CompTIA Network+ N10-007 Cert Guide
Chapter 12 Network Security
1) What are the three primary goals of network security?
A) Integrity, confidentiality, availability
B) Reliability, classified, accessibility
C) Integrated, restricted, obtainable
D) Veracity, dependability, unrestricted
2) DES (Data Encryption Standard) is the newest and strongest encrypted algorithm available
today.
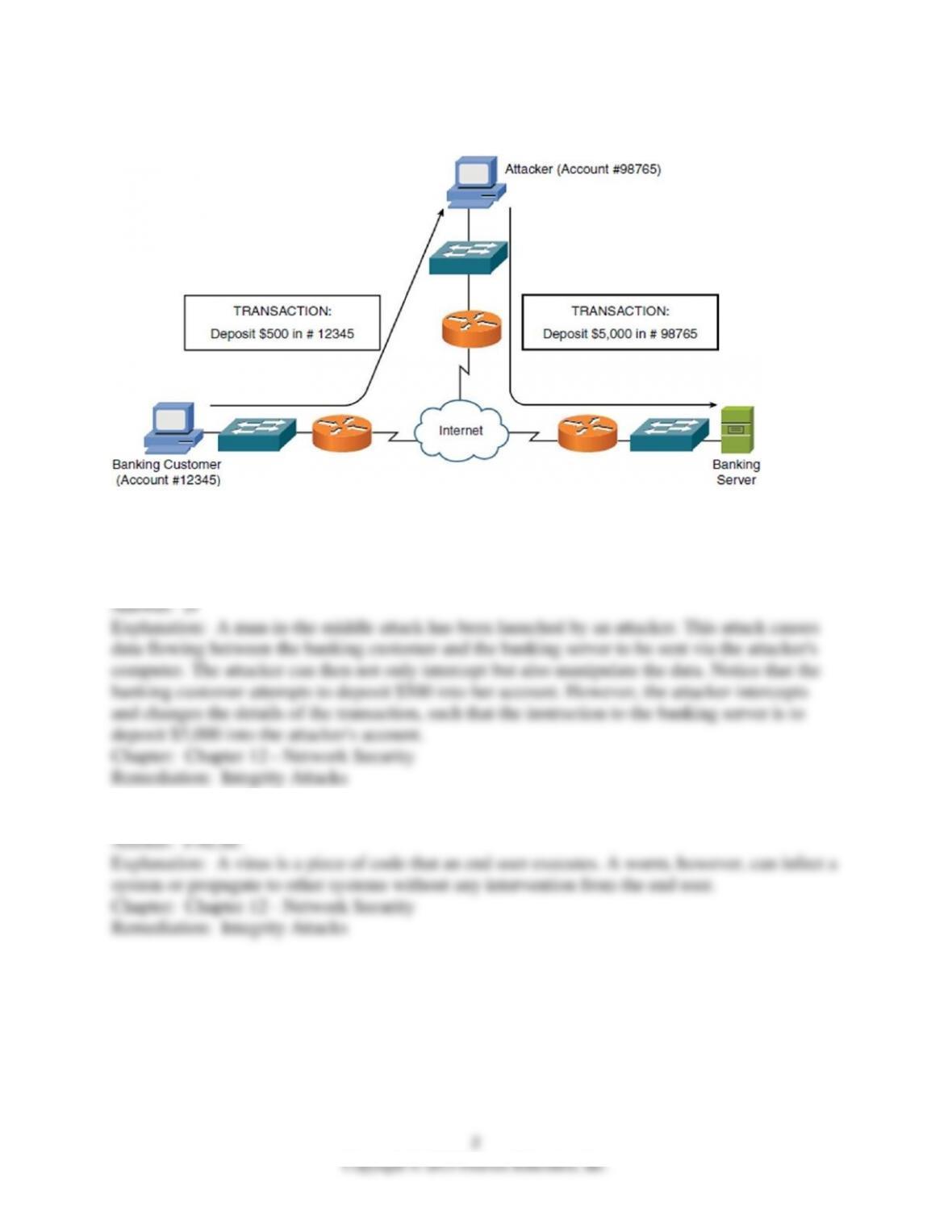
3) Which of the following is not an example of an integrity violation?
A) Modifying the appearance of a corporate website
B) Intercepting and altering an e-commerce transaction
C) Sending improperly formatted data to a networked device, resulting in an unhandled
exception error
D) Modifying financial records that are stored electronically