correctly and then subsequently changed, with the difference diverted to a fictitious
customer account. This is an example of
A) kiting.
B) data diddling.
C) data leakage.
D) phreaking.
At the beginning of this chapter, you were presented with a situation regarding Jason
Scott. Jason is an internal auditor for Northwest Industries, a forest products company.
On March 31, he reviewed his completed tax return and noticed that the federal income
tax withholding on his final paycheck was $5 more than the amount indicated on his
W-2 form.He used the W-2 amount to complete his tax return and made a note to ask
the payroll department what happened to the other $5. The next day, Jason was
swamped, and he dismissed the $5 difference as immaterial. On April 16, a coworker
grumbled that the company had taken $5 more from his check than he was given credit
for on his W-2. When Jason realized he was not the only one with the $5 discrepancy,
he investigated and found that all 1,500 employees had the same $5 discrepancy. He
also discovered that the W-2 of Don Hawkins, the payroll programmer, had
thousands of dollars more in withholdings reported to the Internal Revenue Service
(IRS) than had been withheld from his paycheck.
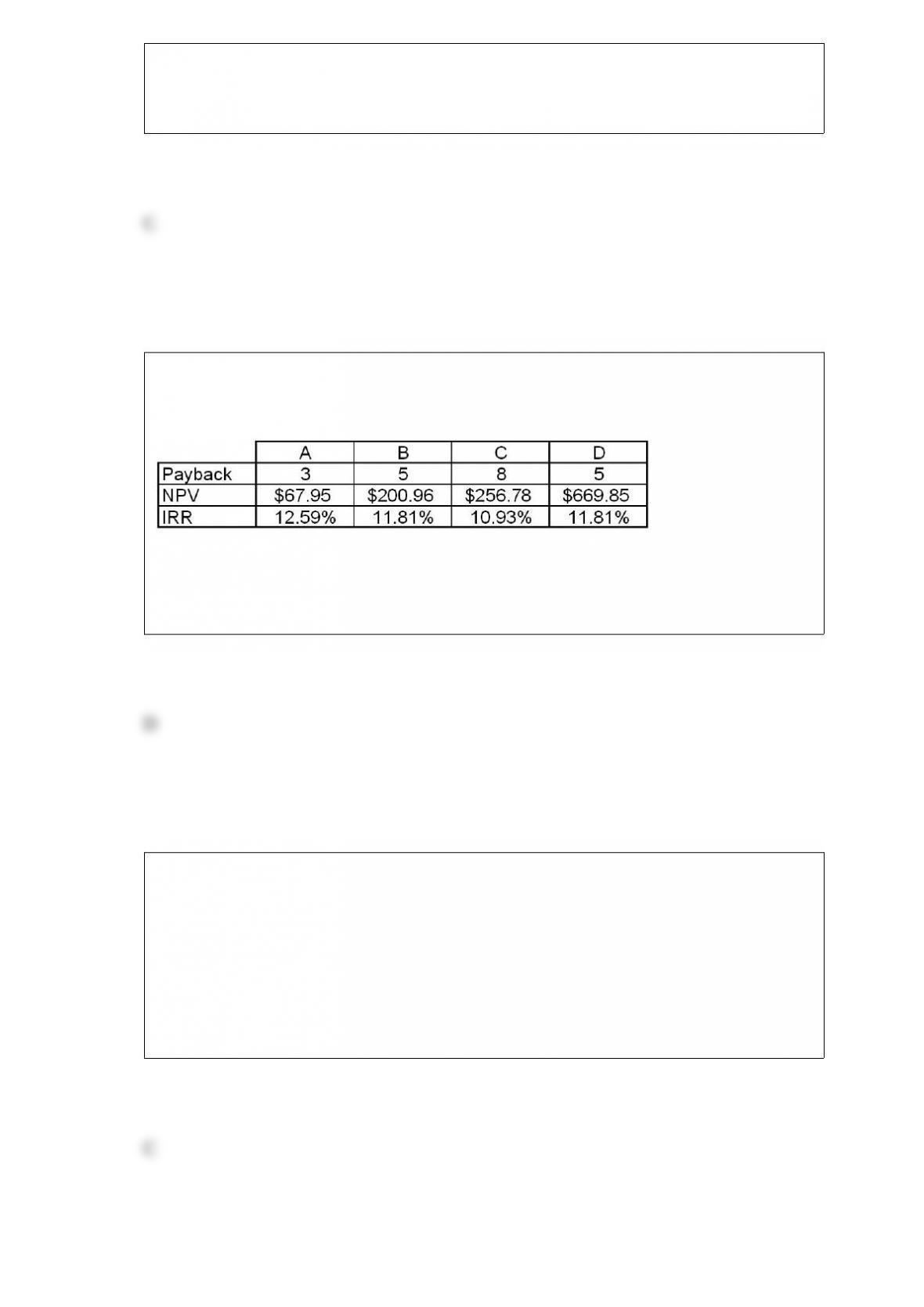
Identify the type of fraud scheme may have happened as described. Describe controls
you would implement to address the fraud risk, and label each control as preventive or
detective.
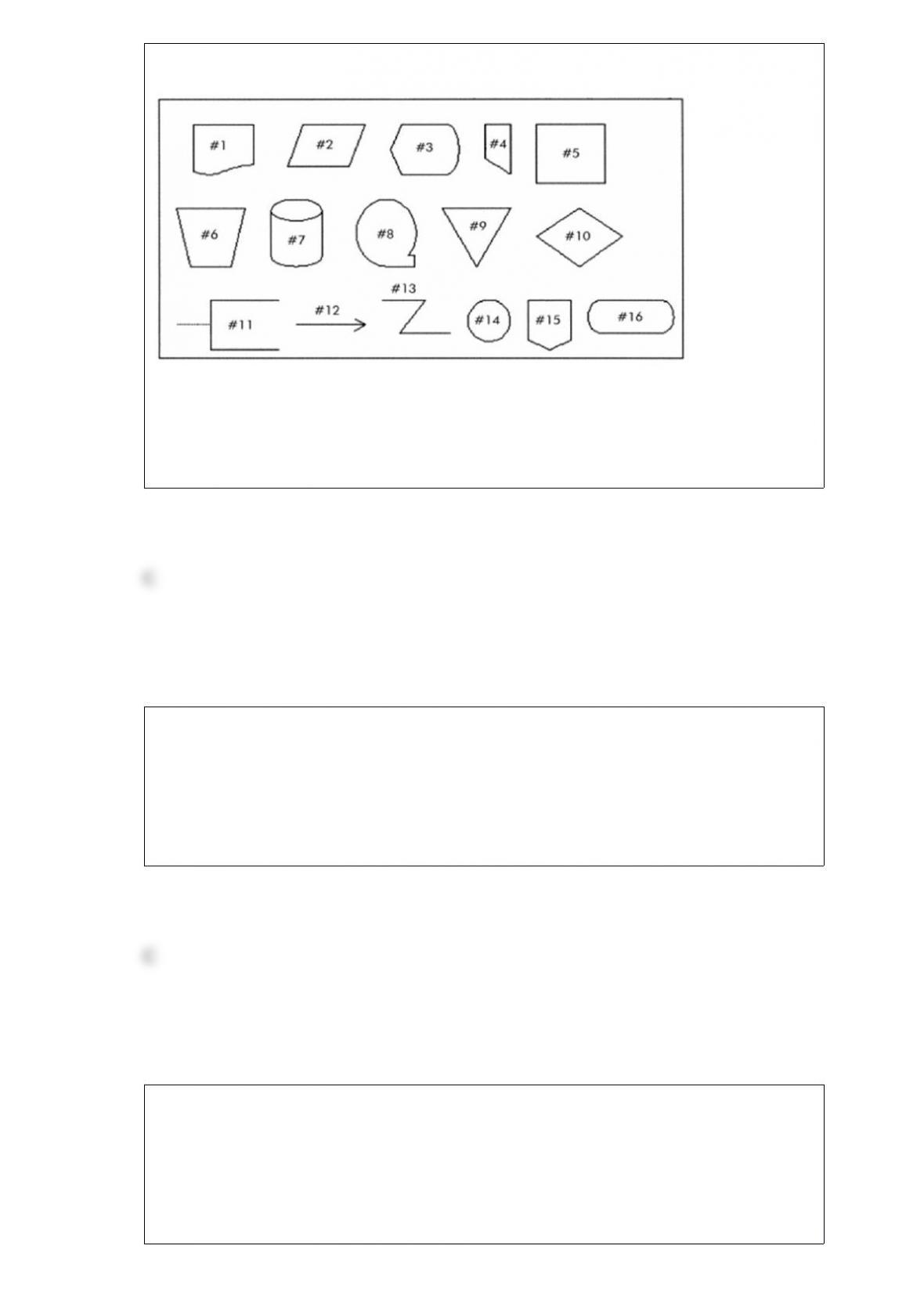
Describe the data processing cycle used to process transactions, including how data is
input, stored, and processed and how information is output.