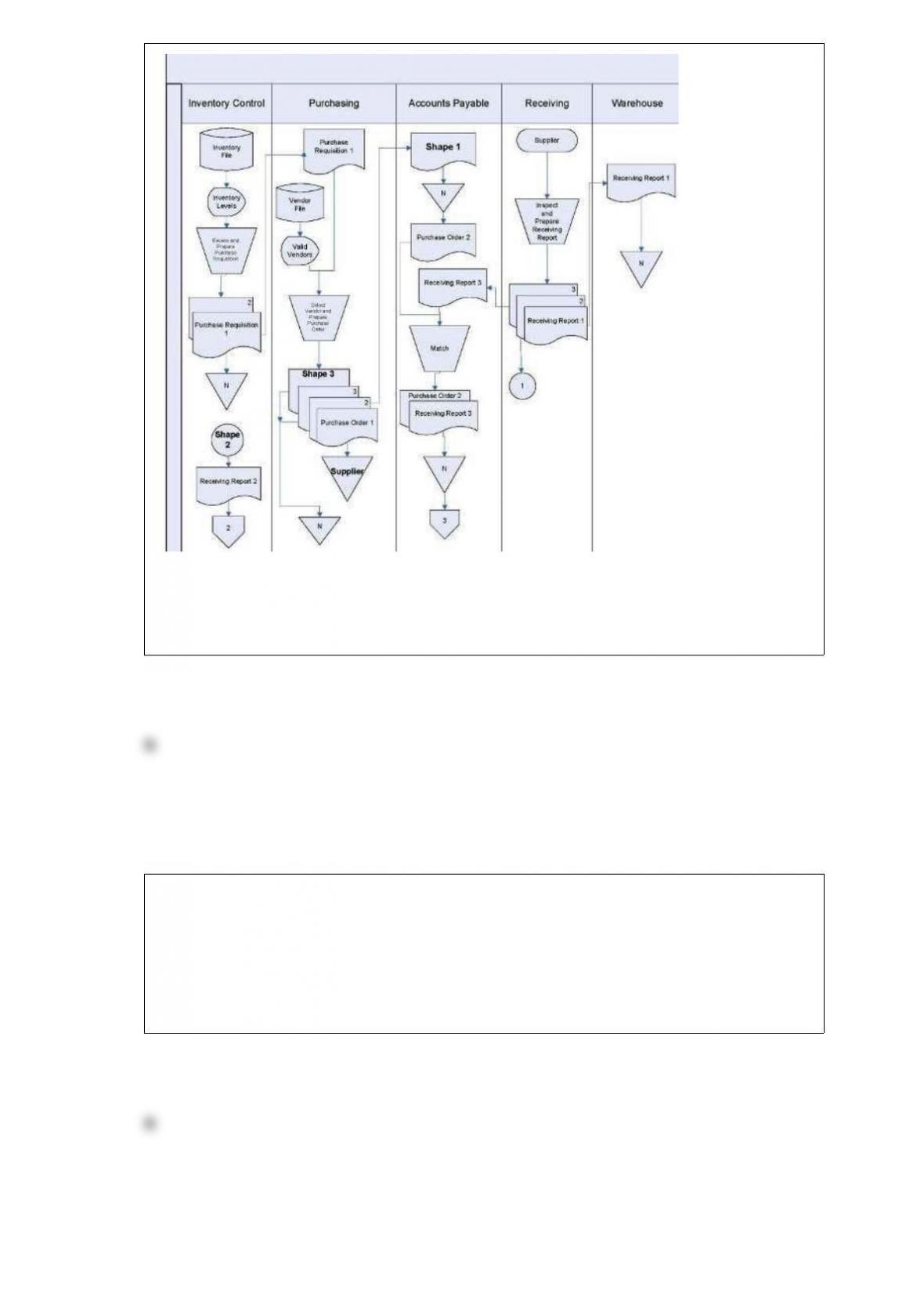
Melissa is a staff accountant for Quality Paper Company, which has strict corporate
policies on appropriate use of corporate resources. The first week of March, Melissa
saw Kent, the branch manager putting printer paper and toner into his briefcase on his
way out the door. This situation best reflects a weakness in which aspect of internal
environment, as discussed in the COSO Enterprise Risk Management Framework?
A) Integrity and ethical values.
B) Risk management philosophy.
C) Restrict access to assets.
D) Methods of assigning authority and responsibility.
Because many HRM / payroll master databases typically contain only descriptive
information (such as which employees possess which skills), many firms have deployed
________ to more effectively leverage employees knowledge and skills.
A) relational databases
B) knowledge management systems
C) talent management systems
D) cardinality systems
Which of the following is not usually a consideration when designing a coding system?
A) government coding regulations
B) standardization
C) future expansion needs
D) ease of reporting